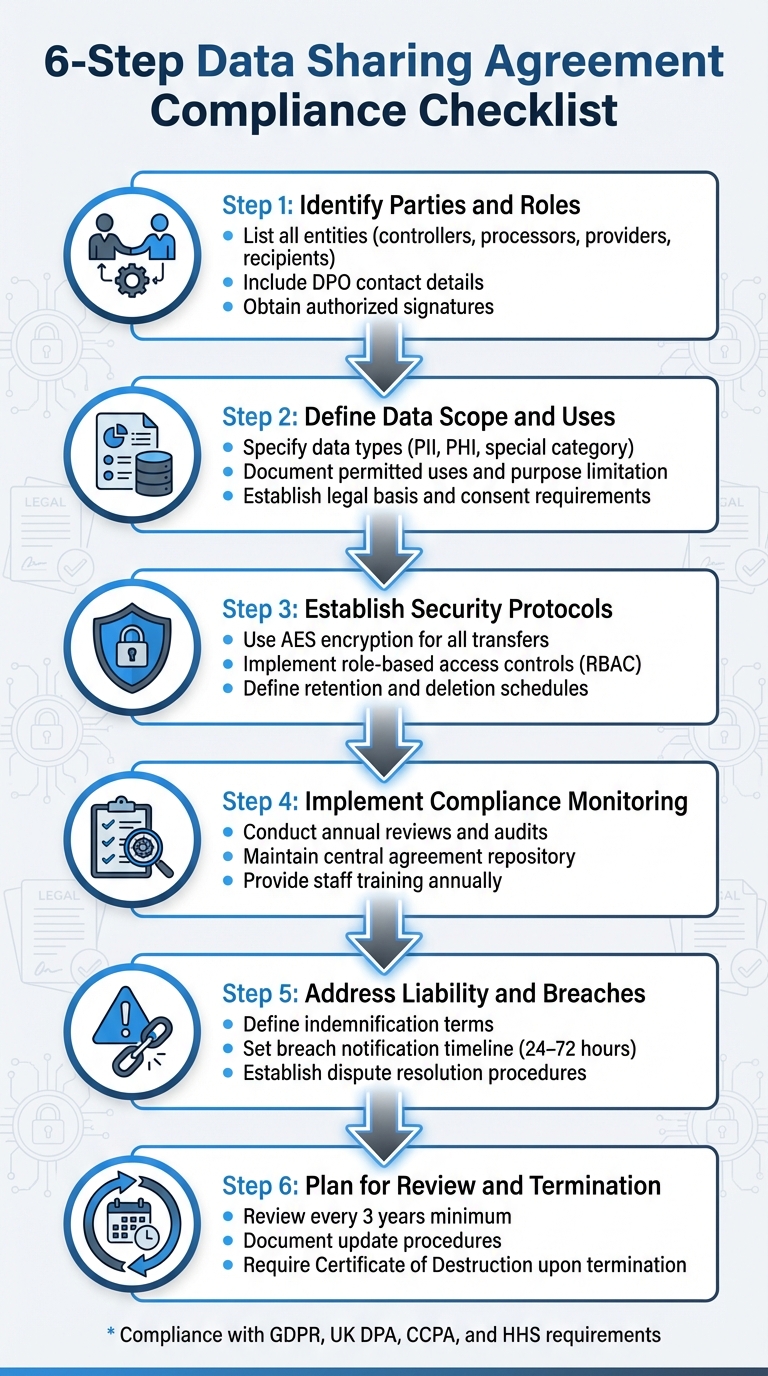
Checklist for Data Sharing Agreement Compliance

Data Sharing Agreements (DSAs) are critical for ensuring secure and lawful data exchanges between organizations. They outline responsibilities, define roles, and specify security measures to comply with regulations like GDPR, UK Data Protection Act, and CCPA. Without a proper DSA, organizations risk legal penalties, data breaches, and reputational damage.
Here’s what you need to know:
- Identify parties and roles: Clearly list all involved entities (data controllers, processors, providers, and recipients) and their responsibilities.
- Define data scope and uses: Specify what data will be shared, its purpose, and access limitations.
- Establish security protocols: Use encryption, access controls, and retention policies to protect data.
- Ensure compliance: Conduct regular audits, maintain documentation, and train staff on data handling.
- Address liability and breaches: Outline breach notification steps, liability terms, and dispute resolution processes.
- Plan for updates and termination: Review agreements regularly, update as needed, and ensure secure data destruction upon termination.
A well-structured DSA not only ensures compliance but also protects organizations from potential risks while fostering accountability in data sharing.
6-Step Data Sharing Agreement Compliance Checklist
Developing a Data Sharing Agreement Critical Elements & Process
Identify Parties and Define Roles
When sharing data, it's crucial to identify all the organizations involved and clearly define their roles. This includes listing every entity participating in the exchange, such as data controllers, data processors, data providers, and data recipients. According to the Information Commissioner's Office (ICO), your agreement should also include contact details for each organization's Data Protection Officer (DPO) or another individual responsible for overseeing data sharing.
It’s important to distinguish between the Data Provider, who grants access to the data, and the Data Recipient, who seeks access. If applicable, you may also need to identify a Data Custodian or Data Intermediary, who manages the technical aspects and reviews on behalf of the provider. For joint controller arrangements, the agreement must legally specify which controller will serve as the primary contact for data subjects.
"Your agreement should clearly identify all the organisations that will be involved in the data sharing and should include contact details for their data protection officer (DPO) or another relevant employee who has responsibility for data sharing." - ICO
This step sets the stage for assigning specific responsibilities in later sections.
List All Parties Involved
Documenting all organizations that will handle the data is a critical step. This includes identifying who will act as the data controller at every stage of the process. For each organization, record its name, the authorized signatory (such as someone from the Office of Sponsored Research or General Counsel), and the contact information for their DPO or designated data protection lead.
Additionally, include contact details for internal roles such as Project Officers, System Managers, Data Custodians, and authorized Data Users. This ensures clear accountability and communication. Confirm that the listed individuals have the authority to sign on behalf of their organizations.
To maintain accuracy over time, establish a process for updating the agreement when new organizations join or existing ones leave. Also, monitor staffing changes to ensure contact details and signatories remain current.
Define Roles and Responsibilities
After identifying all involved parties, assign specific responsibilities to each. The agreement should outline who the controllers are at every stage and clearly define what each party is responsible for.
| Role | Primary Responsibilities |
|---|---|
| Data Controller | Establish the purpose of processing, ensure lawful basis, and maintain overall compliance |
| Data Provider | Extract data, ensure its quality, and set terms for its use |
| Data Recipient | Follow security protocols, report breaches, and use data only as permitted |
| Data Custodian | Manage technical aspects like storage, access controls, and secure transmission |
Specify which departments or roles within each organization are allowed access to the shared data. Additionally, define responsibilities for handling individual rights requests - such as objections, rectifications, or erasures - to avoid compliance issues. This clarity ensures that all parties understand their obligations and prevents misunderstandings.
Obtain Signatures and Approvals
Once roles are defined, formalizing the agreement with signatures is essential. Signatures validate the agreement and establish accountability. A data sharing agreement serves as a set of shared rules that binds all participating organizations.
"If you are acting with another controller as joint controllers of personal data, there is a legal obligation to set out your responsibilities in a joint control arrangement..." - ICO
Ensure the agreement is signed by authorized individuals, typically senior management or designated officials, to confirm that all parties understand and accept the terms. While a formal agreement may not always be mandatory for separate controllers, it demonstrates compliance with the accountability principle, which requires organizations to show adherence to data protection laws. Also, include procedures for adding new organizations or removing existing ones from the arrangement, if necessary.
Define Data Scope and Permitted Uses
When sharing data, it’s essential to clearly define what data will be shared and how it can be used. This helps ensure that only relevant information is accessed and prevents misuse.
The agreement should detail the exact data being shared, broken down by type. For instance, in the U.S., this might include Personally Identifiable Information (PII), Protected Health Information (PHI), or Business Identifiable Information (BII). In the UK, data is categorized as personal data, special category data (e.g., health or biometric data), or criminal offense data. Each category comes with distinct legal and security requirements, making accurate classification a must.
"Your agreement should set out the types of data you are intending to share. This is sometimes known as a data specification." - Information Commissioner’s Office (ICO)
Beyond categorizing data, it’s critical to specify the source - such as the federal program, system, or dataset - and include details like file names and the time period the data covers. Also, clarify whether the data is identifiable or de-identified, as this impacts compliance and security protocols. Ownership and rights over the data should also be explicitly stated. These definitions lay the groundwork for secure and accountable data sharing.
Specify Data Types
Classifying data helps determine the level of protection required. For example, personal data typically needs standard safeguards, while more sensitive information - like health records or biometric data - requires stricter conditions and enhanced security.
Granular permissions can be applied to control access to specific data points, ensuring only authorized personnel with the necessary training can view sensitive information. To maintain consistency, define data formats (e.g., standardizing date formats) and adopt open standards to improve accuracy and compatibility.
| Data Category | Description / Examples | Relevant Framework |
|---|---|---|
| Personal Data / PII | Information that identifies an individual. | UK GDPR / US Privacy Act |
| Special Category Data | Sensitive data (e.g., health, race, religion, biometrics). | UK GDPR / DPA 2018 |
| PHI | Protected health-related information. | US HHS / CMS |
| Criminal Offense Data | Data on criminal convictions or offenses. | UK GDPR / DPA 2018 |
| BII | Business Identifiable Information. | US HHS |
| De-identified Data | Data stripped of identifiers to prevent re-identification. | US HHS |
Outline Permitted Uses
After defining the data, it’s equally important to outline its intended uses. This ensures that all parties stay aligned and prevents unauthorized secondary use. The agreement should clearly state the purpose of sharing, the necessity of the data for achieving that purpose, and any expected benefits to individuals or society.
"You should document this in precise terms so that all parties are absolutely clear about the purposes for which they may share or use the data." - Information Commissioner’s Office (ICO)
To minimize risks, apply purpose limitation - only collect and share the data needed for a specific goal, and delete it once that goal is achieved. Before sharing, conduct a necessity test to determine if the objective can be met with less data or by excluding personal information. Additionally, specify which departments or individuals within the recipient organization are authorized to access the data.
Set clear retention periods and deletion protocols to ensure data isn’t kept longer than necessary. For instance, data might be deleted once the project ends or the agreement is terminated.
Address Legal Basis and Consent
Every data-sharing arrangement must have a clear legal foundation. Organizations need to explain the lawful basis for sharing data under laws like the UK GDPR or DPA 2018. It’s important to note that the legal basis for sharing might differ between the sharing and receiving organizations.
Identify the specific legal authority that allows for data sharing. If relying on "legitimate interests" as the basis, document a Legitimate Interests Assessment (LIA). For sensitive data, additional conditions must be met beyond the standard legal basis.
If consent is the legal basis, include a model consent form and outline procedures for individuals to withdraw consent if needed. Document the decision-making process for data sharing, including the rationale for the chosen legal basis and whether data is shared with or without consent. Lastly, confirm that no legal barriers, such as confidentiality obligations or copyright restrictions, prevent the data from being shared.
Establish Security and Sharing Protocols
After defining what data will be shared and its purpose, the next step is ensuring its security - whether in transit or at rest. Proper security protocols are crucial to prevent unauthorized access, data breaches, and compliance violations. Your agreement should clearly outline the technical and organizational measures required from both parties.
Always encrypt identifiable data. The Centers for Disease Control and Prevention (CDC) emphasizes: "No electronic data containing identifying information should be transferred without being encrypted". Encryption tools meeting Advanced Encryption Standard (AES) criteria must be used for all transfers, including those involving portable devices. These encryption practices are foundational to secure transfer methods.
Secure Transfer Methods
Whenever possible, avoid file transfers. Instead, opt for a remote access model using virtual workspaces or remote APIs. These solutions allow authorized users to access and analyze data without physically exporting or duplicating datasets. This approach aligns with Zero Trust principles, enabling dynamic authorization - permissions that adjust in real time based on user identity and risk factors.
"Implementation of sharing as a virtual workspace or API enables dynamic authorization, which is a key Zero Trust principle." - CMS Technical Reference Architecture
If file transfers are unavoidable, your agreement should specify the exact transmission method (e.g., secure file transfer protocols) and the frequency of data sharing. For system-to-system exchanges between agencies or organizations, establish an Interconnection Security Agreement (ISA) to define the technical relationship and security requirements. Network access controls should ensure remote devices and users adhere to your organization's security policies. For methods like faxing, limit the inclusion of personally identifiable information and ensure hard drives are sanitized afterward. Before any electronic transfer, an Overall Responsible Party (ORP) or designated program official must approve it.
Access Controls and Retention Policies
Once data is securely transferred, access should be tightly controlled. Implement role-based access control (RBAC) to assign specific roles and access levels to authorized personnel. Adhere to the principle of minimum necessary access - only those with a legitimate need should handle identifiable data.
Your agreement should require the recipient to maintain a current log of all individuals with access to identifying data. This log should include names, reasons for access, and the specific storage locations of the data. Additionally, staff with access must complete annual security training and renew confidentiality agreements.
Define clear retention schedules and procedures for returning or destroying data when the project ends or the agreement terminates. Require recipients to provide formal certification of data disposition, documenting that all shared data has been properly deleted or returned. For physical documents, specify secure storage requirements and mandate the use of crosscutting shredders for disposal.
Technical Safeguards
Beyond encryption and access controls, additional technical measures are necessary to prevent breaches and unauthorized modifications. If the recipient uses cloud services, they must document that their provider is compliant with the Federal Risk and Authorization Management Program (FedRAMP). Systems processing shared data should have an Authority to Operate (ATO) and remain within defined authorization boundaries.
Automated monitoring systems should track and control user access, especially for remote users. For datasets accessed outside secure environments, protective software should manage data storage, removal, and usage. Regular computer backups and disaster recovery plans should be in place, and hard drives must be sanitized before disposal. Your agreement should also establish timelines and procedures for reporting data breaches - whether actual or suspected - to the data provider.
| Safeguard Category | Essential Measure | Purpose |
|---|---|---|
| Data Transfer | AES Encryption & Secure Channels | Protects data from interception during transit |
| Data Storage | FedRAMP Cloud / ATO Boundaries | Ensures storage meets federal security standards |
| Access Management | Zero Trust Access | Limits access based on real-time risk verification |
| Data Integrity | Protective Software & Monitoring | Prevents unauthorized changes or deletions |
| Disposal | Hard Drive Sanitization | Ensures data cannot be retrieved after agreement ends |
Implement Compliance Monitoring and Auditing
After setting up the data scope and security measures, the next step is ensuring compliance through continuous monitoring and regular audits. Without proper oversight, even the best security protocols can fall apart. Agreements can become outdated, security gaps might go unnoticed, and regulatory violations could occur.
Define Audit Procedures
Start by maintaining a central log or repository for all data-sharing agreements. This ensures every agreement is tracked and reviewed appropriately. As the Information Commissioner’s Office (ICO) highlights:
"Without a log or record of all agreements in place, there is a high likelihood that existing agreements will not be tracked or reviewed".
Each agreement should also link to its corresponding Data Protection Impact Assessment (DPIA).
It's essential to assign clear roles for oversight. For example, designate an Information Asset Owner (IAO) or an Overall Responsible Party (ORP) to monitor data-sharing activities and enforce security standards. Additionally, set up a formal review schedule - conduct reviews at least annually, but also define triggers for immediate action, such as changes in partners, shifts in data-sharing purposes, security breaches, or major complaints.
| Monitoring Procedure | Frequency | Key Responsibility |
|---|---|---|
| Policy & Procedure Review | At least annually | Overall Responsible Party (ORP) |
| Staff Training | Annually | All staff with data access |
| Compliance Certification | Annually | Program Officials |
| Data Quality Analysis | Periodic | Data Custodians / IAOs |
| Agreement Review | Regularly or upon "trigger" events | Information Governance Board |
Technical monitoring tools can help track, trace, and label information to ensure you know what data was shared, with whom, and when. Regular sampling exercises and data quality checks ensure the data remains accurate and follows agreed-upon formats. These reviews also verify that the data stays accessible and within its defined scope.
Document Retention and Reporting
Good documentation is the backbone of compliance. Specify in your agreements which records need to be kept and for how long. Incorporate data-sharing activities into your organization’s Record of Processing Activities (ROPA) and data flow mapping to clearly distinguish between controller-to-controller and controller-to-processor relationships. As the ICO states:
"The accountability principle means that you are responsible for your compliance with the UK GDPR or DPA 2018 as appropriate and you must be able to demonstrate that compliance".
Keep evidence of all compliance efforts, including DPIAs, Data Protection Officer (DPO) advice, and justifications for sharing decisions. For every sharing decision, document the purpose, the data shared, the recipient, and the lawful basis for processing. Maintaining a record of "what was shared and when" is crucial for handling individual rights requests and managing data breaches.
Audit findings should be regularly reported to senior management. Include these findings, along with the results of data-sharing reviews, in the agenda for your information governance board or equivalent body. Track and report non-compliance issues and follow up with corrective actions. Require program officials to certify annually that all data security and sharing standards are being met.
Staff Training and Awareness
Training plays a key role in compliance. Conduct a Training Needs Analysis (TNA) to identify which roles require data-sharing and audit training. The ICO underscores the importance of this step:
"Train all staff likely to make decisions about data sharing, and make them aware of their responsibilities. Refresh this training appropriately".
Your Data Protection Officer should oversee and contribute to the training content to ensure it meets legal requirements. Make sure staff understand the distinctions between controller-to-controller and controller-to-processor relationships, as these dictate the compliance framework to follow. Require all employees with access to identifiable data to sign confidentiality agreements upon hire and renew them annually.
Keep records of all training sessions, including content and attendance, to demonstrate compliance during audits or investigations. Training isn’t a one-and-done process - schedule regular refreshers. Internal audits should go beyond checking training completion; they should assess whether employees understand how data protection principles apply to their roles. Use permission controls to ensure only trained staff can access sensitive or restricted data sets.
sbb-itb-5f36581
Address Liability, Breaches, and Dispute Resolution
Beyond implementing strong security measures and monitoring compliance, it's essential to establish clear terms for liability and dispute resolution. A well-constructed data sharing agreement should address these areas to protect all parties involved and provide a clear plan for managing potential issues.
Define Liability and Indemnification
Responsibility for claims tied to each party's actions must be clearly assigned. As Bloomberg Law explains, indemnification agreements transfer risks or costs from one party to another. Your agreement should explicitly state that parties are accountable for claims resulting from their own actions, in accordance with federal and state laws.
Include provisions for losses stemming from breaches of representations, warranties, or duties. For example, if a data recipient misuses shared data and faces legal action, the indemnification clause will determine who covers the legal expenses. Keep in mind that most jurisdictions prohibit indemnification for gross negligence, reckless behavior, or intentional misconduct, so structure your clauses with these limitations in mind.
Be cautious with "hold harmless" language. Courts interpret this term differently - some see it as redundant to "indemnify", while others treat it as a clause that releases the indemnified party from liability to the indemnifier. Use precise wording to avoid misunderstandings. Also, ensure that liability and indemnification responsibilities continue even after the agreement ends, so protections remain in place.
Establish Breach Notification Procedures
Once liabilities are defined, the agreement must also include clear breach notification protocols. It should specify what qualifies as an "actual or suspected breach" or security incident. Require notifications within a short timeframe - typically 24 to 72 hours - so the data owner can meet any regulatory obligations.
The agreement should list specific contacts, including names, offices, and communication methods for reporting incidents. Notifications should provide detailed information, such as the type of data involved (e.g., PII or PHI), the identity of any unauthorized recipient, whether the data was accessed or acquired, related system documentation, and mitigation steps taken.
Additionally, the data recipient should be required to maintain records for investigations and take measures to prevent future breaches. The agreement should also clarify who is responsible for notifying affected individuals and regulators and who will cover the associated costs. As noted by HHS:
"The DUA structure supports... Accountability by having clear definitions of roles and responsibilities and specifying penalties for failure to comply with the terms of the DUA".
Set Dispute Resolution Processes
Disputes are inevitable, so your agreement should include a clear process for resolving them. Specify which state or federal laws govern the contract and where legal proceedings will occur. Include cure periods - such as 30 days - allowing a party to address a material breach before the other party can terminate the agreement or seek legal remedies.
Define escalation procedures, starting with informal discussions between project officers or data custodians before escalating to formal litigation. Include timelines for reporting violations of the agreement. To save time and money, consider adding clauses for mediation or arbitration as alternatives to traditional court proceedings.
Finally, outline termination procedures for both cause (e.g., unresolved breaches) and no cause, specifying notice periods and requirements for returning or destroying data. Ensure that exclusions to liability limitations - such as those for willful misconduct or gross negligence - apply equally to all parties.
Plan for Review, Renewal, and Termination
Data Sharing Agreements (DSAs) need regular reviews to keep up with changing regulations, business priorities, and security challenges.
Schedule Regular Reviews
Set a consistent review timeline - ideally every three years or sooner if there's a breach, a major complaint, or a shift in the purpose of data sharing. During each review, check that the sharing arrangement is still necessary and proportionate. Confirm that only the minimum data required is being shared and that your security protocols are up to date. Additionally, review breach reporting timelines and ensure staff training reflects current practices.
"You should review your data sharing arrangements on a regular basis; and particularly when a change in circumstances or in the rationale for the data sharing arises."
– Information Commissioner's Office (ICO)
Outline Renewal and Update Procedures
Identify key changes - like new parties, expanded data scope, updated purposes, shifts in roles, or changes in laws - that require a formal update to the DSA. Include a Modification clause specifying which departments, such as the Office of the General Counsel or Chief Data Officer, need to approve these updates. Clearly outline the agreement's start and end dates in a "Period of Agreement" section, along with renewal or extension procedures. All finalized and updated agreements should be stored in a central repository for easy access by authorized users, helping determine if existing agreements can be reused. These protocols streamline updates and prepare for clear termination processes.
Include Termination and Data Destruction Terms
Define clear termination notice requirements, both for termination without cause and in response to breaches. Ensure the agreement mandates secure data return or destruction upon termination.
"A data sharing agreement... should have procedures for dealing with the termination of the data sharing initiative, including the deletion of shared data or its return to the organisation that supplied it originally."
– Information Commissioner's Office (ICO)
Require a Certificate of Destruction after termination. Include a Survival Clause to specify which obligations - such as confidentiality, indemnification, or liability limitations - remain in effect after the agreement ends. Finally, conduct a thorough audit to confirm all data has been disposed of according to the terms of the agreement. This structured approach to termination ensures accountability and proper handling of data even after the agreement concludes.
Key Documentation Checklist
This checklist is your go-to guide for ensuring your organization has all the critical documentation needed for effective and compliant data sharing. Each piece of documentation plays a vital role in your Data Sharing Agreement (DSA) process, from defining responsibilities to meeting regulatory requirements. The table below categorizes the documents, making it simple to spot any missing elements in your compliance efforts. Store these records in a centralized, secure location accessible only to authorized personnel. Regularly review this checklist to maintain compliance and address any gaps promptly.
| Document Category | Required Documentation | Compliance Purpose | Status |
|---|---|---|---|
| Legal Framework | Signed Data Sharing Agreement (DSA) or Memorandum of Understanding (MOU) | Establishes roles (e.g., controllers/processors) and sets standards | ☐ Complete |
| Risk Management | Data Protection Impact Assessment (DPIA) | Identifies and mitigates risks to individuals, especially in high-risk scenarios | ☐ Complete |
| Lawful Basis | Legitimate Interests Assessment (LIA) or documented legal power | Justifies data sharing when consent or legal obligation isn’t applicable | ☐ Complete |
| Consent Records | Model consent forms and withdrawal records | Provides proof of individual consent where required | ☐ Complete |
| Data Scope | Data specification or dataset inventory | Clearly defines shared data to avoid excessive disclosure | ☐ Complete |
| Justification | Data Sharing Decision Form | Documents the "why, who, when, and how" for each data-sharing instance | ☐ Complete |
| Governance | Staff training logs and awareness records | Shows that personnel are trained and capable of managing shared data | ☐ Complete |
| Security | Technical and organizational measures documentation | Details encryption, access controls, and other security measures | ☐ Complete |
| Data Lifecycle | Retention and deletion schedules | Ensures data is only retained as long as necessary | ☐ Complete |
| Rights Handling | Individual rights procedure manual | Explains how to handle requests for access, rectification, or erasure | ☐ Complete |
| Accountability | DPO advice and audit reports | Provides evidence of expert input and regular compliance audits | ☐ Complete |
This table not only helps you organize your documentation but also ensures that your data-sharing practices are transparent and aligned with regulatory expectations. By keeping these records up-to-date, your organization can demonstrate accountability and readiness for audits or reviews.
Conclusion
Data sharing agreements aren't static - they require careful planning, clear documentation, and continuous oversight to keep your organization both compliant and secure. Accountability is key, which means every decision, safeguard, and update must align with the latest regulations. This principle ties directly to the practical steps we've discussed earlier.
As laws and regulations shift, your data sharing practices need to evolve too. For instance, under HHS policy, Data Use Agreements must be reviewed at least every three years. However, don't rely solely on these scheduled reviews. If there’s a change in security measures, partners, or how the data is used, an immediate reassessment is essential.
Thorough documentation does more than just meet legal requirements - it strengthens internal controls. Keeping signed DSAs, training logs, and other records on hand shows that risks are being actively identified and managed. When roles are clearly outlined, security protocols are recorded, and retention schedules are followed, you're building a strong framework to protect your organization and the people whose data you handle.
FAQs
What should a Data Sharing Agreement include to stay compliant with legal and regulatory standards?
A Data Sharing Agreement needs to spell out the reason for sharing the data, how it will be managed, and the responsibilities of everyone involved. It should also clarify who owns the data, detail the security measures in place to protect it, and ensure adherence to legal and regulatory standards.
On top of that, the agreement should include guidelines for data retention and disposal and establish clear rules for access and usage.
Covering these aspects helps protect sensitive information, maintain compliance, and build trust among all parties.
How often should we review and update Data Sharing Agreements to stay compliant with regulations?
To keep up with changing regulations, it's important to review and update Data Sharing Agreements regularly as part of your organization's governance and compliance efforts. While there's no set rule for how often this should happen, it's generally a good idea to revisit these agreements periodically - especially if there are major shifts in laws, industry standards, or the type of data being exchanged.
Consistent reviews help reduce risks, promote transparency, and ensure all parties involved stay aligned with their legal and regulatory responsibilities.
What should you do if a data breach happens under a Data Sharing Agreement?
If a data breach happens under a Data Sharing Agreement, it's crucial to act immediately to secure the affected systems and limit any further harm. This might involve steps like restricting access, resetting passwords, and addressing any identified vulnerabilities. Bringing in experts, such as forensic investigators, can help pinpoint the cause and assess the full scope of the breach.
You’ll also need to notify the appropriate authorities and inform impacted individuals if required by law. Make sure to document every action taken to show compliance and support any ongoing investigations. Once the situation is under control, take time to evaluate and improve your security measures to minimize the chances of future breaches and stay aligned with data protection standards.
Related Blog Posts
Get new content delivered straight to your inbox

The Response
Updates on the Reform platform, insights on optimizing conversion rates, and tips to craft forms that convert.
Drive real results with form optimizations
Tested across hundreds of experiments, our strategies deliver a 215% lift in qualified leads for B2B and SaaS companies.


.webp)



