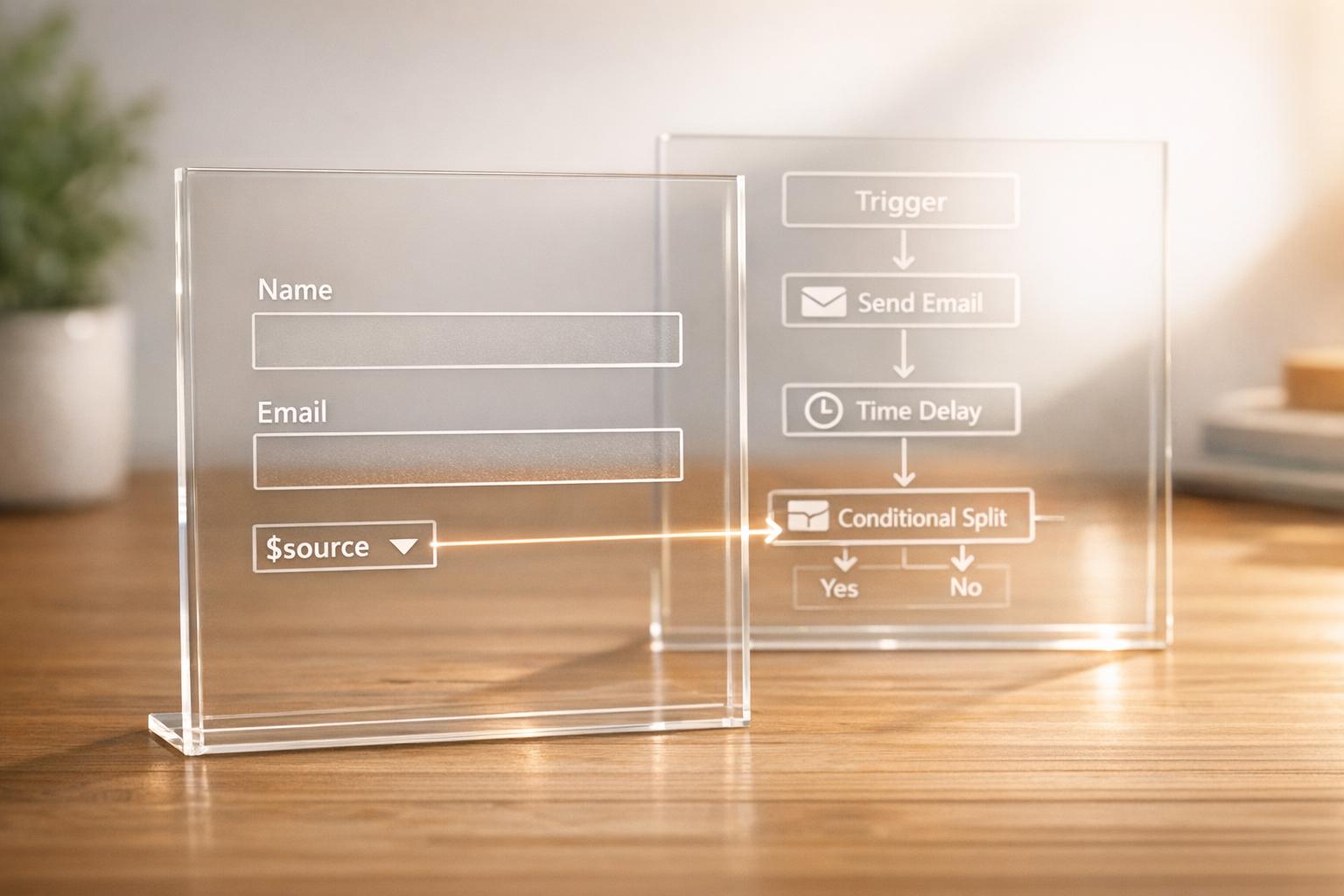
How Authentication Protocols Handle Third-Party Cookies

The shift away from third-party cookies is reshaping how websites manage user authentication. These cookies, historically used for features like single sign-on (SSO) and cross-domain sessions, are being phased out due to privacy concerns and regulations like GDPR and CCPA. Major browsers like Safari, Firefox, and Chrome now block or limit third-party cookies, forcing businesses to rethink their authentication systems.
Key updates include:
- Challenges: Without third-party cookies, users may face repeated logins, and security measures like fraud detection need new methods.
- Modern Solutions:
- PKCE (Proof Key for Code Exchange): A secure OAuth flow that avoids cookies.
- JWTs (JSON Web Tokens): Self-contained tokens for secure, cookieless authentication.
- Browser Privacy Features: Tools like partitioned cookies and APIs (e.g., Trust Tokens) ensure privacy while maintaining functionality.
- Alternatives:
- First-Party Data: Using email addresses or account IDs for identity resolution.
- Distributed IDs: Hashed emails or device fingerprinting for cross-platform recognition.
- Privacy-Focused Tech: Partitioned storage, cryptographic hashing, and consent-driven tracking.
To stay compliant and user-friendly, businesses must adopt cookie-free authentication protocols, prioritize user privacy, and leverage new tools that balance security and convenience.
Develop identity solutions without third-party cookies
How Authentication Used Third-Party Cookies
Authentication systems have long leaned on third-party cookies to enable cross-domain sign-on. While this approach simplified user experiences, it also introduced significant security and privacy risks. Below, we’ll explore how these cookies were used in session management and the challenges they created.
Session Management and Cross-Domain Authentication
Third-party cookies were the backbone of cross-domain authentication. For example, when you logged into Google and seamlessly accessed YouTube without signing in again, third-party cookies made that possible. They enabled single sign-on (SSO), allowing users to move between services without repeated logins.
Here’s how it worked: when you logged into a company’s main portal, the authentication server would generate a session cookie. Partner applications could then recognize this cookie, granting you access without requiring additional logins. This streamlined experience was particularly valuable for enterprises, where employees needed to switch between internal tools, vendor platforms, and cloud services.
While this method reduced friction, it also came with serious trade-offs in terms of security and privacy.
Security and Privacy Risks of Legacy Methods
The reliance on third-party cookies opened the door to a variety of risks, including cross-site tracking, session hijacking, and persistent tracking mechanisms like zombie cookies.
1. Cross-Site Tracking and Profiling
Authentication cookies were often used to track users across websites, building detailed profiles of their browsing habits, interests, and personal data - usually without their knowledge or consent. This lack of transparency left most users unaware that their online activity was being monitored. Worse, there were few tools to help users understand or control how their data was being collected.
2. Session Hijacking
Session cookies, which acted as authentication tokens, became prime targets for attackers. If stolen, these cookies allowed cybercriminals to bypass login screens entirely, impersonating users to send messages, make purchases, or access sensitive information.
3. XSS and CSRF Attacks
Authentication cookies were also vulnerable to cross-site scripting (XSS) and cross-site request forgery (CSRF) attacks. Malicious scripts could steal session tokens, while attackers could exploit cookies to forge legitimate-looking requests. This enabled unauthorized actions like transferring funds or changing account settings without the user’s consent.
4. Persistent Tracking with Zombie Cookies
Zombie cookies added another layer of complexity. Even after users deleted them, these cookies could reappear from backup copies stored in multiple locations. Their persistence made it nearly impossible for users to escape tracking, as they continued to link browsing habits and user IDs for extensive data collection.
The convenience of third-party cookies came at the cost of security and privacy. As browsers began blocking these cookies and privacy regulations tightened, businesses were forced to rethink their authentication methods. This shift has driven the adoption of modern solutions designed to better protect user data while maintaining a seamless experience.
Current Authentication Protocols for a Cookieless World
As the digital landscape moves away from cookie-based systems, modern authentication protocols are stepping up to provide more secure and user-friendly alternatives. These updated methods not only work around cookie restrictions but also enhance security and give users more control over their personal data.
Authorization Code Flow with PKCE
Proof Key for Code Exchange (PKCE) has become a go-to solution for secure authentication in single-page applications and mobile apps. Originally created to bolster OAuth flows for public clients, PKCE eliminates the reliance on third-party cookies while improving security.
Here’s how it works: PKCE generates two key components - a code verifier and a code challenge. The verifier stays on the client side, while the challenge is sent to the authorization server during login. Once the user is authenticated, the server issues an authorization code. The application then exchanges this code for tokens by presenting the original verifier.
This method ensures that the authorization code can’t be intercepted, as the verifier is unique to each session and never leaves the client. The entire process relies on secure redirects and API calls, bypassing the need for cross-domain cookies. Many major identity providers now support PKCE, making it a cornerstone of modern authentication systems.
By enabling token-based authentication, PKCE offers a seamless transition away from cookie-dependent systems.
Token-Based Authentication with JWTs
JSON Web Tokens (JWTs) are another key player in the shift to cookieless authentication. Unlike traditional session cookies, which require server-side storage, JWTs are self-contained tokens that don’t rely on cross-domain sharing.
Each JWT is made up of three parts: a header, a payload, and a signature. This structure allows applications to verify the token’s authenticity without needing to contact the original authentication server. This makes JWTs especially useful for distributed systems like microservices and APIs.
In cookieless setups, JWTs eliminate the need for cross-domain cookies. Typically, they’re paired with short-lived access tokens and refresh tokens to minimize security risks. When an access token expires, the application uses the refresh token to request a new one, keeping the user experience smooth while maintaining security.
Many platforms now use JWTs to combine strong security with efficient, cookieless authentication.
Browser Privacy Features and Their Role
Modern browsers are reshaping how authentication works by introducing privacy-focused features that reduce the need for third-party cookies while safeguarding user data.
Partitioned cookies, for instance, allow cookies to function across domains but isolate them by the top-level domain. This prevents cross-site tracking while retaining the benefits of cookie-based authentication. Some browsers now support cookies in isolated storage contexts, ensuring privacy without losing functionality.
New APIs are also stepping in to replace traditional tracking methods. The Trust Tokens API, for example, lets websites evaluate a user’s trustworthiness across domains without exposing personal information. Similarly, interest-based APIs provide useful signals without revealing detailed browsing histories.
Another innovation is the Storage Access API, which introduces a permission-based model for cross-site data sharing. With this API, applications can request user consent to access data from another site, making single sign-on scenarios possible while keeping users in control of their information.
Browser vendors are also exploring experimental features like enhanced tracking protection and limiting identifying information. These developments are pushing authentication providers to adopt more transparent practices, focusing on explicit user permissions and clear communication about data use. This shift prioritizes user control and privacy, signaling a new era for authentication protocols in a cookieless world.
sbb-itb-5f36581
Alternatives to Third-Party Cookies for Identity Resolution
As businesses step away from third-party cookies, finding reliable ways to identify and authenticate users across various touchpoints has become essential. New methods are emerging to address this need, each offering ways to maintain secure identity resolution while prioritizing user privacy. These approaches align with today's shift toward privacy-conscious authentication.
First-Party Data and Permanent User Identifiers
First-party data has become the backbone of identity resolution in a cookieless world. Unlike third-party cookies, which track users across multiple sites, first-party data is gathered directly from user interactions on your platform, making it more dependable and privacy-friendly.
Durable identifiers like email addresses, account numbers, and phone numbers play a key role here. For example, when users sign up for accounts or subscribe to services, their email addresses provide a consistent way to recognize them across devices and sessions. This method works well because users willingly share this information, fostering trust and consent.
Login IDs and account numbers offer similar benefits. Once users create accounts, these identifiers remain constant, unaffected by cookie restrictions or browser settings. Many authentication systems are now shifting toward account-based identification, which enhances both user recognition and security.
Phone numbers are also gaining popularity, particularly for businesses that prioritize mobile users. Since two-factor authentication already relies on phone numbers, they naturally lend themselves to identity resolution. However, phone numbers can change more often than email addresses, so this approach requires thoughtful implementation.
The durability of first-party identifiers is a major advantage. While cookies can be blocked or deleted, users typically retain the same email address or account credentials for years. This consistency allows businesses to build accurate user profiles and deliver tailored experiences without depending on less reliable tracking methods.
Distributed ID Systems and Universal IDs
Distributed ID systems offer an alternative to cookie-based tracking by using identifiers that don't rely on cookies. One example is hashed email systems, which strike a balance between functionality and privacy. These systems convert email addresses into encrypted hashes, enabling cross-platform recognition without revealing the original email address.
Here's how it works: cryptographic algorithms transform email addresses into consistent, irreversible hashes. When a user visits multiple websites that participate in the same hashed email system, the matching hash allows the sites to recognize the user - without ever exposing their actual email.
Device fingerprinting is another method for identity resolution. This technique creates a unique signature by analyzing device characteristics like screen resolution, browser version, and hardware details. Unlike cookies, device fingerprints persist across sessions and can't be easily erased. However, this method has raised privacy concerns and is increasingly targeted by browser countermeasures, making its long-term reliability uncertain.
Probabilistic matching offers a different approach. It combines various data points - such as IP addresses, browsing behaviors, and device details - to identify users with statistical confidence. While not as precise as deterministic methods like email hashing, probabilistic systems can still achieve high accuracy.
Privacy-Focused Technologies
While identity resolution methods like deterministic and probabilistic matching are effective, privacy-focused technologies ensure they meet modern data protection standards.
Partitioned storage is one such technology. It isolates data by top-level domain, preventing cross-site tracking while still supporting features like single sign-on. For instance, when a user logs into a service, their authentication data remains accessible within the same organization’s subdomains but stays isolated from unrelated third-party sites. This strikes a balance between usability and privacy.
Cryptographic hashing takes privacy protection further by using advanced techniques like differential privacy and homomorphic encryption. These methods allow data to be verified without exposing sensitive information in plain text.
Consent-driven tracking gives users control over how their identity is managed. Instead of relying on invisible tracking, these systems ask users for explicit permission to maintain their identity across sessions and sites. Users can choose their preferred balance between convenience and privacy. Modern consent management platforms make this process seamless, remembering user preferences and applying them consistently across services.
The most effective privacy-focused strategies often combine multiple technologies. For example, a business might use first-party email identifiers as the primary method, rely on partitioned storage for users without accounts, and apply cryptographic techniques to secure data during transmission and storage.
Best Practices for Authentication Without Third-Party Cookies
Moving away from third-party cookies calls for a thoughtful approach that balances security, user experience, and privacy compliance. Businesses must adopt modern authentication systems that provide seamless experiences while respecting user privacy.
Transitioning to Cookieless Authentication
To adapt to cookieless authentication flows, it's essential to leverage modern protocols and tools that ensure security and usability.
- Authorization Code Flow with PKCE: This method generates unique code challenges for each login, eliminating the need for third-party cookies.
- JSON Web Tokens (JWTs): Use these to securely carry authentication data without relying on cross-domain cookies.
- Refresh Token Rotation: Regularly rotate refresh tokens to minimize the risk of token hijacking. This ensures secure and efficient authentication processes.
- Single Sign-On (SSO) Without Third-Party Cookies: Achieve SSO by using same-site cookies on your primary domain, combined with secure redirects to verify identities across subdomains.
- SessionStorage or localStorage: Where appropriate, use these storage options for temporary data, avoiding cookies for sensitive information.
Ensuring Privacy Compliance and Transparency
Privacy regulations like GDPR and CCPA require businesses to prioritize user consent and data minimization in their authentication workflows.
- Granular Consent: Clearly explain what user data is collected during login and how long it's retained. Offer simple, easy-to-understand options for users to approve or decline different types of data processing.
- Consent Management Platforms: Integrate these tools into your authentication flows to present consent options upfront, such as during account creation. Avoid burying consent details in lengthy terms of service, and use intuitive toggles for users to control how their data is used (e.g., for analytics or marketing).
- Data Minimization: Collect only the essentials - such as email addresses, passwords, and basic profile information. Avoid requesting unnecessary details like phone numbers unless they are critical for your service.
- Audit Trails: Maintain detailed logs of authentication events, such as login attempts and password changes. These logs support regulatory compliance and provide valuable security insights.
- Transparent Privacy Policies: Clearly outline your authentication methods, including whether device fingerprinting is used, how long login data is stored, and what happens to user information after account deletion. Regularly update your privacy policy to reflect any changes in your authentication practices.
Using Reform to Enhance Authentication Workflows
Reform offers tools to optimize authentication processes, ensuring security and usability in a cookieless environment.
- Email Validation: Reform verifies email addresses in real-time during account creation, checking syntax, domain validity, and mailbox existence. This prevents users from registering with invalid or temporary emails, streamlining future authentication.
- Multi-Step Authentication Forms: Reform's conditional logic guides users through secure registration processes. For instance, business accounts might require additional verification steps, while individual users experience a simpler flow.
- CRM Integration: Automatically sync authenticated user data with platforms like Salesforce or HubSpot. This eliminates manual data entry, reduces errors, and creates unified customer profiles without relying on third-party cookies.
- Real-Time Analytics: Reform provides insights into where users face challenges during registration. By identifying friction points, you can adjust authentication processes to improve completion rates while maintaining security.
- Spam Prevention: Reform's built-in security measures detect and block suspicious activity, such as bot-generated registrations, ensuring your database remains secure and free of fake accounts.
- Accessibility Features: Reform ensures authentication forms are inclusive, supporting screen readers, keyboard navigation, and clear error messages. This approach creates secure, user-friendly experiences for all individuals.
Conclusion: Preparing for a Cookieless Future in Authentication
The move away from third-party cookies marks a major shift in how businesses handle user authentication. This isn't just about meeting legal requirements - it’s about creating safer, more transparent, and user-focused authentication systems that will shape the digital world moving forward.
Modern solutions like PKCE and JWTs provide secure authentication without relying on cross-domain cookies, all while aligning with privacy regulations such as GDPR, CCPA, and other emerging laws.
The businesses that succeed in this new era will be those that embrace first-party data strategies and invest in cookieless authentication systems. This involves ensuring clear consent management, maintaining honest privacy policies, and designing authentication processes that remain smooth and user-friendly, even as the technical landscape changes. Taking these steps now ensures a seamless transition into a privacy-first digital future.
Privacy compliance has evolved from being a mandate to a competitive edge. Companies that integrate privacy-first principles into their authentication systems will not only meet legal standards but also strengthen customer trust.
The tools to make this transition are already available. Businesses can implement real-time validation, optimize multi-step authentication processes, and build systems that perform effectively without third-party cookies. The time to act is now.
As the digital ecosystem continues to evolve, authentication will naturally shift toward being privacy-first by design. Companies that adapt to this reality today will be better equipped to navigate future privacy regulations and meet the growing expectations of their users. The cookieless future isn’t a hurdle - it’s an opportunity to create more secure and trustworthy authentication experiences.
FAQs
How do authentication protocols like PKCE and JWTs enhance security without using third-party cookies?
Modern authentication protocols like PKCE (Proof Key for Code Exchange) and JWTs (JSON Web Tokens) enhance security by removing the need for third-party cookies. PKCE boosts the OAuth authorization process by introducing a unique code verifier, which blocks authorization code interception attacks. This makes it especially useful for securing public clients, such as mobile apps or single-page applications.
Meanwhile, JWTs rely on cryptographic signatures and short expiration periods to provide secure, tamper-resistant authentication. By enabling decentralized, token-based authentication, JWTs reduce the need for server-side session storage and lower the risks associated with cookies. These protocols are particularly well-suited for modern web and mobile applications, especially in scenarios where third-party cookies are disabled or unavailable.
How can businesses shift to authentication systems that don’t rely on third-party cookies while protecting user privacy?
To navigate the shift away from third-party cookies, businesses can explore token-based authentication methods like JSON Web Tokens (JWT). These tokens provide a more secure way to handle session data without relying on cookies, offering better privacy for users.
Another option is to implement privacy-preserving identifiers, such as browser-based alternative IDs. These function similarly to cookies but align with stricter privacy regulations. On top of that, businesses can focus on gathering first-party data while being upfront with users about how their information is used. Clear and transparent consent processes go a long way in building and maintaining trust.
By adopting these strategies, companies can develop secure, privacy-focused systems that align with today's cookie restrictions.
How do technologies like partitioned storage and cryptographic hashing protect user privacy while supporting identity resolution?
Technologies like partitioned storage and cryptographic hashing offer a smart way to safeguard user privacy while ensuring accurate identity resolution.
Partitioned storage works by dividing data into separate, secure sections. This setup minimizes the chances of large-scale data breaches and prevents anyone from accessing complete user profiles without proper authorization. On the other hand, cryptographic hashing transforms sensitive information into unique, irreversible codes. This means systems can match identities without ever revealing the original data.
Together, these techniques help businesses protect user privacy while reliably resolving identities, all while staying aligned with today’s privacy regulations.
Related Blog Posts
Get new content delivered straight to your inbox

The Response
Updates on the Reform platform, insights on optimizing conversion rates, and tips to craft forms that convert.
Drive real results with form optimizations
Tested across hundreds of experiments, our strategies deliver a 215% lift in qualified leads for B2B and SaaS companies.


.webp)