SCC Challenges After Schrems II: What to Know

The Schrems II ruling in 2020 reshaped international data transfers, invalidating the EU–US Privacy Shield and imposing stricter rules on Standard Contractual Clauses (SCCs). Here’s what you need to know:
- Key Changes: SCCs require detailed Transfer Impact Assessments (TIAs), supplementary safeguards like encryption, and the suspension of transfers if protections fall short.
- Legal Context: U.S. surveillance laws (e.g., FISA 702) were deemed inadequate under EU privacy standards, complicating compliance for businesses.
- Practical Challenges: Companies face hurdles like mapping data flows, managing vendor contracts, and adapting to the updated SCC framework from 2021.
- Solutions: A thorough compliance process, including risk assessments, technical safeguards, and leveraging tools for automation, is critical to meeting these requirements.
Noncompliance risks hefty fines (up to 4% of global revenue), making it crucial for businesses to prioritize continuous monitoring and robust safeguards for cross-border data transfers.
International Data transfers after Schrems II
How Schrems II Changed SCCs
The Schrems II ruling shook up international data transfers by invalidating the Privacy Shield and reshaping how Standard Contractual Clauses (SCCs) are used. On July 16, 2020, this decision left over 5,000 U.S. companies without a valid transfer mechanism. The Court made it clear: SCCs could no longer be treated as a mere "check-the-box" exercise. Here's a closer look at the key changes that followed.
Key Changes from Schrems II
Schrems II introduced stricter requirements, demanding a case-by-case evaluation of data transfers. The Court of Justice of the European Union (CJEU) ruled that data exporters must ensure the destination country's legal framework provides protections equivalent to those in the EU.
This ruling brought three major responsibilities for organizations:
- Transfer Impact Assessments (TIAs): Companies must evaluate and document the risks posed by the legal environment in the recipient country.
- Supplementary Measures: If the importing country's laws - like U.S. surveillance laws under FISA Section 702 or Executive Order 12333 - pose risks to SCC protections, companies must implement additional safeguards, such as advanced encryption methods.
- Suspension of Transfers: If adequate protection cannot be ensured, even with extra measures, organizations are obligated to halt or terminate the transfer.
The 2021 SCC Framework
In response to these heightened requirements, the European Commission introduced a revamped SCC framework in 2021. This new framework employs a modular structure tailored to four specific transfer scenarios: Controller-to-Controller (Module 1), Controller-to-Processor (Module 2), Processor-to-Processor (Module 3), and Processor-to-Controller (Module 4). Notably, even before this update, 88% of organizations surveyed in the IAPP-EY Annual Privacy Governance Report 2019 already relied on SCCs for international data transfers.
The updated framework brought several practical changes:
- Docking Clause: This feature allows additional parties to join an existing agreement during its term without requiring entirely new contracts.
- Integration of GDPR Article 28: The clauses now directly incorporate GDPR Article 28 obligations, often removing the need for separate Data Processing Agreements.
- Government Access Provisions: The new SCCs include specific rules for handling government access requests, requiring importers to notify exporters and challenge any unlawful demands.
The transition to this updated framework began on September 27, 2021, for new contracts, with existing agreements required to comply by December 27, 2022.
Main Challenges in SCC Implementation
The updated SCC framework provides clearer guidelines, but putting it into practice is no small feat. It demands ongoing effort, specialized knowledge, and considerable resources. Among the most pressing challenges are the intricacies of conducting Transfer Impact Assessments (TIAs).
Transfer Impact Assessments (TIAs)
TIAs are far from straightforward. Companies must map out every instance of EU data leaving its borders, including less obvious scenarios - like IT support in the U.S. remotely accessing EU-based systems. For organizations with extensive vendor networks, this data mapping can be a time-consuming and resource-intensive task.
Assessing whether countries such as the United States offer protections "essentially equivalent" to EU standards under laws like FISA Section 702 or Executive Order 12333 adds another layer of complexity. These evaluations often require expert legal interpretation, especially when determining if government surveillance is "necessary and proportionate." Unfortunately, the lack of transparency in these laws makes this task even more challenging. Applying the four European Essential Guarantees requires a nuanced understanding that many organizations may not have in-house.
To complicate matters, secrecy and gag orders in certain jurisdictions prevent data importers from informing exporters about government data access requests. This lack of transparency makes it nearly impossible for EU-based companies to ensure their data is adequately protected. Moreover, TIAs aren't a one-time task - they require ongoing monitoring of legal and policy changes in recipient countries. Noncompliance can result in severe penalties, including regulatory fines of up to 4% of global annual turnover.
When risks emerge during TIAs, organizations must act by implementing additional safeguards.
Additional Safeguards for Data Transfers
If a TIA identifies risks in the destination country, companies must introduce extra protective measures. One widely used approach is encryption, which can prevent unauthorized access. However, encryption has its limits. In many cases, such as cloud processing, the data importer needs access to unencrypted information to perform their duties. In these scenarios, encryption alone may not be sufficient.
"Contractual and organisational measures may not, alone, suffice to provide the essential equivalent standard that EU law requires. Much will therefore rest on technical measures such as encryption and pseudonymisation".
To address this, organizations are encouraged to keep encryption keys exclusively within the European Economic Area (EEA) or in countries deemed adequate by the European Commission. Some companies have adopted creative strategies like "warrant canaries" - regularly issued cryptographic messages confirming no secret disclosure requests have been received. Others rely on pseudonymization, which involves transferring data in a format that cannot identify individuals without additional information stored securely within the EU. These measures highlight the limitations of relying solely on contractual protections to prevent government access.
However, these technical requirements add another layer of complexity to contract management, which is already a challenging area.
Contract Updates and Vendor Management
The revised SCC framework places significant demands on vendor management. Its modular design - covering Controller-to-Controller, Controller-to-Processor, Processor-to-Processor, and Processor-to-Controller scenarios - adds administrative hurdles.
One major change is the requirement to provide specific names of sub-processors instead of general categories. This means contracts must be updated more frequently as vendor relationships change. Additionally, the core text of the SCCs cannot be altered. Making changes beyond selecting modules or completing annexes risks invalidating the agreement, potentially requiring approval from supervisory authorities.
The deadline of December 27, 2022, for transitioning to the updated SCCs added to the pressure. Ensuring compliance for onward transfers further complicates vendor management. Data importers must verify that any third parties they work with meet the same stringent standards, often necessitating written agreements that mirror the original SCCs' protections.
sbb-itb-5f36581
Recent Regulatory Changes
Since Schrems II, the regulatory environment has undergone notable shifts. Keeping up with these changes is essential for ensuring compliance, especially as updates to Standard Contractual Clauses (SCCs) demand heightened attention.
GDPR's Global Reach and Compliance Challenges
The complexities of evaluating legal systems have now intertwined with broader regulatory updates, creating challenges for both public and private sectors. The GDPR's influence stretches far beyond the borders of the EU, posing ongoing hurdles for U.S.-based organizations. In 2024, the European Data Protection Supervisor (EDPS) intensified enforcement efforts, ruling that the European Commission had violated data protection laws in its handling of personal data transfers to a cloud-based service provider. This case underscores that the Schrems II standards are being applied not only to private companies but also to government bodies and international organizations. Essentially, no entity is beyond the reach of regulatory scrutiny.
U.S. Bulk Data Rule and Its Global Implications
On April 8, 2025, the U.S. Bulk Data Rule, enacted under Executive Order 14117, came into effect. This rule imposes strict limits on transferring sensitive personal data of U.S. citizens to "countries of concern", including China, Russia, Iran, North Korea, Venezuela, and Cuba. The restrictions are triggered when data transfers exceed specific thresholds:
- 100,000 individuals for personal identifiers
- 10,000 individuals for health or financial data
- 1,000 individuals or devices for precise location or biometric information
- 100 individuals for human genetic data
A grace period for civil enforcement was granted until July 8, 2025. By blending privacy concerns with national security priorities, this rule requires organizations to carefully map their data flows and include contractual safeguards to prevent data from reaching restricted third parties. These evolving U.S. regulations highlight the contrasting approaches to cross-border data protection, paving the way for frameworks like the Data Privacy Framework (DPF).
The Data Privacy Framework and SCCs
The EU-U.S. Data Privacy Framework (DPF), introduced on July 10, 2023, offers a simplified alternative to SCCs for U.S. organizations that achieve certification under the framework. Built on the foundation of U.S. Executive Order 14086, the DPF incorporates safeguards and a redress mechanism, eliminating the need for Transfer Impact Assessments (TIAs) when data is transferred to DPF-certified entities.
Nicola McCrudden, Of Counsel at Ogletree Deakins, notes:
"EO 14086 may also facilitate a more straightforward TIA with regard to transfers of personal data to the United States, even if the DPF itself is not the appropriate transfer mechanism for a particular transfer".
For businesses relying on SCCs with non-certified U.S. partners, the protections outlined in Executive Order 14086 can bolster TIA arguments by demonstrating that U.S. safeguards align closely with EU data protection standards.
Solutions for SCC Challenges
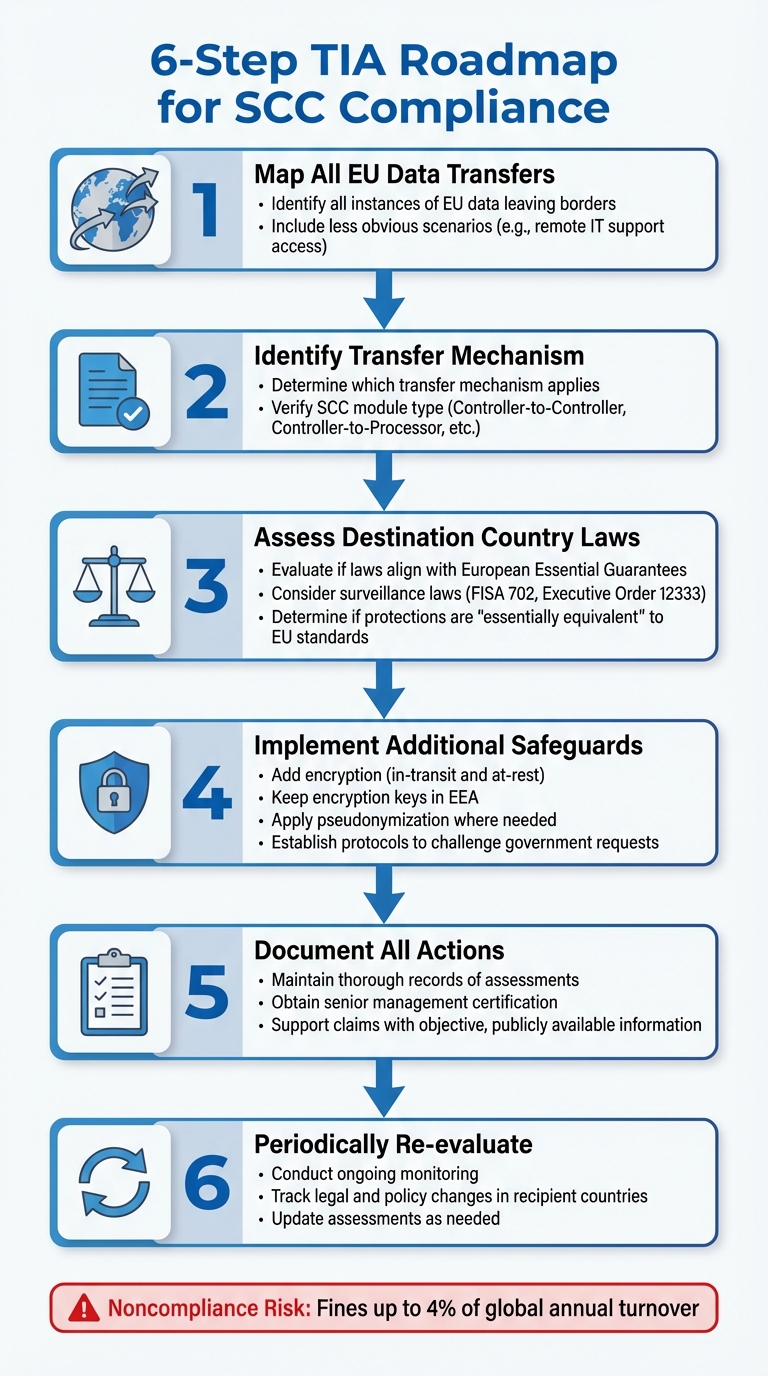
6-Step Transfer Impact Assessment (TIA) Roadmap for GDPR Compliance
Addressing the challenges of implementing Standard Contractual Clauses (SCCs) requires practical strategies and tools. Below are some key approaches to help organizations navigate compliance effectively.
Risk Assessment and Compliance Approaches
A solid compliance strategy begins with the six-step Transfer Impact Assessment (TIA) roadmap:
- Map all EU data transfers.
- Identify the transfer mechanism.
- Assess whether the destination country’s laws align with European Essential Guarantees.
- Implement additional safeguards if needed.
- Document all actions taken.
- Periodically re-evaluate the process.
Huw Beverley-Smith, Partner at Faegre Drinker, underscores the importance of thorough assessments:
"A subjective assessment that the transfer is not particularly risky given the nature of the data, the relevant industry sector and the likelihood of government access will not cut it".
While the 2021 SCCs allow for a risk-based approach, organizations must ensure any claims about the absence of prior government access requests are well-documented, certified by senior management, and supported by objective, publicly available information. Additionally, companies should establish internal procedures for handling government access requests and involve their Data Protection Officer in all international transfer evaluations.
Technology can play a key role in streamlining these compliance efforts.
Using Technology for Compliance
Automated tools can simplify compliance by mapping data flows and visualizing international transfers. These tools help organizations pinpoint data importers and identify the third countries involved. AI-powered functionalities, such as auto-populating forms, further reduce manual effort.
For businesses collecting data through online forms, platforms like Reform offer practical solutions. Features like email validation, spam prevention, and real-time analytics help ensure accurate data capture. Seamless integrations with CRM and marketing tools make it easier to track and document where data is transferred and how it is processed. By centralizing data collection with no-code form builders, companies can maintain better control over their data flows and ensure they meet documentation requirements for Transfer Impact Assessments.
Pairing these technological solutions with strong technical safeguards provides even greater protection.
Best Practices for Additional Safeguards
Technical measures, such as encryption for data in-transit and at-rest, are critical. However, the European Data Protection Board clarifies:
"Encryption would only be an effective supplementary measure if the cryptographic keys are retained solely by the data exporter, or other entities entrusted with this task that reside in the EEA or a third country that the European Commission has found to provide an adequate level of data protection".
For example, one digital credentialing platform implemented TLS 128-bit AES encryption for in-transit data and full-disk AES encryption for data at-rest. It also established protocols to challenge overly broad government requests.
In addition to encryption, contractual safeguards can enhance data protection. Tools like warrant canaries and mandatory transparency reports add layers of accountability. Organizational measures, such as obtaining data security certifications (e.g., ISO standards), conducting regular staff training, and providing clear data protection notices, further strengthen compliance frameworks.
Conclusion
The Schrems II decision reshaped the landscape of international data transfers. By invalidating the EU–US Privacy Shield, it placed Standard Contractual Clauses (SCCs) at the forefront of data transfer mechanisms to the United States. However, these clauses now come with heightened scrutiny and responsibilities. The Court of Justice of the European Union emphasized:
"it is, above all, for that controller or processor to verify, on a case-by-case basis... whether the law of the third country of destination ensures adequate protection, under EU law, of personal data transferred pursuant to standard data protection clauses".
This means compliance isn’t a one-and-done task. It requires continuous monitoring and frequent re-evaluation of data transfer practices to keep pace with evolving regulations. The shift to the 2021 SCC framework is non-negotiable, leaving organizations no room for delay. These changes present both operational challenges and legal risks.
To meet these demands, businesses must commit to detailed Transfer Impact Assessments (TIAs), implement additional safeguards, and maintain strong vendor oversight. As Eduardo Ustaran, Partner at Hogan Lovells, aptly points out:
"Entering into agreements including any of the SCCs modules should not be regarded as a 'paper exercise' as the practical implementation of the obligations will require substantial efforts from all parties involved".
Organizations can tackle these challenges with practical tools and strategies, such as conducting comprehensive risk assessments, leveraging automation for compliance tasks, and employing strong encryption protocols. For businesses collecting data online, ensuring proper validation, maintaining clear documentation, and integrating seamlessly with CRM systems are crucial steps to support Transfer Impact Assessments and maintain control over data flows.
Noncompliance is not an option. With fines reaching up to 4% of global annual turnover, the financial and reputational risks are immense. Investing in thorough assessments, robust documentation, and technical safeguards isn’t just about meeting legal requirements - it’s about staying ahead in an increasingly complex regulatory environment.
FAQs
What are Transfer Impact Assessments (TIAs) and why do they matter?
Transfer Impact Assessments (TIAs) are in-depth evaluations that organizations must carry out when transferring personal data outside the European Economic Area (EEA) using Standard Contractual Clauses (SCCs). These assessments focus on the legal and regulatory framework of the destination country, particularly scrutinizing government access to data. The goal is to ensure the data receives protection equivalent to what the GDPR requires. If the destination country’s safeguards fall short, additional measures - whether technical, contractual, or organizational - must be put in place.
The importance of TIAs stems from the Schrems II ruling, which made it clear that SCCs are only valid if the data transfer is adequately protected. Skipping this step can leave businesses exposed to serious risks: unauthorized access to personal data, regulatory fines, or even invalidation of the data transfer. By conducting a TIA, organizations can stay compliant, reduce risks, and maintain trust with both customers and regulators.
How do U.S. surveillance laws affect the use of SCCs for transferring data from the EU?
U.S. surveillance laws, including Section 702 of the Foreign Intelligence Surveillance Act (FISA) and Executive Order 12333, provide extensive authority for accessing personal data. After the Schrems II decision, companies relying on Standard Contractual Clauses (SCCs) for transferring data from the EU to the U.S. must evaluate whether these laws meet the level of protection required under EU standards.
When U.S. laws don't align with EU data protection requirements, businesses are often required to put in place extra safeguards to stay compliant. These can involve steps like encryption, pseudonymization, or stricter contractual agreements to secure personal data during transfers.
What steps can businesses take to meet SCC requirements after Schrems II?
To meet the stricter requirements for Standard Contractual Clauses (SCCs) after the Schrems II decision, businesses need to adopt a combination of technical, organizational, and contractual measures to safeguard data. The process starts with conducting a detailed transfer impact assessment (TIA) and keeping a close eye on the data importer’s legal framework over time.
Here are some key steps to consider:
- Encrypt data effectively and retain control of encryption keys locally, or use end-to-end encryption to block unauthorized access.
- Pseudonymize or tokenize personal data before transferring it to reduce risks if a breach occurs.
- Enforce strict access controls by implementing policies like least-privilege access, multi-factor authentication, and maintaining detailed audit logs.
- Limit data usage by transferring only what’s absolutely necessary and deleting it as soon as it's no longer required.
- Enhance contractual terms to oblige importers to notify exporters of government access requests, contest overly broad orders, and maintain transparency.
- Stay updated on foreign legal systems to ensure the safeguards remain effective as laws change.
By integrating these measures, businesses can align with GDPR expectations and ensure an “essentially equivalent” level of protection for EU personal data under the SCC framework.
Related Blog Posts
Get new content delivered straight to your inbox

The Response
Updates on the Reform platform, insights on optimizing conversion rates, and tips to craft forms that convert.
Drive real results with form optimizations
Tested across hundreds of experiments, our strategies deliver a 215% lift in qualified leads for B2B and SaaS companies.


.webp)








