Cross-Border Data Transfers: Risks and Solutions

Transferring data across borders is essential for global business operations, but it comes with legal, security, and process-related risks.
Here’s why it matters:
- Legal Risks: Conflicting regulations like GDPR in Europe and new U.S. rules (e.g., Executive Order 14117) make compliance complex. Non-compliance can result in fines, such as Meta’s €1.2 billion penalty in 2023.
- Security Risks: Data in transit is vulnerable to breaches, surveillance, and mismanagement, especially across jurisdictions with weak protections.
- Operational Issues: Managing vendors, data flows, and compliance across regions is time-consuming and prone to errors.
Key Solutions:
- Legal Safeguards: Use Standard Contractual Clauses (SCCs), Binding Corporate Rules (BCRs), and Transfer Impact Assessments (TIAs).
- Technical Defenses: Encrypt data, limit access, and monitor activity.
- Better Data Management: Map data flows, evaluate vendors, and use tools like Reform to ensure compliance during data collection.
By focusing on these steps, businesses can reduce risks, maintain compliance, and protect sensitive information during cross-border transfers.
Cross-Border Data Transfers in 2025: Regulatory Changes, AI Risks, and Operationalization
Key Risks of Cross-Border Data Transfers
When data crosses international borders, it opens the door to a range of legal, security, and operational challenges. Below, we break down the main risks organizations face when managing global data flows.
Legal and Regulatory Risks
Navigating the legal maze of cross-border data transfers is no small feat. Different countries impose their own rules on how data can leave their borders, and these rules often clash. For instance, transferring personal data from the EU to nations without an adequacy decision requires a Transfer Impact Assessment (TIA) and, in some cases, additional safeguards like encryption or data minimization.
The Schrems II ruling in 2020 turned EU-to-U.S. data transfers on their head. It invalidated the Privacy Shield framework, making it clear that Standard Contractual Clauses (SCCs) alone don’t cut it if the destination country’s surveillance laws undermine privacy protections. U.S. companies receiving EU data now face the added burden of evaluating risks related to U.S. government access under laws like the CLOUD Act and implementing extra protections.
The financial stakes are high. In 2024, Clearview AI faced a €30.5 million fine for transferring biometric data without a valid legal basis. In the U.S., overlapping privacy laws such as the CCPA, CPRA, and various state regulations add another layer of complexity once data lands on American soil.
Some countries, like China, take it a step further with data localization laws. China’s Personal Information Protection Law requires specific mechanisms - such as security assessments or certifications - for cross-border transfers of sensitive data, including financial and health information. The U.S. is also tightening its grip. Starting in April 2025, Executive Order 14117 will restrict the transfer of sensitive personal data - like biometric or geolocation data - to countries like China, Russia, and Iran.
Failure to comply with these regulations can lead to massive fines, halted data transfers, and operational disruptions. Companies may even be forced to redesign their data systems or repatriate data to comply with local laws.
But legal risks aren’t the only concern - security vulnerabilities also loom large.
Security Vulnerabilities
When data moves across borders, it becomes more exposed to threats. Whether transferred via APIs, VPNs, or cloud services, data in transit is vulnerable to interception, misconfigurations, and man-in-the-middle attacks.
Security standards vary by country, and weaker controls or slower incident response times in certain regions can increase the risk of breaches. Foreign government surveillance adds another layer of complexity. For example, under the CLOUD Act, U.S. authorities can compel U.S.-based providers to hand over data stored anywhere in the world, creating tension with EU privacy laws.
Coordinating security measures across time zones and jurisdictions is no easy task. Managing encryption keys in one region while storing data in another can create exploitable gaps. Similarly, patching vulnerabilities and monitoring threats across borders can slow response times and leave blind spots.
In the event of a breach, organizations face the daunting task of complying with different breach notification laws across jurisdictions. This turns incident response into a global coordination effort, often involving legal, security, and communications teams.
Even with airtight legal and security measures, operational challenges can throw a wrench into cross-border data strategies.
Operational Challenges
Operational hurdles often complicate cross-border data transfers, even when legal and security frameworks are in place. A major challenge is achieving full visibility into where personal data originates, where it’s stored, and which systems and vendors process it. Legacy systems, shadow IT, and ad-hoc integrations make accurate data mapping a difficult task.
Without precise data mapping, organizations may not know where data is replicated or forwarded to sub-processors in third countries. This lack of clarity can lead to compliance risks, as teams struggle to determine which transfers require SCCs, Binding Corporate Rules (BCRs), or other safeguards. Outdated data maps also slow down incident response, delaying efforts to assess the impact of a breach or meet notification deadlines.
Vendor management adds another layer of complexity. Many providers operate across multiple countries, triggering unexpected data transfers. Sub-processors - like cloud hosting services, analytics platforms, or offshore support centers - often fall under different legal regimes. If contracts and data protection agreements don’t clearly outline transfer locations and security requirements, companies risk losing control over their data.
Global vendor coordination can also be a headache. Conducting impact assessments and security evaluations for multiple providers takes time and can delay decision-making. Vendor outages or compliance issues in one region can disrupt operations worldwide, especially if critical data or processing capabilities need to be moved to stay compliant.
Addressing these operational challenges requires better data mapping and stronger vendor controls - topics we’ll explore further in the solutions section ahead.
Solutions to Reduce Cross-Border Data Transfer Risks
Reducing the risks tied to cross-border data transfers calls for a layered approach that combines legal safeguards, technical defenses, and operational rigor. Below are strategies that organizations can use to establish effective frameworks for managing international data flows.
Strengthen Legal Mechanisms and Compliance
Choosing the right legal framework is key to ensuring compliant cross-border data transfers. When possible, organizations should rely on adequacy decisions, which allow data to flow to jurisdictions deemed to have sufficient protections. This simplifies the process and avoids the need for additional contractual measures.
When adequacy decisions aren't an option, Standard Contractual Clauses (SCCs) are a widely used tool, especially for U.S.-based companies. These are particularly useful for transfers involving vendors or SaaS platforms. The 2021 EU SCCs introduce modular clauses tailored to different scenarios, stricter rules for sub-processors, and detailed security obligations. It's essential to use the latest version of these clauses and configure them correctly for each transfer.
For large multinational companies, Binding Corporate Rules (BCRs) provide a streamlined way to manage internal data transfers. While explicit consent can sometimes be used to justify transfers, its limitations make it unsuitable as a primary approach.
In regions with strict data localization laws - such as China's rules for financial and health data - businesses should minimize transfers by keeping sensitive data within the country. When necessary, only derived or anonymized data should be exported.
Another critical step is operationalizing Transfer Impact Assessments (TIAs). These assessments evaluate the legal and technical risks associated with transferring data to specific countries. A robust TIA process involves assessing the destination country's legal environment, evaluating safeguards like encryption, and documenting any residual risks. These assessments should be regularly updated, especially when regulations or geopolitical conditions change. Automated tools can help map data flows and maintain compliance, while internal audits ensure safeguards remain effective.
Integrating these legal mechanisms with clear Data Processing Agreements (DPAs) and comprehensive records of processing activities strengthens compliance efforts. This combination helps organizations avoid penalties while laying the groundwork for secure data handling.
Implement Strong Data Security Practices
Legal measures alone aren't enough - technical controls are equally crucial to protect data during transfers. Using end-to-end encryption with strong algorithms like AES-256 for stored data and TLS 1.2 or higher for data in transit significantly reduces interception risks. It's essential to manage encryption keys in secure and trusted environments.
For highly sensitive information, such as financial or health records, pseudonymization or tokenization ensures that vendors handle only de-identified data. This adds an extra layer of security.
Access control is another key element. Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) can restrict data access based on an employee's role, location, or specific business needs. For example, a support team in one region should not have access to analytics data from another region unless it's absolutely necessary. Regularly reviewing access permissions and promptly revoking unnecessary access supports the principle of least privilege.
Monitoring and logging are equally important. Centralized logging systems should track access logs, data exports, and unusual activity. These systems can detect anomalies, such as bulk data exports or suspicious access patterns. Additionally, configuring region-specific instances for SaaS tools and limiting cross-region replication can further reduce risks. Routine penetration testing and security assessments ensure that these controls remain effective.
Staying updated on regulatory changes, such as those introduced by Executive Order 14117, is also crucial. These evolving requirements may demand additional safeguards and documentation for specific types of data.
Improve Data Mapping and Vendor Management
Accurate data mapping is the foundation of managing cross-border transfer risks. Organizations should maintain a detailed inventory of all systems that process personal data, including databases, SaaS tools, CRM platforms, and HR systems. This inventory should document where data is stored, who can access it, and how it flows across regions.
Manual data inventories can quickly become outdated, so automation tools are invaluable. These tools can scan data systems, analyze metadata, and create data lineage diagrams in real time. Automated compliance maps can also flag unauthorized transfers, prompting timely reviews or updates to TIAs.
To keep data maps current, organizations should register new integrations in a centralized catalog and incorporate updates into change management processes. This visibility not only supports compliance but also speeds up incident response in the event of a breach.
Vendor management is another critical area. Businesses must evaluate where vendors store and process data, the transfer mechanisms they use, and their security measures. This includes encryption standards, access controls, incident response protocols, and vulnerability testing. Standardized questionnaires based on ISO 27001 or SOC 2 can streamline these evaluations. Additionally, reviewing DPAs, SCC appendices, and sub-processor lists helps verify that vendors meet necessary standards.
sbb-itb-5f36581
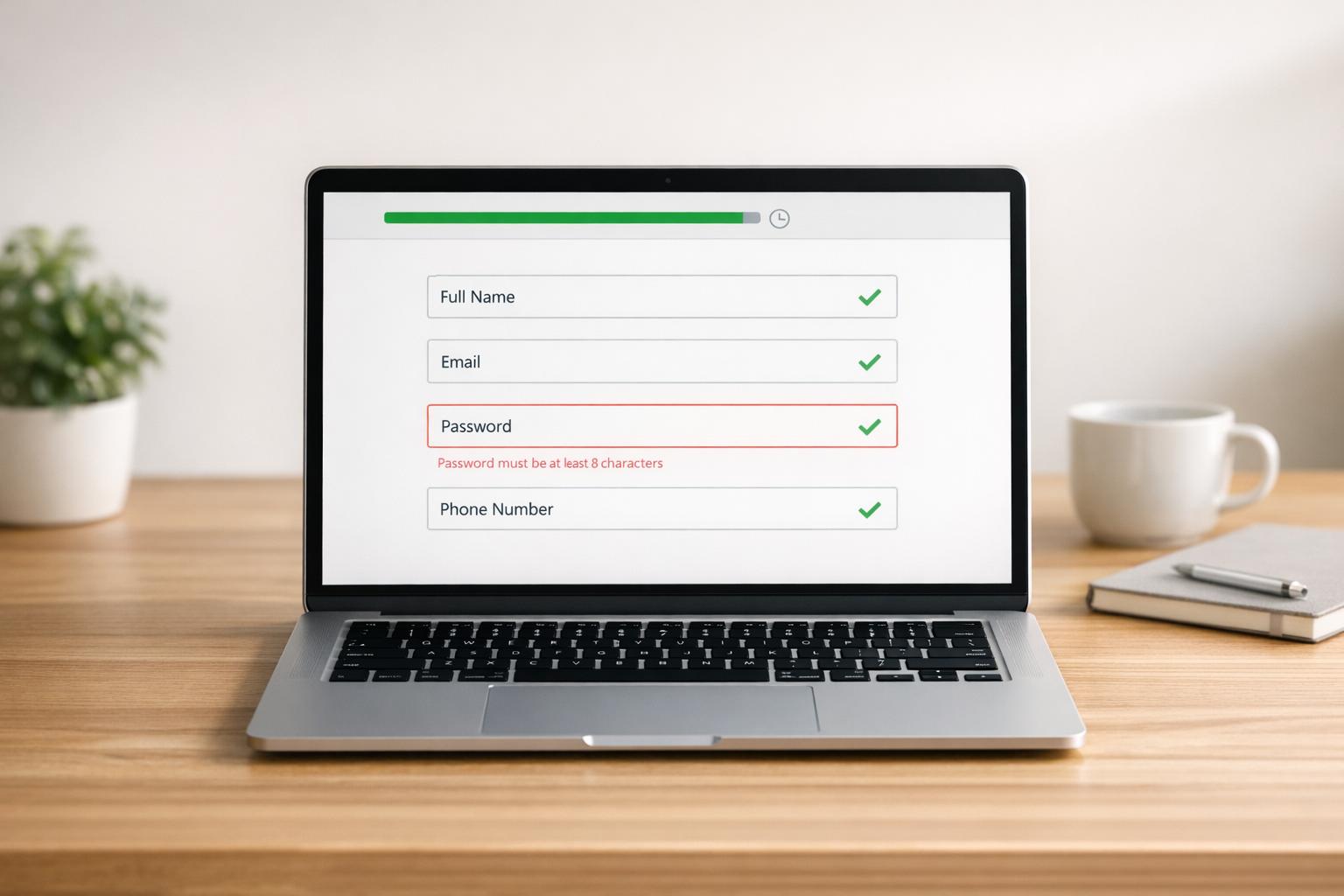
Privacy-Aware Form Design for Cross-Border Lead Collection
When dealing with cross-border lead collection, privacy-aware form design becomes a critical tool for ensuring compliance. These forms are often an overlooked source of international data transfers. Every time a form sends user data to a CRM, marketing platform, analytics tool, or cloud storage system located in another country, it triggers obligations tied to data transfers. For U.S.-based businesses collecting information from multiple regions, designing forms with privacy in mind is key. This means structuring every part of the form - fields, consent language, notices, routing, and storage - so that the data collection process complies with the strictest privacy rules, including GDPR for EU residents, LGPD in Brazil, PIPEDA in Canada, and state laws like California’s CCPA/CPRA.
The risks are serious: non-compliance can lead to steep fines and regulatory investigations. Poorly designed forms can act as a weak point for unlawful data transfers and heightened scrutiny from regulators.
Configuring Forms for Global Compliance
A crucial first step in privacy-aware form design is detecting where the user is located and presenting consent text and disclosures tailored to their region. This can be achieved by adding a country field and using conditional logic to adapt the form’s content based on the user’s location.
For users in the EU or EEA, forms must align with GDPR requirements. This includes identifying your organization as the data controller, explaining the purpose of data collection, stating the legal basis (e.g., "legitimate interests" or "consent"), and detailing cross-border transfer safeguards like Standard Contractual Clauses. Explicit consent checkboxes are mandatory - pre-checked boxes are not allowed. Similarly, for California residents, forms should include "notice at collection" elements that outline data categories, purposes, and provide a link to the privacy policy, along with an option to opt out of data sales or sharing.
For regions like Brazil (LGPD) and Canada (PIPEDA), the notice language should meet local requirements for consent, purpose specification, and transfer disclosures. Conditional logic can also help minimize data collection by hiding unnecessary or high-risk fields, such as national ID numbers or precise geolocation, depending on regional rules. For instance, EU users might see opt-in checkboxes with detailed channel preferences, while California users could be presented with an opt-out option. Documenting these configurations in a data protection impact assessment ensures that privacy, legal, and security teams can verify compliance. This adaptive approach also sets the stage for conditional routing, which further reduces risks tied to data transfers.
Reducing Transfer Risks with Conditional Routing
Conditional routing helps ensure compliance by directing form submissions to region-specific data centers. This approach restricts data transfers until all safeguards are in place. For example, submissions from EU users can be routed to EU-based data centers, Brazilian leads to infrastructure aligned with LGPD, and sensitive data - like health or payment details - can be kept within countries with strict localization requirements.
Routing can also control which downstream systems receive data. For instance, EU submissions could follow a processing path covered by Standard Contractual Clauses and strong security measures, while U.S. submissions might be sent to a broader set of tools. By segmenting data flows, businesses limit unnecessary transfers and demonstrate that they’ve assessed and documented their cross-border data controls. Routing data to specific workspaces or integrations also supports role-based access and data localization, reducing potential risks and aiding compliance efforts.
Using Reform's Security and Integration Features
Reform offers tools specifically designed to simplify privacy-aware form design. As a no-code form builder, it allows businesses to create reusable templates that include region-specific consent blocks, privacy links, and explanatory tooltips for key fields. Multi-step forms can be configured to identify the user’s region in the first step, dynamically adjusting later steps by showing or hiding fields, updating consent language, or enabling/disabling options.
Reform’s conditional routing is especially useful for cross-border compliance, directing submissions by geography to ensure data is processed in region-compliant environments. Features like advanced spam prevention and real-time email validation help ensure that only legitimate, valid data is collected, reducing the risk of processing fraudulent or non-compliant information.
With Reform, data security is a priority. It employs encrypted transmissions, real-time access controls, and seamless integrations with CRMs to ensure data remains protected. By centralizing data flows and enforcing strict security measures, Reform ensures only compliant data transfers occur. These features not only streamline form-based lead collection but also strengthen cross-border compliance, helping businesses mitigate risks effectively.
Additionally, Reform’s real-time analytics offer insights into submission origins, highlight key jurisdictions within lead pools, and evaluate the effectiveness of routing rules. This data supports ongoing risk assessments and ensures that cross-border lead collection remains both compliant and adaptable to evolving regulations.
Conclusion
Key Takeaways
Cross-border data transfers come with three primary risks: legal exposure from conflicting regulations, security vulnerabilities during transit and storage, and operational disruptions caused by fragmented vendor ecosystems. Non-compliance can lead to penalties as severe as €20 million or 4% of global annual turnover. To avoid these pitfalls, it’s crucial to manage risks proactively - documenting and anticipating cross-border data flows before issues arise can help prevent investigations and operational setbacks.
A solid risk management framework is built on three essential pillars:
- Strengthen legal mechanisms and governance: Leverage tools like Standard Contractual Clauses, Binding Corporate Rules, and adequacy decisions. Conduct Transfer Impact Assessments and ensure contracts and processing records are up to date.
- Implement technical and organizational security: Encrypt data both in transit and at rest, enforce role-based access controls, limit data collection, and monitor cross-border flows continuously.
- Optimize data and vendor workflows: Map data flows accurately, maintain a clear inventory of vendors and Data Processing Agreements, and design workflows that route data based on geography or legal requirements.
These pillars provide a structured approach to mitigating risks, leading naturally into how Reform’s tools can operationalize these strategies.
For practical next steps, start by mapping your data flows to understand what crosses borders and why. Choose the right legal transfer tools, enforce encryption and access controls, establish Data Processing Agreements with vendors, and configure systems to respect regional regulations using conditional routing and data minimization. Stay informed about regulatory changes and review critical flows regularly.
Privacy-focused forms play a key role in reducing cross-border risks by embedding compliance into the data collection process. By gathering data from multiple jurisdictions and feeding it into globally distributed systems, forms become a vital control point. Features like data minimization, jurisdiction-specific consent, and conditional logic ensure that only compliant and properly labeled data enters downstream workflows.
How Reform Helps with Global Lead Collection
Reform provides a practical solution for managing global lead collection while maintaining compliance. As a no-code form builder, it allows teams to create reusable templates with region-specific consent blocks and privacy disclosures. With multi-step forms and conditional routing, questions and data destinations adapt based on the user’s location. For example, EU users encounter GDPR-compliant consent referencing Standard Contractual Clauses, while U.S. users see CCPA/CPRA notices with opt-out options.
Reform’s integration controls let you define where data flows next, ensuring EU-origin data stays within specific environments or receives additional safeguards before syncing with U.S.-hosted systems. Real-time analytics track lead generation by region, helping teams evaluate risk and refine routing strategies. By embedding security at the point of data capture, Reform reduces risks during one of the most vulnerable stages of data transfer.
Because Reform is no-code and designed with ease of use in mind, privacy teams and marketers can collaborate to create compliant workflows without heavy engineering resources. This accelerates the adoption of privacy-by-design principles across campaigns, embedding cross-border compliance into everyday lead-generation activities instead of leaving it confined to policy documents.
Reform is scalable for businesses of all sizes. For smaller U.S. startups, the journey might begin with mapping key data flows, adopting Standard Contractual Clauses, and configuring forms with regional consent logic. Larger enterprises, on the other hand, can develop formal Transfer Impact Assessments, tier their vendors, and implement continuous monitoring. By turning privacy and security into operational strengths, Reform empowers businesses to manage global lead collection with confidence.
FAQs
What legal frameworks should businesses follow to ensure compliance with cross-border data transfers?
When dealing with cross-border data transfers, businesses need to navigate and comply with several critical legal frameworks to ensure data privacy and security. Here are some of the key regulations to keep in mind:
- General Data Protection Regulation (GDPR): This applies to businesses managing the personal data of individuals within the European Union. GDPR enforces strict requirements for transferring data outside the EU or EEA, emphasizing robust safeguards.
- United States-Mexico-Canada Agreement (USMCA): As part of this trade agreement, there are specific provisions aimed at protecting data while enabling the free flow of information between these three countries.
- Privacy Shield Alternatives: Since the EU-U.S. Privacy Shield was invalidated, businesses transferring data between the EU and U.S. often rely on mechanisms like Standard Contractual Clauses (SCCs) or Binding Corporate Rules (BCRs) to remain compliant.
To stay on the right side of these regulations, it’s crucial to review your data transfer processes, ensure they align with applicable laws, and adopt protective measures such as encryption or pseudonymization to reduce potential risks.
What steps can businesses take to secure data during cross-border transfers and minimize risks of breaches or unauthorized access?
To keep data secure during cross-border transfers, businesses should prioritize encryption - both for data in transit and at rest. This ensures sensitive information stays protected from unauthorized access. Pairing encryption with secure communication protocols, like HTTPS or VPNs, adds an extra layer of protection during transmission.
Equally important is adhering to local and international data protection laws, such as GDPR or CCPA, to steer clear of legal complications. Staying ahead of potential threats involves regularly updating security systems, conducting audits, and setting up strict access controls. These measures work together to minimize vulnerabilities and help businesses maintain the integrity of their data across borders.
How can organizations effectively manage data flows and vendor relationships when handling cross-border data transfers?
Organizations can navigate cross-border data transfers by putting well-defined data governance policies in place and adhering to international regulations like GDPR or CCPA. Begin by pinpointing potential risks tied to transferring sensitive data across borders - think data breaches or hefty regulatory fines - and take steps to tackle these issues head-on.
When working with vendors, focus on creating clear, transparent contracts that spell out data protection obligations. Regular vendor audits can help ensure they meet the required security standards. Additionally, incorporating tools like no-code platforms can simplify workflows, boost data accuracy, and improve communication with vendors, all while reducing risks and increasing operational efficiency.
Related Blog Posts
Get new content delivered straight to your inbox

The Response
Updates on the Reform platform, insights on optimizing conversion rates, and tips to craft forms that convert.
Drive real results with form optimizations
Tested across hundreds of experiments, our strategies deliver a 215% lift in qualified leads for B2B and SaaS companies.


.webp)