ISO 27001 Encryption Controls for Form Data

Protecting online form data is critical for security and compliance. ISO 27001 Annex A.8.24 outlines encryption controls to safeguard sensitive data during transmission and storage. Here's what you need to know:
- Why encryption matters: Online forms collect sensitive data like personal details and payment information, which can be intercepted during transmission or compromised if stored insecurely.
- ISO 27001 requirements: Encryption must protect data confidentiality, integrity, and authenticity. This includes using HTTPS/TLS for data in transit and AES-256 for stored data, alongside strong key management practices.
- Best practices: Classify data by sensitivity, encrypt high-risk fields, use secure TLS configurations, and manage encryption keys securely with regular rotations and access controls.
Cryptographic Controls in ISO 27001
Annex A.10: Cryptographic Controls
The way ISO 27001 handles encryption has changed over time. What was once outlined in Annex A.10 has now been updated and moved to Annex A.8.24. This updated approach highlights the importance of encrypting both data in transit and data at rest, ensuring that encryption policies align with business needs, legal requirements, and contractual obligations. The focus is on securing data throughout its lifecycle - whether it's being transmitted via a browser or stored in databases and backups. This shift reflects the growing need for modern web applications, like form platforms, to protect data at every step.
Main Goals of Cryptographic Controls
The primary objective of Annex A.8.24 is clear: to ensure cryptography is used effectively to protect the confidentiality, integrity, and authenticity of information. These principles are crucial for safeguarding form data:
- Confidentiality: Ensures that only authorized individuals or systems can access the submitted information.
- Integrity: Prevents data from being altered without detection.
- Authenticity: Confirms that the data originates from a trusted source.
For online forms, these principles translate into specific technical measures. For instance:
- Confidentiality: Encrypting form submissions during transmission using HTTPS/TLS and, if needed, encrypting stored data to protect against unauthorized access.
- Integrity: Using mechanisms like TLS, message authentication codes, or signed tokens to detect tampering with data or API calls.
- Authenticity: Employing trusted certificates for form endpoints, secure authentication for administrators, and digital signatures for sensitive processes like contract submissions or financial transactions.
These goals form the backbone of cryptographic strategies, but organizations must adapt them to the specific risks associated with their form data.
Applying Cryptographic Controls to Form Data
Implementing cryptographic measures starts with a clear, risk-based approach. ISO 27001 doesn’t prescribe specific algorithms or methods; instead, it requires organizations to assess the risks tied to their form data and decide on appropriate cryptographic solutions. These decisions must be documented in the Statement of Applicability, a key part of the ISO 27001 framework. This documentation ensures that the rationale behind encryption choices is clear and that auditors can verify that the measures are suitable for protecting high-risk data.
Encryption Best Practices for Form Data
Encrypting Stored Form Data
Start by classifying each form field based on its sensitivity to determine the appropriate level of encryption. For instance, contact details don’t require the same level of protection as Social Security numbers or payment information. Always encrypt sensitive fields while they are stored. Use AES-256 in GCM or CBC mode - these are widely trusted algorithms supported by reliable libraries. Stick to established encryption frameworks to avoid vulnerabilities.
Your encryption plan should cover every storage location: application databases, file systems, and even full-disk volumes. For highly sensitive data, like SSNs or health records, field-level encryption is a smart choice. This ensures the data stays encrypted, even to some internal users. A golden rule to follow: never store encryption keys alongside the encrypted data. Use a Key Management Service (KMS) or a Hardware Security Module (HSM) to securely store your keys. Additionally, ensure backups and replicas are encrypted as well. By securing stored data, you create a comprehensive encryption strategy that works alongside robust transmission protections.
Encrypting Form Data During Transmission
Once your stored data is secure, the next step is to protect it during transmission. Always serve form pages over HTTPS using TLS 1.2 or later - ideally TLS 1.3. Set up automatic redirects from HTTP to HTTPS and enable HSTS (HTTP Strict Transport Security) to block protocol downgrades. Configure your TLS settings to prioritize modern cipher suites like AES-GCM or ChaCha20-Poly1305 while disabling outdated options, such as SSL, TLS 1.0/1.1, RC4, 3DES, and weak key sizes.
Encryption should also extend to back-end communications. This includes connections between your web front end and application servers, interactions with databases, and communications with third-party APIs like CRMs or email services. Always use certificates from trusted certificate authorities - self-signed certificates are not suitable for production environments. Ensure certificates are well-managed and regularly updated.
Key Management Best Practices
A clear cryptographic policy is essential. It should outline approved algorithms, key sizes, usage guidelines, and responsibilities for managing the key lifecycle. Keys must be generated using cryptographically secure random number generators and stored securely in HSMs or cloud-based KMS platforms. Access should be strictly controlled with multi-factor authentication, and keys should never be stored in application configurations or source code.
Rotate encryption keys every 12 months, or immediately if a security breach occurs. Maintain a detailed inventory of keys, including their owners, expiration dates, and usage. When retiring keys, ensure they are securely destroyed following documented procedures. Limit access to keys to only those who absolutely need it, and log every action involving encryption, decryption, or key management. Regularly test your backup and recovery processes to confirm that encrypted data remains accessible after key rotations or system failures. This ensures your encryption strategy remains both secure and practical over time.
ISO 27001 - A8.24 - Use of cryptography
sbb-itb-5f36581
How to Implement ISO 27001 Encryption for Forms
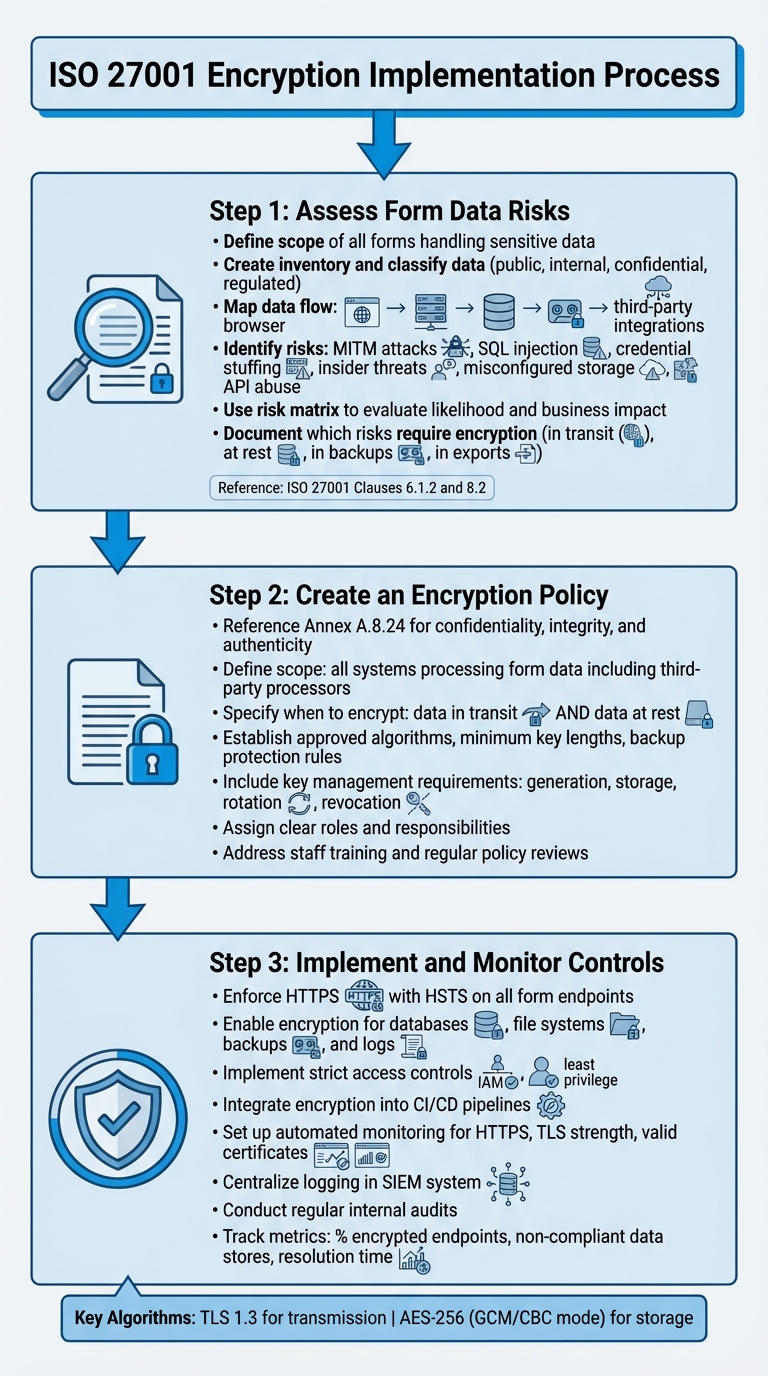
ISO 27001 Encryption Implementation Process for Form Data
Assessing Form Data Risks
Start by defining the scope of all forms that handle sensitive data, such as personal, financial, or confidential business information. Create an inventory of your forms, classify the data they collect (e.g., public, internal, confidential, regulated), and map the data flow - from the browser to servers, databases, backups, and any third-party integrations involved in processing the data. This will help you understand where vulnerabilities might exist and where encryption is necessary to protect the data at different stages of its lifecycle.
Next, identify specific risks, such as man-in-the-middle attacks, SQL injection, credential stuffing, insider threats, misconfigured cloud storage, and API abuse. Use a risk matrix to evaluate these threats, considering both their likelihood and potential business impact. For example, risks could result in fines, legal liabilities, revenue loss, or damage to your reputation. This approach aligns with ISO 27001 Clauses 6.1.2 and 8.2. Document which risks require encryption - whether during transmission, at rest, in backups, or in exports - and identify where additional measures like access restrictions, logging, or data loss prevention might be necessary.
Creating an Encryption Policy
Referencing Annex A.8.24, your encryption policy should ensure that cryptography safeguards the confidentiality, integrity, and authenticity of data. Define the policy's scope to include all systems that process form data, including third-party processors and exports. Standardize terminology for encryption, hashing, key management, and digital signatures to maintain consistency.
Your policy should specify when form data must be encrypted, both in transit and at rest. It should also establish approved cryptographic algorithms, minimum key lengths, and rules for protecting backups and removable media. Include detailed requirements for key generation, storage, rotation, and revocation. Assign clear roles and responsibilities, such as approving algorithms, managing keys, configuring systems, and monitoring compliance. If you rely on vendors or cloud services, ensure they adhere to equivalent cryptographic standards. Additionally, the policy should address staff training, awareness programs, and regular reviews to keep up with evolving risks and regulatory changes.
Implementing and Monitoring Encryption Controls
Ensure all form endpoints and downstream connections (such as APIs and CRMs) enforce HTTPS with HSTS, using automated certificate management and modern TLS configurations. For data at rest, enable encryption for databases, file systems, backups, and logs. Implement strict access controls using IAM roles and apply the principle of least privilege. To prevent configuration drift, integrate encryption settings into infrastructure-as-code and CI/CD pipelines, and document these controls to demonstrate compliance with Annex A.8.24.
Set up automated monitoring to confirm that all form endpoints use HTTPS, implement strong TLS, and maintain valid certificates. Periodically verify that any databases, storage systems, or backups containing form data remain encrypted. Centralize logging for encryption-related events, such as TLS configuration changes, key usage, key rotation, and failed decryption attempts. Feed this data into a SIEM system to detect anomalies and trigger alerts. Regular internal audits should verify compliance with your encryption policy, review access permissions for keys and encrypted data, and ensure that new forms or integrations are properly included in the encryption scope.
Finally, track metrics like the percentage of encrypted endpoints, the number of non-compliant data stores, and the time required to address issues. Include encryption controls in management reviews to ensure they evolve with changes in technology, threats, or regulations.
These steps provide a solid foundation for securely managing forms while aligning with ISO 27001 standards and leveraging Reform's advanced security features.
Using Reform for Secure Form Data Handling

Reform combines advanced encryption techniques with practical tools to ensure secure handling of form data.
Reform's Security Features
Reform safeguards form data both during transmission and storage, adhering to ISO 27001 standards. It implements the cryptographic controls described in Annex A.8.24. Data in transit is protected using HTTPS/TLS protocols, while data at rest is encrypted within its AWS-hosted infrastructure.
Beyond encryption, Reform includes powerful spam prevention tools to block unauthorized submissions, preserving data integrity. Its email validation feature ensures that only legitimate senders can submit forms, reducing the risk of fraudulent data entries. Additionally, real-time threat detection mechanisms - like rapid risk scoring, activity monitoring, and threat intelligence - help identify and stop bots or fake submissions before they become an issue.
Integration with Secure Workflows
Reform extends its encryption standards across integrations with platforms like HubSpot, Salesforce, and Mailchimp. Secure webhooks and APIs ensure that data remains encrypted during transfers to these external systems. For automated workflows, such as those created with Zapier, Reform encrypts form data to maintain security throughout the process. To further protect sensitive data, Reform uses context-aware access controls, including role-based access control (RBAC), attribute-based access control (ABAC), Zero Trust principles, just-in-time privileges, and continuous logging. These measures ensure that data remains secure as it moves through connected systems.
Customization for Compliance Requirements
Reform's multi-step forms make it easier to handle sensitive data securely. For example, payment details can be collected separately from contact information to comply with encryption policies based on risk levels. Conditional routing ensures that users only see fields relevant to their input, minimizing unnecessary data exposure. To configure Reform for ISO 27001 compliance, you can enable HTTPS-only mode, use conditional logic for high-risk fields, and set up custom webhooks with API keys. Additionally, Reform’s real-time analytics dashboard allows you to audit encryption logs and monitor performance regularly, helping maintain ongoing compliance. These features integrate seamlessly with broader ISO 27001 compliance strategies.
Conclusion
Key Takeaways
ISO 27001 Annex A.8.24 (formerly A.10) outlines a policy-driven framework for securing form data with cryptography, focusing on maintaining confidentiality, integrity, and authenticity during storage and transmission. Instead of prescribing specific algorithms, the standard emphasizes risk-based assessments to determine the right encryption strength for your organization's needs. This adaptable approach allows you to adjust as new threats emerge.
When implemented effectively, these measures can yield tangible benefits. For instance, studies indicate that organizations using ISO 27001-compliant encryption experience fewer data breaches. In one example, Vigilant Software highlighted how robust cryptographic controls thwarted man-in-the-middle attacks, sparing a company roughly $2.5 million in potential fines.
To protect your data, use proven encryption methods like TLS 1.3 and AES-256 for both storage and transmission. Combine this with strict key management practices, regular risk assessments, and comprehensive audits. Policies that include staff training and address legal requirements further strengthen compliance. Tools like Reform simplify this process with built-in TLS encryption, secure storage, and real-time analytics. These features can accelerate ISMS implementation by up to 81% using pre-configured controls.
By following these practices, you create a strong foundation for a reliable data protection strategy.
Final Thoughts
Taking a proactive stance on encryption not only minimizes risks but also builds user confidence. Encryption controls are central to ISO 27001 compliance, safeguarding data while fostering trust. The standard’s focus on risk assessment and policy development ensures your encryption practices stay effective in an ever-changing threat landscape.
Start by defining a clear cryptography policy, testing integrations, and conducting regular audits. Reform’s built-in security features make compliance more manageable, offering ready-to-use solutions for protecting data. By encrypting data at rest and in transit, securing encryption keys, and maintaining well-documented processes, you can establish a robust defense that protects both your data and your reputation. This streamlined approach aligns with our broader guidance on ISO 27001 encryption, ensuring consistency in your data protection efforts.
FAQs
What’s the difference between encrypting data in transit and at rest under ISO 27001?
Under ISO 27001, encryption plays a critical role in keeping data secure. Encryption in transit protects information as it moves across networks, such as the internet, by using secure protocols like TLS. This ensures that sensitive data stays private and secure during transmission.
Meanwhile, encryption at rest focuses on safeguarding stored data. Techniques like AES are used to make the data unreadable without the correct decryption key. This means that even if a storage device is lost or accessed without permission, the data remains protected.
Together, these two encryption methods create a strong defense for your data while also helping you meet ISO 27001 compliance standards.
What are ISO 27001's guidelines for securely managing encryption keys?
ISO 27001 places a strong focus on secure encryption key management as a cornerstone of protecting sensitive data. To achieve this, it recommends several key practices:
- Enforce strict access controls to ensure only authorized personnel can access encryption keys.
- Use secure hardware modules or similarly protected environments to store keys safely.
- Rotate encryption keys regularly to minimize the chances of compromise.
- Develop and implement clear policies that address every stage of the key lifecycle, from creation to secure disposal.
Adopting these measures helps organizations safeguard their data, prevent unauthorized access, and align with established security standards.
How can I assess risks and choose the right encryption strength for protecting form data?
When dealing with form data, it's crucial to evaluate how sensitive the information is and identify any potential security vulnerabilities. Begin by assessing the type of data you're collecting - whether it's personal details, financial information, or other sensitive inputs - and the risks associated with its exposure.
Refer to ISO 27001 guidelines to choose the right encryption algorithms and key lengths. These standards help ensure your encryption methods are both secure and compliant with industry requirements.
By matching your encryption approach to the specific risks, you can protect form data effectively while adhering to regulatory standards.
Related Blog Posts
Get new content delivered straight to your inbox

The Response
Updates on the Reform platform, insights on optimizing conversion rates, and tips to craft forms that convert.
Drive real results with form optimizations
Tested across hundreds of experiments, our strategies deliver a 215% lift in qualified leads for B2B and SaaS companies.


.webp)



