Form.io API Authentication Setup Guide

Form.io API authentication ensures secure access to your forms and data. This guide covers the setup process for various authentication methods and offers tips for maintaining a secure environment. Here’s what you need to know:
- Authentication Methods: Choose from OAuth (with OpenID Connect), SAML, JWT tokens, email/password, or LDAP based on your needs.
- Setup Essentials: Gather admin access, provider configuration details (e.g., client IDs, metadata, certificates), and define user roles early.
- Security Features: Enable two-factor authentication (2FA), use reCAPTCHA to block bots, and manage API keys securely.
- Maintenance: Regularly review authentication logs, update configurations, and monitor for unusual activity.
Each method integrates with Form.io’s role-based permissions, ensuring controlled access. Follow the detailed steps for your chosen method and test configurations in a safe environment before deployment.
Form.io Developer Tutorial Part 3: Authenticating Forms and ngFormio/ngFormioHelper

Requirements and Initial Setup
Setting up your Form.io environment correctly is crucial to ensuring smooth and secure authentication processes. Here's how to get started.
Basic Requirements
First, make sure you have administrative access to your Form.io project. Since authentication settings directly influence security, this access is essential.
Your technical team should be well-versed in the authentication method you plan to use - whether that's OAuth, SAML, or JWT. Understanding these methods will help avoid misconfigurations and ensure a seamless setup.
Before diving into the configuration, confirm that Form.io is already deployed within your enterprise environment. This step is critical to avoid potential issues later. Additionally, map out the necessary API access for both users and systems to close any potential security gaps.
Form.io supports hierarchical roles and permissions, so it’s a good idea to define user access levels early. This planning will make it easier to assign the correct permissions and avoid complications down the road. Finally, gather all the tools and configuration data you'll need for your chosen authentication method.
Required Tools and Configuration Data
The tools and data you'll need depend on the authentication method you choose, but some elements are common across all methods. Start by collecting configuration details from your existing authentication provider. These typically include endpoint URLs, metadata files, and any required certificates or keys.
For OAuth and OIDC, you'll need client IDs, client secrets, and authorization server endpoints. If you're using SAML, gather identity provider metadata, certificate files, and single sign-on URLs. For JWT, make sure you have token signing keys as well as issuer and audience details.
Proper API key management is essential. Store sensitive information like client secrets and private keys in secure locations, such as environment variables or secret management systems, rather than in configuration files.
Additionally, prepare mappings between your existing user attributes and Form.io's role structure. This step ensures that users are assigned the correct permissions automatically when they authenticate.
Finally, set up a testing environment that mirrors your production setup as closely as possible. Use dedicated accounts and isolated settings to simulate realistic scenarios without risking your live systems. This approach makes troubleshooting easier and helps ensure a smooth rollout.
Authentication Setup Instructions
Follow these steps to configure your preferred authentication method.
OAuth and OpenID Connect (OIDC) Setup
OAuth and OIDC allow secure authentication through external providers like Google, Microsoft Azure, or custom authorization servers. Start by accessing the Authentication section in your Form.io admin panel and selecting OAuth/OIDC as the method.
Input the authorization server URL (e.g., https://your-provider.com/oauth2/authorize) along with the client ID and client secret obtained during your setup process. Define scopes such as openid, profile, and email to determine the user information your app can access. Ensure the redirect URI points back to your Form.io instance, typically formatted as https://your-formio-instance.com/auth/oauth/callback.
To manage user access, map roles from your identity provider to Form.io's permissions. For instance, you might link an "Administrators" group to the admin role, ensuring users are assigned the correct level of access.
Before deploying this configuration across your organization, test it with a dedicated account. Once confirmed, you can move on to setting up SAML for enterprise-level single sign-on.
SAML Authentication Setup
SAML provides a single sign-on solution for businesses with existing identity management systems. Begin by uploading your identity provider's metadata file to the SAML configuration section in Form.io.
Enter the Identity Provider (IdP) Single Sign-On URL and IdP Entity ID as specified in your IdP's documentation. Upload the X.509 certificate used by your IdP to sign SAML assertions, ensuring authentication responses are verified.
In the Form.io Service Provider (SP) settings, define the SP Entity ID to uniquely identify your instance to the IdP. Set the Assertion Consumer Service URL to Form.io's SAML endpoint, typically https://your-formio-instance.com/auth/saml/callback.
Map attributes from your IdP - such as email, firstName, lastName, and any custom fields - to Form.io's user fields. Also, ensure role or group attributes are mapped correctly to manage user permissions effectively.
Test the SAML authentication flow thoroughly, verifying that user attributes are mapped accurately and logout functions as intended. Afterward, you can proceed to configure JWT tokens for system-to-system communication.
JWT Token Authentication Setup
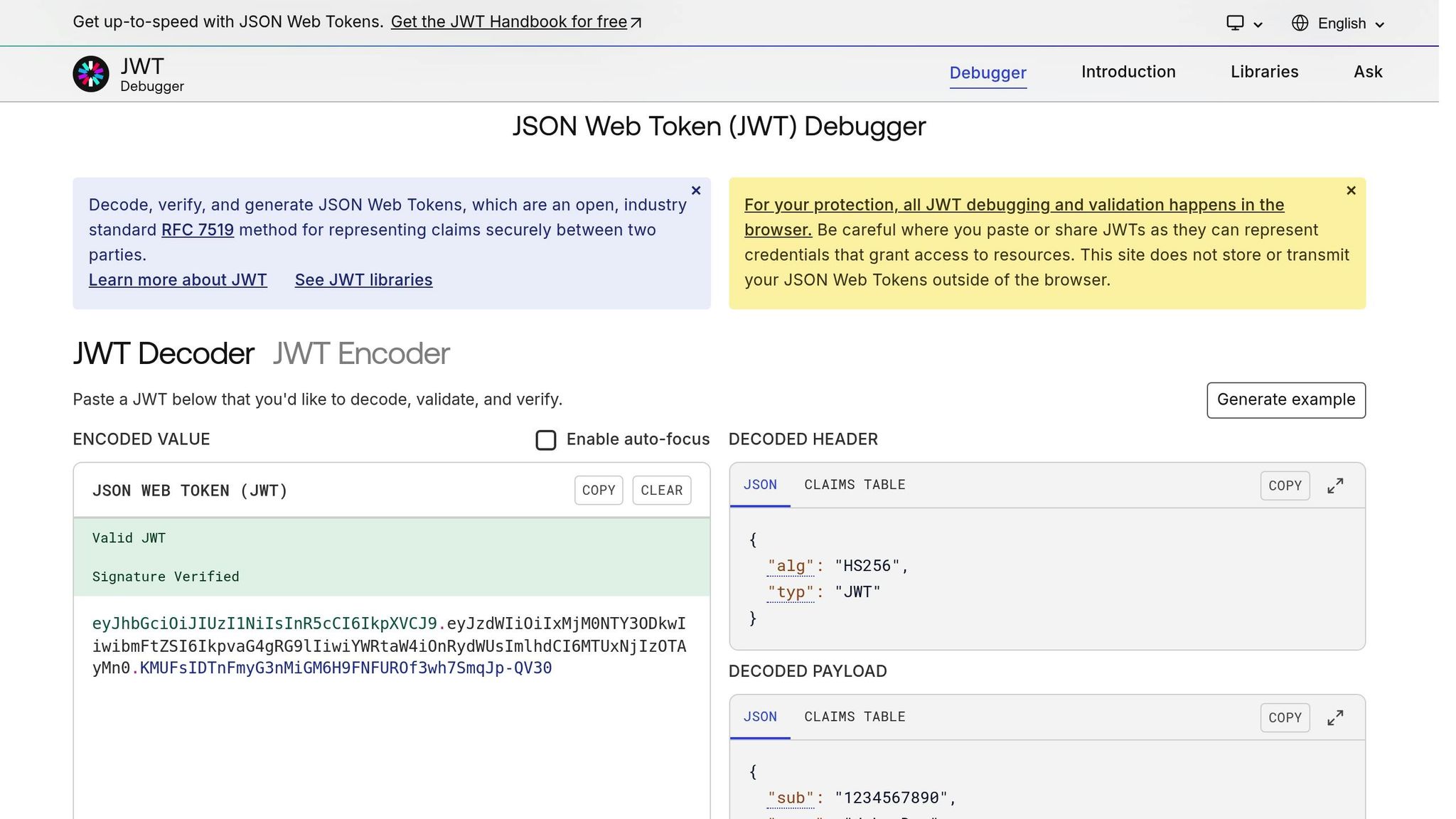
JWT tokens are ideal for programmatic API access and system-to-system communication. Configure tokens to use a secure signing algorithm and validate claims such as issuer, audience, and expiration. For detailed setup instructions and security recommendations, refer to the official Form.io API documentation.
Email/Password and LDAP Setup
Email/password authentication is a versatile option, while LDAP integration connects Form.io to your existing directory services.
For email/password authentication, set up policies for password complexity, account lockouts, and reset procedures.
When configuring LDAP, provide your directory server's hostname, port, credentials, and search base DN. Always use encrypted connections (LDAPS) where possible and limit the bind account's permissions to only what is necessary.
"Set up roles and permissions integrated with your existing authentication" - Form.io
Test scenarios like password resets and group changes to ensure users receive the correct access levels and permissions.
sbb-itb-5f36581
Security Best Practices
Securing your Form.io instance goes beyond basic authentication. It requires a layered approach to guard against common threats effectively.
Two-Factor Authentication (2FA) Setup
Two-factor authentication (2FA) adds an extra layer of security by requiring users to verify their identity with a second factor beyond just a password. This step significantly reduces the risk of unauthorized access, even if passwords are leaked or stolen.
To set up 2FA, use your identity provider (e.g., Google OAuth), which prompts users for a second verification step. This is especially important for admin and high-privilege accounts. Why? Because stolen credentials are a leading cause of data breaches - 83% of breaches in 2023 involved compromised credentials, according to the Verizon Data Breach Investigations Report. For industries like healthcare, implementing 2FA is often necessary to comply with regulations like HIPAA.
For the best results, configure 2FA with time-based one-time passwords (TOTP) through apps like Google Authenticator or Microsoft Authenticator. These apps generate codes that refresh every 30 seconds, offering greater security than SMS-based verification.
To further protect your system, address automated attacks with reCAPTCHA.
Spam Prevention with reCAPTCHA
Authentication endpoints are prime targets for bots, which can attempt thousands of username and password combinations in minutes. Google’s reCAPTCHA service blocks over 100 million spam and abuse attempts daily, making it a powerful tool against such attacks.
To integrate reCAPTCHA into your Form.io authentication forms, start by obtaining API keys from Google’s reCAPTCHA console. Then, configure the component to validate user interactions before form submission. If you opt for reCAPTCHA v3, it runs discreetly in the background, assigning risk scores to user interactions. You can set thresholds to automatically block suspicious traffic while letting legitimate users through.
It’s a good idea to include reCAPTCHA on all public-facing forms, such as login pages, registration forms, and password reset requests. This ensures bots can’t exploit any entry points into your system.
Next, let’s talk about securing API access.
API Key Management
API keys are the gateway to your Form.io instance, so managing them securely is critical. Mismanagement can expose your system to unauthorized access.
Here’s what to do:
- Generate unique API keys for each application or integration. This makes it easier to track usage and revoke access if a key is compromised.
- Store keys securely in environment variables or encrypted files. Never embed keys directly in your application code, especially in client-side JavaScript.
- Rotate keys regularly - every 90 days for high-security needs or every six months otherwise. Automated rotation minimizes the risk of compromised keys being exploited.
- Limit permissions for each key to only what’s necessary. For example, if an integration only needs to read form submissions, don’t grant it administrative access.
- Monitor usage for unusual activity, like spikes in requests or access from unexpected IP addresses. Set up alerts to flag these anomalies for your security team.
Now, let’s compare different authentication methods to help you choose the right fit for your security needs.
Authentication Methods Comparison
Here’s a quick overview of how different authentication methods stack up in terms of security, ease of use, and complexity:
| Method | Security Level | Ease of Use | Integration Complexity |
|---|---|---|---|
| OAuth/OpenID Connect | High | User-friendly SSO | Moderate to High |
| SAML | High | User-friendly SSO | High |
| JWT | Medium-High | Simple for developers | Low to Moderate |
| Email/Password/LDAP | Medium | Familiar to users | Low to Moderate |
OAuth and SAML are top-tier for security, supporting single sign-on (SSO) and integrating with enterprise identity providers. These methods often include 2FA and advanced policies but require a more complex setup.
JWT tokens strike a balance between security and simplicity. They’re especially useful for system-to-system communication since they’re stateless and don’t need server-side session storage. Just make sure tokens are signed with strong algorithms and have appropriate expiration times.
Email/password authentication is easy to implement and familiar to users, but it depends heavily on user behavior. Without strong password policies and 2FA, this method is more vulnerable to attacks.
For organizations with directory services, LDAP integration offers centralized user management. However, its security depends on using encrypted connections (LDAPS) and limiting bind account permissions.
For instance, a healthcare provider in the U.S. implemented SAML SSO with 2FA and reCAPTCHA. This combination significantly reduced unauthorized login attempts while ensuring compliance with HIPAA security standards. This example highlights how layering multiple security measures creates a stronger defense against threats while meeting regulatory requirements.
Maintenance and Troubleshooting
Keeping your API secure is not a one-and-done task - it requires consistent monitoring and upkeep. After setting up authentication, it's essential to stay vigilant and proactive to ensure long-term protection.
Monitoring Authentication Activity
Make it a habit to review authentication logs regularly. Look for any unusual patterns or unexpected access attempts that could indicate a problem. Setting up alerts for significant changes or anomalies ensures you can quickly spot and address potential issues before they escalate.
Routine Maintenance
Beyond monitoring, periodic maintenance plays a key role in strengthening security. Take time to review and update your authentication settings to make sure they remain effective and aligned with current security standards. This ongoing effort not only protects your API but also ensures a smooth and secure experience for your users.
Conclusion
Setting up authentication for the Form.io API is a straightforward process. Whether you opt for OAuth, SAML, JWT tokens, or email/password authentication, the key is choosing the method that aligns with your organization's security needs and technical setup. For detailed steps and practical tips, revisit the earlier sections of this guide.
While the initial setup is simple once the prerequisites are in place, maintaining strong security requires ongoing diligence. Practices like enabling two-factor authentication, managing API keys securely, and using tools like reCAPTCHA to prevent spam are crucial for building a solid defense.
Regular monitoring and periodic updates are essential to keep your API secure over time. With the detailed instructions and strategies provided here, you’re well-equipped to establish and maintain a secure Form.io API environment.
FAQs
What are the main differences between OAuth, SAML, and JWT authentication methods, and how can I determine the best option for my organization?
OAuth, SAML, and JWT are three popular approaches to authentication, each catering to specific needs. OAuth works well for secure delegated access, making it a go-to option for APIs and integrations with third-party applications. SAML shines in enterprise environments, particularly for Single Sign-On (SSO), allowing users to log in once and seamlessly access multiple systems. Meanwhile, JWT offers a lightweight, self-contained token format that's perfect for stateless authentication in modern web apps.
Choosing the right method depends on your requirements. If you're securing APIs or enabling third-party integrations, OAuth is often the way to go. For enterprise SSO, SAML is a strong contender. On the other hand, if you need a simple, stateless solution, JWT might be the best fit. Each method serves a distinct purpose, so aligning the choice with your specific use case is essential.
What are the best practices for securely managing API keys in my Form.io instance?
To manage your API keys securely and prevent unauthorized access, here are some essential steps to follow:
- Keep your API keys private: Never expose your keys in public repositories or hardcode them into your application. Instead, store them safely using environment variables or secure secrets management tools.
- Use role-based permissions: Assign each API key the minimum permissions it needs to perform its specific task. This limits access to sensitive data and reduces potential risks.
- Rotate keys regularly: Update your API keys on a regular schedule. This minimizes the chance of misuse if a key is ever compromised.
- Monitor usage: Actively track API activity to spot any unusual patterns or unauthorized access attempts.
For an extra layer of protection, enable IP whitelisting or other access restrictions if your system supports these features. These measures can help tighten security further.
How can I test and confirm that my Form.io API authentication setup is working correctly before going live?
To make sure your Form.io API authentication is working correctly before going live, here’s what you should do:
- Test locally: Use tools like Postman or curl to send requests to your API endpoints. Check that valid credentials grant access, while invalid ones are properly denied.
- Validate role-based access: If your API uses role-based permissions, test various user roles to confirm they can only access the resources they’re authorized for.
- Review logs: Look at your server logs to catch any errors or unusual activity during authentication attempts.
Thorough testing in these areas helps you catch and fix issues early, so your deployment goes off without a hitch.
Related Blog Posts
Get new content delivered straight to your inbox

The Response
Updates on the Reform platform, insights on optimizing conversion rates, and tips to craft forms that convert.
Drive real results with form optimizations
Tested across hundreds of experiments, our strategies deliver a 215% lift in qualified leads for B2B and SaaS companies.


.webp)








