How to Navigate Global Data Transfer Laws

Global data transfer laws are stricter than ever in 2026. Non-compliance can mean fines up to 4% of annual revenue and operational disruptions. Here's what you need to know:
- EU and UK GDPR: Transfers outside the EEA or UK require safeguards like Standard Contractual Clauses (SCCs), Binding Corporate Rules (BCRs), or adequacy decisions. A Transfer Impact Assessment (TIA) is mandatory for SCCs.
- US Frameworks: The EU-U.S. Data Privacy Framework allows certified companies to transfer data. State laws add complexity.
- China's PIPL: Requires government security assessments, certifications, or approved contracts for international data transfers. New audits and stricter rules apply.
- Compliance Steps: Map data flows, assess risks, and monitor regulations. Use tools like SCCs, BCRs, or adequacy decisions to ensure lawful transfers.
Key Update: The UK now uses a "data protection test" instead of a Transfer Risk Assessment. China has introduced PIP Certification and stricter audit rules. Stay vigilant to avoid penalties and disruptions.
The Data Chronicles | Navigating global data transfer restrictions | U.S., EU, and China
Major Global Data Transfer Frameworks
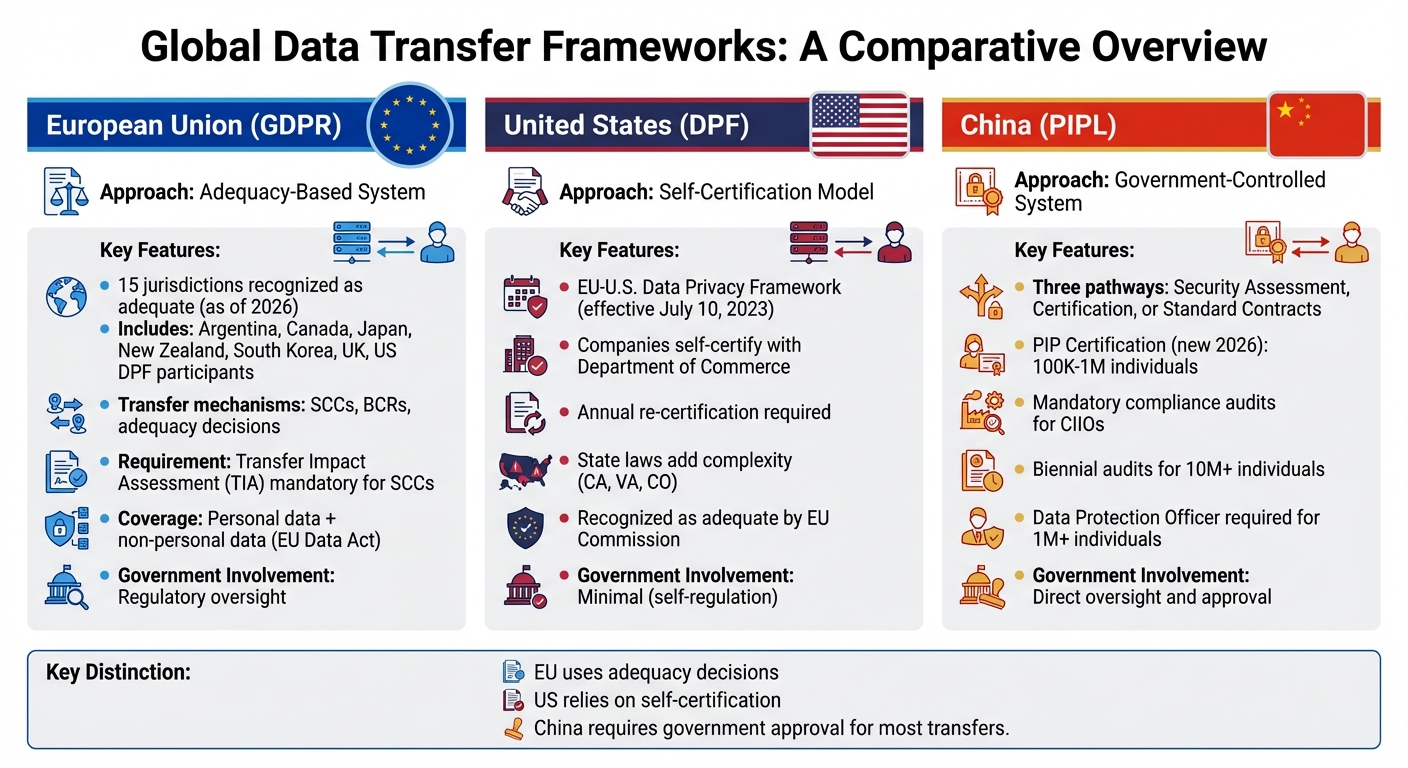
Global Data Transfer Frameworks Comparison: EU GDPR vs US DPF vs China PIPL
Different regions around the world have developed their own systems to regulate how data moves across borders. Understanding these frameworks is key for businesses to figure out which legal rules apply and how to comply when handling international data transfers.
European Union: GDPR and the EU Data Act
The General Data Protection Regulation (GDPR) ensures that data protection rules follow personal information wherever it goes. As the European Commission explains:
"The protection offered by the General Data Protection Regulation (GDPR) travels with the data, meaning that the rules protecting personal data continue to apply regardless of where the data lands".
When transferring data outside the European Economic Area (EEA), businesses have a few options. They can rely on adequacy decisions - 15 jurisdictions are recognized as adequate as of 2026, including Argentina, Canada, Japan, New Zealand, South Korea, the UK, and participants in the US Data Privacy Framework. Other options include using Standard Contractual Clauses (SCCs), Binding Corporate Rules (BCRs), or specific derogations like obtaining explicit consent for one-off transfers.
However, using SCCs comes with additional steps. Businesses must conduct a Transfer Impact Assessment (TIA) to ensure that the laws in the destination country, particularly around government surveillance, don't undermine data protection. Beyond personal data, the EU Data Act expands these obligations to include non-personal data, meaning businesses need to monitor all types of information they share across borders.
United States: Federal and State Laws
In the US, the approach to international data transfers is centered on self-certification under the EU-U.S. Data Privacy Framework (DPF), which became effective on July 10, 2023. Companies self-certify with the Department of Commerce to demonstrate compliance with the framework, which the European Commission recognizes as providing adequate protection. For instance, as of August 2025, Google LLC and its wholly-owned US subsidiaries maintained certification under the EU-U.S. DPF, the UK Extension, and the Swiss-U.S. DPF.
To remain compliant, organizations must complete annual re-certification to stay listed on the official Data Privacy Framework List. On top of federal rules, state-level privacy laws - like those in California, Virginia, and Colorado - add another layer of complexity. These state laws often differ from international standards, creating challenges for businesses trying to meet multiple compliance requirements.
China: PIPL and Cybersecurity Law
China takes a different approach, requiring direct government oversight for most international data transfers. Under the Personal Information Protection Law (PIPL), businesses must follow one of three pathways: pass a government security assessment, obtain certification from an approved institution, or use standard contracts authorized by Chinese regulators. Additionally, the Cybersecurity Law imposes mandatory compliance audits for critical information infrastructure operators and companies handling large amounts of personal data.
Unlike the EU's adequacy-based system or the US's self-certification model, China's framework relies heavily on government involvement to oversee and approve international data flows, making compliance more centralized and stringent.
Legal Mechanisms for Cross-Border Data Transfers
Once you've identified the regulatory frameworks relevant to your business, the next step is selecting the right legal mechanism for transferring data across borders. These tools act as safeguards, ensuring that data protection standards remain intact, no matter where the data is processed.
Standard Contractual Clauses (SCCs)
Standard Contractual Clauses (SCCs) are templates provided by regulatory authorities, such as the European Commission or the UK Information Commissioner’s Office. These clauses are typically used for data transfers between separate legal entities, like when your company shares customer information with an external vendor. On June 4, 2021, the European Commission updated its SCCs to replace older versions that had been in place since 1995.
Once executed, SCCs enable swift compliance, but completing a Transfer Impact Assessment (TIA) is still mandatory. Under Clause 14 of the updated EU SCCs, the TIA must evaluate whether the destination country’s laws - particularly those related to government surveillance - compromise data protection. If risks are identified, additional measures like end-to-end encryption or relocating data to a jurisdiction deemed adequate may be required.
In the UK, a similar process exists but uses different terminology. By January 15, 2026, the UK’s Data (Use and Access) Act will refer to this evaluation as a "data protection test" instead of a Transfer Risk Assessment. For UK-based transfers, organizations often rely on the International Data Transfer Agreement (IDTA) or the UK Addendum to the EU SCCs.
Binding Corporate Rules (BCRs)
While SCCs are designed for external transfers, Binding Corporate Rules (BCRs) are meant for data flows within a company’s corporate group. BCRs serve as internal codes of conduct, allowing multinational organizations to transfer personal data between their subsidiaries and branches under a unified framework. Unlike SCCs, which require separate contracts for each transfer, BCRs offer a one-size-fits-all solution for intra-group data movement.
The key advantage of BCRs is their flexibility: once approved by data protection authorities, they streamline compliance for all internal transfers. However, the approval process can be complex, requiring significant coordination with regulators. Like SCCs, BCRs also necessitate a risk assessment to address potential legal challenges in the destination country.
| Feature | Standard Contractual Clauses (SCCs) | Binding Corporate Rules (BCRs) |
|---|---|---|
| Use Case | Transfers between separate entities (e.g., vendors) | Transfers within a multinational organization |
| Implementation | Quick to execute once signed | Lengthy approval process with regulators |
| Flexibility | Limited; must adhere to pre-approved clauses | High; covers all group entities under one framework |
Note: Both mechanisms require a Transfer Impact Assessment (TIA) or equivalent evaluation to address risks tied to the destination country’s legal environment.
Region-Specific Transfer Mechanisms
In addition to global tools, some regions offer specialized options for data transfers. For example, UK organizations can use the UK Addendum to the EU SCCs. This shorter document validates EU data transfer contracts under UK law, making it especially useful for multinational companies managing UK-specific transfers.
In Southeast Asia, joint guidance from the European Commission and ASEAN provides businesses with a roadmap for navigating cross-border data transfers. This guidance highlights similarities between EU SCCs and ASEAN Model Contractual Clauses, simplifying compliance across these regions.
For transfers to China, companies must follow one of three government-approved pathways: passing a government security assessment, obtaining certification from an accredited institution, or using standard contracts authorized by Chinese regulators. Each option involves oversight by Chinese authorities.
Before selecting a mechanism, check whether the destination country has an adequacy decision. If it does, data can flow freely without additional safeguards. As of 2026, the European Commission recognizes 15 jurisdictions as adequate, including Argentina, Canada, Japan, New Zealand, South Korea, the United Kingdom, Uruguay, and participants in the US Data Privacy Framework. Armed with these legal tools, businesses can now adapt their strategies to meet shifting compliance requirements.
sbb-itb-5f36581
How to Build a Compliance Framework
Creating a compliance framework involves mapping your data flows, evaluating risks, and keeping an eye on regulatory changes.
Conduct a Data Mapping Exercise
Start by identifying where your data comes from, where it goes, and who handles it along the way. Document every data source, the countries it passes through, and its final storage location. Be thorough - include all internal departments and external partners like vendors, subprocessors, and cloud providers that interact with the data during its journey. As Microsoft explains:
"The first step is to understand where all personal data goes so that when it is transferred outside the EU it is processed with a level of data protection that complies with EU law."
Organize this information into a Record of Processing Activities (ROPA) or a detailed data inventory. For each data flow, identify the legal mechanism that applies to the destination country - this could be an adequacy decision, Standard Contractual Clauses (SCCs), or Binding Corporate Rules (BCRs).
If you’re dealing with data from U.S. individuals, remember the Department of Justice's Bulk Data Transfer Rule, effective April 2025. This rule applies to transfers involving over 100,000 U.S. persons for general identifiers, 10,000 for health or financial data, and as few as 100 for human genomic data. Non-compliance can lead to penalties exceeding $368,136 or twice the value of the transaction.
Once your data flows are mapped, the next step is to assess the risks with a Transfer Impact Assessment.
Implement Transfer Impact Assessments (TIAs)
After mapping your data, assess whether the receiving country’s laws provide adequate protection. TIAs are mandatory for EU exporters relying on Article 46 transfer tools like SCCs or BCRs when transferring data to countries without an adequacy decision. In the UK, this process is now called the "data protection test", as introduced by the Data (Use and Access) Act on January 15, 2026.
Your assessment should document the types of data involved, the identity of the importer, storage locations, and transfer methods. Analyze the destination country’s laws on surveillance and third-party access. If the legal framework doesn’t offer sufficient protection, you’ll need to apply additional safeguards, such as end-to-end encryption or data anonymization, before proceeding with the transfer. TermsFeed emphasizes this point:
"Data exporters must consider whether the laws and practices in third countries may impede the effectiveness of the safeguards provided by the transfer tools."
For the UK, apply equivalent measures under the data protection test. Be sure to revisit TIAs periodically, as political or legal changes can render earlier assessments outdated.
Once risks are addressed, focus on maintaining compliance through continuous monitoring.
Set Up Monitoring Processes
Compliance isn’t a one-and-done task - it requires ongoing vigilance. Regularly check updates from the European Commission and the UK Information Commissioner’s Office (ICO) for changes in adequacy decisions. The European Data Protection Board underscores this responsibility:
"Data exporters are responsible for monitoring whether adequacy decisions relevant to their transfers are still in force and not in the process of being revoked or invalidated."
Keep your internal documentation current, reflecting regulatory updates such as the UK’s move from "Transfer Risk Assessment" to the "data protection test". Update your data flow mappings to include new subprocessors operating in regions without adequacy decisions. Automated tools can be a big help here, tracking data usage and alerting your compliance team to unauthorized cross-border transfers in real time.
New Compliance Requirements in 2026
As 2026 begins, businesses face major regulatory updates that demand adjustments to their compliance frameworks. These updates reshape global compliance standards, building on previously established frameworks. Companies must adapt to these changes to avoid disruptions and penalties.
China's Mandatory Audit Reporting
Starting January 1, 2026, China implemented the Measures on Certification for Cross-Border Transfer of Personal Information, introducing PIP Certification as a third option alongside Security Assessments and Standard Contractual Clauses (SCCs). This certification applies to non-CIIOs transferring personal data of 100,000 to 1 million individuals or sensitive data of fewer than 10,000 individuals annually.
PIP Certification is valid for three years, with renewal applications required six months before expiration. Unlike SCC filings, PIP Certification involves a thorough review process, including potential on-site inspections by CAC-approved institutions. This mechanism provides a streamlined option for overseas entities, allowing them to apply through a designated representative in China.
Before applying, organizations must conduct a Personal Information Protection Impact Assessment (PIA) to confirm the legality and necessity of the data transfer. For multinational corporations managing intra-group transfers, PIP Certification can simplify compliance compared to filing separate SCCs for each transfer.
China’s updated Cybersecurity Law, also effective January 1, 2026, introduces stricter audit obligations. Companies processing data from over 10 million individuals must undergo compliance audits at least every two years. Additionally, those handling data from over 1 million individuals must appoint a Data Protection Officer and complete a filing.
If your organization is informed that it processes "Important Data", you must apply for a Security Assessment within two months and halt all transfers until the assessment is completed. By March 2025, the CAC had reviewed 298 Security Assessment submissions, approving 325 out of 509 specific data items for transfer. However, seven of the 44 assessments involving important data were rejected.
Cybersecurity Law Amendments
The amendments to China’s Cybersecurity Law, effective January 1, 2026, increase penalties for non-compliance and impose stricter data protection standards. Extensions for Security Assessments now limit future data transfers to a 20% increase over the approved volume.
The CAC has clarified that exemptions for "contract performance" and "HR management" apply only when the transfers are absolutely necessary.
Businesses operating in China’s Free Trade Zones should consult local "negative lists" to determine if their data transfers qualify for exemptions. If a local list doesn’t cover your industry, you can reference lists from other zones, such as Beijing or Shanghai.
UK ICO's Updated Guidance
Meanwhile, the UK is also revising its data transfer rules. On January 15, 2026, the UK Information Commissioner’s Office (ICO) released updated guidance to align with the Data (Use and Access) Act. A key change is the renaming of the "Transfer Risk Assessment" to a "data protection test". However, the ICO notes:
"A transfer risk assessment (TRA) is now referred to in UK legislation as a 'data protection test,' but we still use the term 'transfer risk assessment' and TRA in our guidance."
The new guidance outlines a three-step test to identify restricted transfers. Organizations must determine if:
- The UK GDPR applies to the processing,
- The transfer is being made to a recipient outside the UK, and
- The recipient is a separate legal entity.
If all three conditions are met, the transfer is restricted and must comply with UK adequacy regulations, safeguards like the International Data Transfer Agreement (IDTA), or specific exceptions.
To stay compliant, businesses should update their internal documentation to reflect the new terminology and ensure their privacy notices align with the Data (Use and Access) Act. The ICO has also introduced a "TRA tool" and specific guidance for transfers to the United States to help organizations adapt to the updated requirements.
Conclusion
Keeping up with global data transfer laws requires constant attention. Regulations are always changing - as shown by updates like the UK ICO's January 15, 2026 guidance - so businesses need to approach compliance as an ongoing effort. Make it a habit to regularly review regulatory updates.
A strong compliance plan begins with thorough data mapping. Pinpoint every instance where personal data is transferred across borders or accessed by entities outside your jurisdiction. From there, select the right transfer mechanisms: use adequacy decisions when applicable, apply safeguards like Standard Contractual Clauses (SCCs) for commercial transfers, and resort to exceptions only when absolutely necessary.
Part of this plan involves conducting detailed risk assessments through Transfer Impact Assessments (TIAs). These assessments are mandatory when relying on safeguards like SCCs. They evaluate whether the destination country’s legal framework could weaken data protection and determine if extra measures - such as encryption or contractual commitments - are required. Keep in mind, failing to comply with EU or UK GDPR transfer rules can lead to fines reaching 4% of an organization’s global annual revenue.
To stay compliant, maintain a detailed transfer log documenting all restricted transfers and the legal mechanisms used. Set up alerts to track changes in adequacy decisions and ensure all subprocessors adhere to the same high standards. This systematic approach strengthens your overall compliance efforts.
Additionally, aligning your data collection methods with compliance requirements adds another layer of security. Use tools like form builders that support data residency controls and consent mechanisms. For example, Reform provides a no-code solution for creating branded, high-performing forms tailored to meet compliance needs. By combining careful data collection with secure transfer practices, you not only safeguard sensitive information but also build trust with customers across different regions.
FAQs
What are the main differences between the EU GDPR, US DPF, and China's PIPL for international data transfers?
The EU GDPR, US Data Privacy Framework (DPF), and China’s Personal Information Protection Law (PIPL) each take a distinct approach to regulating international data transfers.
Under the GDPR, transferring data outside the European Economic Area (EEA) is only permitted if the recipient country ensures an adequate level of protection. Alternatively, businesses can use safeguards like Standard Contractual Clauses (SCCs) or Binding Corporate Rules (BCRs) to align with EU data protection standards.
The DPF offers a voluntary certification program for U.S. organizations overseen by the Federal Trade Commission (FTC) or Department of Transportation (DOT). Certified companies can receive data from the EEA without needing additional safeguards, provided they adhere to principles such as transparency, user choice, and data security.
China’s PIPL enforces strict government oversight for cross-border data transfers. Businesses must either pass a Security Assessment, obtain a PIP certification, or register SCCs with regulators. Failure to comply can lead to hefty fines - up to ¥50,000,000 or 5% of a company's annual revenue. The PIPL also includes rights for individuals that are comparable to those under the GDPR.
In essence, the GDPR emphasizes adequacy and contractual safeguards, the DPF streamlines transfers through certification, and the PIPL enforces government-approved mechanisms with severe penalties for violations.
How can businesses comply with the changing global data transfer laws in 2026?
To align with the shifting global data transfer laws set for 2026, businesses need to approach international data transfers as an ongoing risk management task. Start by mapping out all personal data flows, pinpointing the legal frameworks that apply to each destination. These could include the EU-U.S. Data Privacy Framework, the UK’s Data (Use and Access) Act 2025, or the United States’ Executive Order 14117. Once the data flows are mapped, perform a Transfer Risk Assessment (TRA) for any restricted transfers and choose suitable safeguards. Options include Standard Contractual Clauses (SCCs), Binding Corporate Rules, or the UK’s International Data Transfer Agreement. Be sure to document your findings and integrate the selected safeguards into your contracts.
Tools like Reform can make compliance easier. Reform helps businesses design forms that enforce data minimization, embed GDPR-compliant consent checkboxes, and automatically direct submissions to pre-approved storage locations. It also logs consent timestamps in the U.S. date-time format (MM/DD/YYYY hh:mm AM/PM) and keeps secure audit trails. These features help meet documentation and accountability standards. Stay on top of regulatory updates and adjust your processes regularly to ensure continued compliance.
What are the key steps to effectively complete a Transfer Impact Assessment (TIA)?
To carry out a Transfer Impact Assessment (TIA) successfully, begin by defining the scope and mapping the data flows. This means identifying the types of data being transferred, the reason for the transfer, the parties involved, and the path the data will take to reach its destination country.
The next step is to evaluate the legal environment of the recipient country. Look closely at its surveillance laws, how law enforcement can access data, and any regulations that could affect data protection. Then, compare these findings to the EU’s data protection standards to determine whether the transfer aligns with an adequacy decision, standard contractual clauses, or other mechanisms outlined in Article 46 of the GDPR.
If you identify any shortcomings, put additional safeguards in place. These can include encryption, pseudonymization, or specific technical and contractual measures designed to address any gaps in protection. Finally, document every step of the process in a detailed report. This report should include your risk analysis, the safeguards you’ve chosen, and a strategy for ongoing monitoring. Make sure the report is reviewed and approved by your Data Protection Officer or a similar compliance authority.
Related Blog Posts
Get new content delivered straight to your inbox

The Response
Updates on the Reform platform, insights on optimizing conversion rates, and tips to craft forms that convert.
Drive real results with form optimizations
Tested across hundreds of experiments, our strategies deliver a 215% lift in qualified leads for B2B and SaaS companies.


.webp)