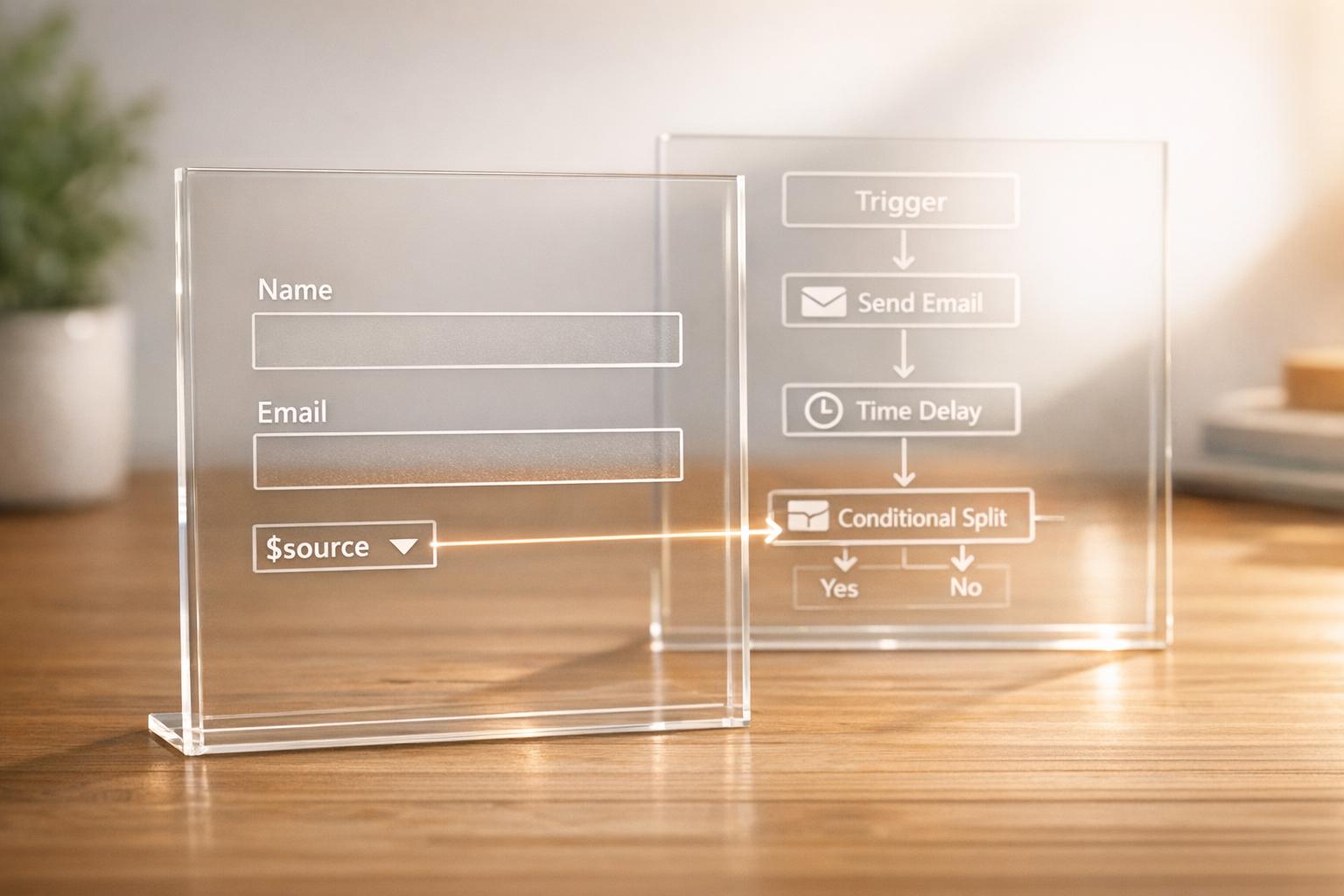
OAuth 2.0 Authorization Code Flow Explained

OAuth 2.0 Authorization Code Flow is a secure way for apps to access user data from third-party platforms without sharing passwords. It uses a token system to ensure safety and user control. Here's a quick breakdown:
- What It Does: Lets apps request limited access to user data via tokens, not passwords.
- Why It’s Secure: Uses a two-step process to exchange an authorization code for tokens, keeping sensitive data safe from exposure.
- Who It’s For: Ideal for server-side apps, web apps with backends, and industries like finance or healthcare where data security is critical.
- How It Works:
- User logs in and approves access via an authorization server.
- App receives a temporary authorization code.
- App exchanges the code for access and refresh tokens securely.
Key security features include Proof Key for Code Exchange (PKCE) to prevent code interception and strict token management practices. Proper implementation reduces risks, ensures compliance, and builds user trust.
Wrapping up OAuth 2.0 with the Authorization Code grant type
How the Authorization Code Flow Works
The Authorization Code Flow follows a series of interactions between your app, the user, and the authorization server. Knowing how each step works is key to implementing this flow correctly and resolving any issues.
Step 1: User Authentication and Authorization Grant
It all starts when a user tries to access a protected feature in your app. At this point, your app redirects them to an authorization server (like Google, Microsoft, or GitHub). The redirect URL includes important details like your client ID, redirect URI, scope, and a state parameter to help prevent CSRF attacks.
The user logs in on the authorization server using their credentials. After logging in, they see a consent screen showing what data your app wants to access. This step is all about transparency, letting users know exactly what permissions they’re granting. They can either approve or deny the request.
If the user approves, the authorization server generates a temporary authorization code. This code is short-lived (usually valid for 10 minutes or less) and can only be used once. The server then redirects the user back to your app using the redirect URI you provided, attaching the authorization code as a query parameter.
Your app now has the authorization code and can securely exchange it for tokens.
Step 2: Authorization Code Exchange
Once your app gets the authorization code, the next step is to exchange it for tokens. This happens securely through a back-channel request to the token endpoint, which ensures the process is hidden from the user's browser and much safer than client-side exchanges.
The token request includes:
- The authorization code
- Your client ID
- Your client secret (a private key that proves your app’s identity)
- The redirect URI (for verification)
- A grant type of "authorization_code"
The client secret is a critical piece here - it ensures only trusted server-side applications can make this request.
The authorization server then validates all the details. It checks that:
- The authorization code is valid and hasn’t expired.
- The client ID and secret match a registered application.
- The redirect URI matches the one registered during setup.
If everything checks out, the server responds with an access token and often a refresh token.
The access token allows your app to make API requests on behalf of the user. The refresh token lets you get new access tokens when the current ones expire, so users don’t have to go through the entire process again.
Step 3: Access Token Usage
With the access token in hand, your app can now send authenticated requests to the resource server (which might be the same as the authorization server or a separate service). Each API request includes the access token in the Authorization header using this format: Authorization: Bearer your_access_token_here.
The resource server validates the token with every request, ensuring it’s still valid, hasn’t expired, and has the right scope for the requested resource. If the token checks out, the server provides the requested data. If it’s expired, your app can use the refresh token to get a new access token without requiring the user to log in again.
This token-based system means your app never deals with user passwords, and tokens are designed to provide access only to the specific resources the user approved. If a token gets compromised, its limited scope and expiration time significantly reduce the risk.
For apps dealing with sensitive data or requiring long-term access, it’s crucial to handle tokens securely. Store them encrypted in your database, refresh tokens automatically before they expire, and be ready to handle situations where refresh tokens become invalid, requiring users to reauthorize your app.
Benefits and Security Features
The Authorization Code Flow offers strong authentication measures while ensuring a seamless user experience for web applications. Let’s break down its key advantages.
Main Benefits of the Flow
One major benefit is better credential security. With this flow, your app doesn’t handle user passwords directly, which lowers the risk of sensitive data being exposed during breaches. Instead, users input their credentials on a trusted authorization server, keeping their passwords out of your app’s reach.
Another highlight is the refresh token feature. Refresh tokens allow apps to maintain access to user data without requiring repeated logins. This ensures uninterrupted functionality even after access tokens expire.
Finally, the flow’s scalability and flexibility stand out. It works seamlessly across various platforms, including web, single-page, mobile, and desktop applications. This makes it easier to implement a consistent authentication system across different environments.
Implementation Best Practices
Setting up the Authorization Code Flow requires close attention to both security and technical details. Following these guidelines can help you create a secure and efficient authentication system that safeguards user data while ensuring smooth operation.
Technical Requirements
Here are some key security measures to implement:
- Always use HTTPS for communications with the authorization server. This encrypted connection protects sensitive data like authorization codes and tokens from being intercepted.
- For confidential clients, store client secrets securely on the server and never expose them in client-side code. Additionally, pre-register all HTTPS redirect URIs to avoid misuse. Avoid using wildcard patterns in redirect URIs, as they can introduce vulnerabilities.
- When working with public clients, such as mobile apps or single-page applications, implement Proof Key for Code Exchange (PKCE). PKCE adds an extra layer of security, ensuring that only the original client can complete the authorization process.
Implementation Tips
- Use trusted authentication libraries. These libraries handle complex security scenarios and edge cases, reducing the risk of errors in custom implementations.
- Set short lifespans for access tokens, typically between 15 minutes and 1 hour, while assigning refresh tokens longer - but still finite - expiration periods. This approach balances security with usability.
- Implement secure storage and revocation mechanisms for tokens. Use encrypted storage for tokens and provide users with options to revoke access, such as logging out from all devices and invalidating refresh tokens.
- Design user-friendly error handling. When authentication fails, display clear and simple error messages without revealing technical details that could be exploited by attackers.
Integration with Platforms like Reform
By adhering to these practices, integrating OAuth 2.0 with platforms like Reform becomes much easier. This integration supports secure workflows that connect user authentication with data collection and enrichment.
For example, when OAuth 2.0 is integrated with form builders like Reform, you can securely pre-fill form fields with authenticated user data. This ensures both efficiency and data protection during the submission process.
Reform's API integrations also work seamlessly with OAuth 2.0-protected endpoints. This allows you to send form submissions directly to CRMs, marketing platforms, or other third-party services over authenticated connections. Sensitive data is transferred securely, keeping user credentials safe.
This setup is especially useful for lead enrichment workflows. After users authenticate, Reform can pull additional profile data from authorized APIs to enhance form submissions. This creates more detailed lead profiles while maintaining strict data security and user privacy.
For businesses utilizing Reform's conditional routing features, OAuth 2.0 integration enables customized form experiences. Based on user roles or permissions, you can display specific form sections or redirect users to tailored thank-you pages. This personalized approach enhances user engagement while keeping authentication secure.
sbb-itb-5f36581
Common Issues and Solutions
Implementing OAuth 2.0 Authorization Code Flow can sometimes feel like navigating a maze. Developers often encounter specific challenges that can disrupt the authentication process. Recognizing these issues and knowing how to address them can save time and ensure your system remains secure.
Invalid Redirect URIs
One of the most common stumbling blocks is redirect URI mismatches. This happens when the redirect URI in your authorization request doesn’t perfectly match the one registered with the authorization server. Even small differences - like a missing trailing slash or a mismatch between http and https - can cause errors. For example, https://yourapp.com/callback and http://localhost:3000/callback are treated as entirely different URIs.
To fix this, double-check your registered URIs in your OAuth provider’s developer console. Make sure every element - protocol, domain, port, path, and even the trailing slash - matches exactly. If you’re working in multiple environments, like development and production, register separate URIs for each. For instance, use http://localhost:3000/callback during development and https://yourapp.com/callback for production.
When using platforms like Reform, remember to account for both staging and production environments. If you’re processing authenticated user data with Reform’s webhook endpoints, make sure you’ve registered all relevant URIs.
Once your redirect URIs are aligned, you’ll be in a better position to ensure smooth token exchanges.
Token Exchange Failures
Token exchange errors are another frequent issue. These occur when your app fails to exchange the authorization code for tokens. Common causes include expired authorization codes, incorrect client credentials, or network connectivity problems.
Authorization codes often have short lifespans, typically between 30 seconds and 10 minutes. If users abandon the process or there’s a delay - such as network lag - the code might expire before it’s exchanged. Additionally, mismatched client credentials (e.g., using development credentials in production) can block the token exchange.
Network-related problems, like firewalls or DNS issues, can also interfere with reaching the token endpoint.
To troubleshoot, implement detailed logging. Record authorization codes (without sensitive secrets) and HTTP responses to identify where things go wrong. Also, check your system clocks to ensure time synchronization, as mismatched clocks can cause token validation failures.
For apps integrating with Reform’s API, token exchange errors can disrupt the flow of data to CRMs or marketing tools. To mitigate this, add retry mechanisms with exponential backoff to handle temporary network hiccups. Just make sure to respect the rate limits set by the authorization server.
Managing tokens properly also helps avoid user frustration with consent prompts, which we’ll tackle next.
Consent Prompt Issues
Nothing irritates users like being asked to grant permissions repeatedly. Repeated consent prompts often point to scope inconsistencies or poor token management. This happens when your app requests different permissions than what was previously authorized, forcing users to re-consent.
To avoid this, be consistent with your scope requests. Decide upfront which permissions your app needs and stick to them. Avoid requesting overly broad permissions that users might hesitate to grant. For example, if you only need access to basic profile data, don’t request permissions for email or contacts unless absolutely necessary.
Session management can also play a role. If a user’s session expires in your app but remains valid with the authorization server, it can create confusing states that lead to additional consent prompts.
Here’s how to minimize these issues:
- Standardize scope requests across your app. Document required permissions and ensure every request aligns with them.
- Manage token lifecycles carefully. Store refresh tokens securely and use them to renew access tokens before they expire. This keeps users from having to reauthorize unnecessarily.
If you’re integrating with Reform for lead enrichment, plan your initial scope requests thoughtfully. Clear and consistent requests improve user trust and reduce abandonment.
Finally, monitor your consent conversion rates. If many users drop off during the authorization process, it might be a sign that your app is asking for too much or failing to explain why the permissions are needed.
Conclusion
OAuth 2.0 Authorization Code Flow has earned its place as a go-to method for secure API authentication, but its success hinges on getting the implementation right. While the protocol itself is solid, security issues often arise from missteps during deployment rather than flaws in the OAuth 2.0 framework.
To ensure a secure setup, focus on managing redirect URIs with precision, handling tokens securely, and defining permission scopes thoughtfully. These steps are critical to avoiding common vulnerabilities. Pairing these practices with features like PKCE (Proof Key for Code Exchange) strengthens your authentication flow, safeguarding both your application and user data. Additionally, implementing detailed logging can help with troubleshooting, and planning permission scopes early on prevents headaches down the road.
These measures don't just enhance security - they also make API integrations smoother for business applications. For instance, platforms like Reform simplify the integration process, especially when paired with a properly implemented OAuth flow. Reform’s API integrations can securely link user data to tools like CRMs or marketing automation systems, all while upholding high security standards.
FAQs
What makes the OAuth 2.0 Authorization Code Flow more secure than other authentication methods?
The OAuth 2.0 Authorization Code Flow boosts security by ensuring the access token stays hidden from the user's browser. This approach minimizes the chances of it being intercepted while also keeping sensitive credentials securely stored on the server, away from the client.
When combined with Proof Key for Code Exchange (PKCE), it adds an extra shield against risks such as authorization code interception and man-in-the-middle attacks. This makes it a more secure option compared to methods like the implicit flow, where tokens are exposed in the browser and face higher vulnerability.
What are the common challenges developers face with OAuth 2.0 Authorization Code Flow, and how can they address them?
Developers often face hurdles when working with OAuth 2.0 Authorization Code Flow. Common issues include security risks - like leaking client secrets, exposing authorization codes, or falling prey to CSRF attacks - and configuration mistakes, such as mismatched redirect URIs or incorrect client credentials. These problems can compromise both the security and functionality of the flow.
To tackle these challenges, consider a few key practices:
- Use PKCE (Proof Key for Code Exchange) to protect against code interception.
- Validate the state parameter to guard against CSRF attacks.
- Double-check configurations, including client IDs, secrets, and redirect URIs, to ensure they’re correct.
Adopting these strategies can help strengthen the security and dependability of your OAuth 2.0 implementation.
What is PKCE, and why is it essential for OAuth 2.0 Authorization Code Flow in mobile and public apps?
What Is PKCE?
PKCE (Proof Key for Code Exchange) is an important security measure used in the OAuth 2.0 Authorization Code Flow. It’s particularly useful for public clients, like mobile apps or single-page applications, where traditional client secret storage isn’t secure.
Here’s how it works: Instead of relying on a static client secret, the app creates a unique code verifier and a hashed code challenge during the authorization process. These two values are then exchanged with the authorization server. The server checks these values to ensure the app initiating the process is the same one completing it.
Why does this matter? PKCE helps prevent serious security threats, like authorization code interception or man-in-the-middle attacks, making OAuth flows safer and more dependable for apps that interact directly with users.
Related Blog Posts
Get new content delivered straight to your inbox

The Response
Updates on the Reform platform, insights on optimizing conversion rates, and tips to craft forms that convert.
Drive real results with form optimizations
Tested across hundreds of experiments, our strategies deliver a 215% lift in qualified leads for B2B and SaaS companies.


.webp)