3rd-Party Processors and PCI DSS Explained

If your business accepts credit cards, PCI DSS compliance is non-negotiable. This global standard protects cardholder data and reduces fraud risks. Non-compliance can cost businesses between $86,000 and $4 million in fines, plus reputational damage that’s hard to recover from.
Using third-party payment processors like Stripe or Adyen can simplify compliance by handling sensitive data securely. However, you still have responsibilities, such as completing annual Self-Assessment Questionnaires (SAQs) and ensuring secure integration with processors.
Key points:
- PCI DSS compliance: Required for all businesses handling card data.
- Third-party processors: Reduce your compliance burden but don’t eliminate your accountability.
- Your role: Secure your systems, use TLS 1.2+, and monitor processor compliance.
Failing to meet these standards can result in fines, legal fees, and even losing the ability to process card payments.
How to Achieve PCI DSS Compliance Quickly | Scytale
How Third-Party Processors Handle PCI DSS Compliance
PCI DSS Compliance: Processor vs Merchant Responsibilities
What Processors Are Required to Do
Leading payment processors like Adyen and Stripe hold PCI DSS Level 1 Service Provider status. This designation requires them to undergo an annual assessment by an independent Qualified Security Assessor (QSA) to confirm compliance with over 300 security controls outlined by PCI DSS.
As Stripe explains:
"Stripe is certified annually by an independent PCI Qualified Security Assessor (QSA) as a PCI Level 1 Service Provider meeting all PCI requirements".
Once cardholder data enters a payment interface - whether through an iframe, mobile SDK, or hosted checkout page - the processor takes full responsibility for its security. This includes encrypting the data at the point of capture and tokenizing it to ensure sensitive information never reaches your servers.
Processors go beyond basic data handling by maintaining secure data centers equipped with physical safeguards, firewalls, and access logs. They also focus on secure development practices and ongoing testing of payment systems to address vulnerabilities like browser-based malware. Under PCI DSS v4.0.1, which takes effect in June 2024, processors will need to meet updated standards covering mobile devices, contactless payments, and cloud infrastructure.
While processors manage the security of data capture and storage, merchants still have critical compliance responsibilities to address.
Compliance Responsibilities You Still Have
Even with the advanced security measures provided by processors, businesses are not entirely off the hook when it comes to PCI DSS compliance. Stripe highlights this shared responsibility:
"PCI compliance is a shared responsibility and applies to both Stripe and your business".
This means that while processors handle much of the heavy lifting, merchants must take proactive steps to ensure full compliance.
Merchants are required to complete an annual Self-Assessment Questionnaire (SAQ) that aligns with their specific integration method. For instance, if your business processes over 1 million card-present transactions annually, you’ll need to submit SAQ B-IP.
Additionally, you should request and retain your processor's annual Attestation of Compliance (AoC) rather than relying on generic compliance certificates.
Securing the environment before data reaches the processor is another key responsibility. This includes completing the appropriate SAQ and ensuring your website uses TLS 1.2 or higher to protect data in transit. PCI DSS Requirement 12.8 also mandates that merchants maintain an up-to-date list of service providers, conduct due diligence, and monitor compliance annually. Physical security is equally important - you must routinely inspect payment terminals for signs of tampering.
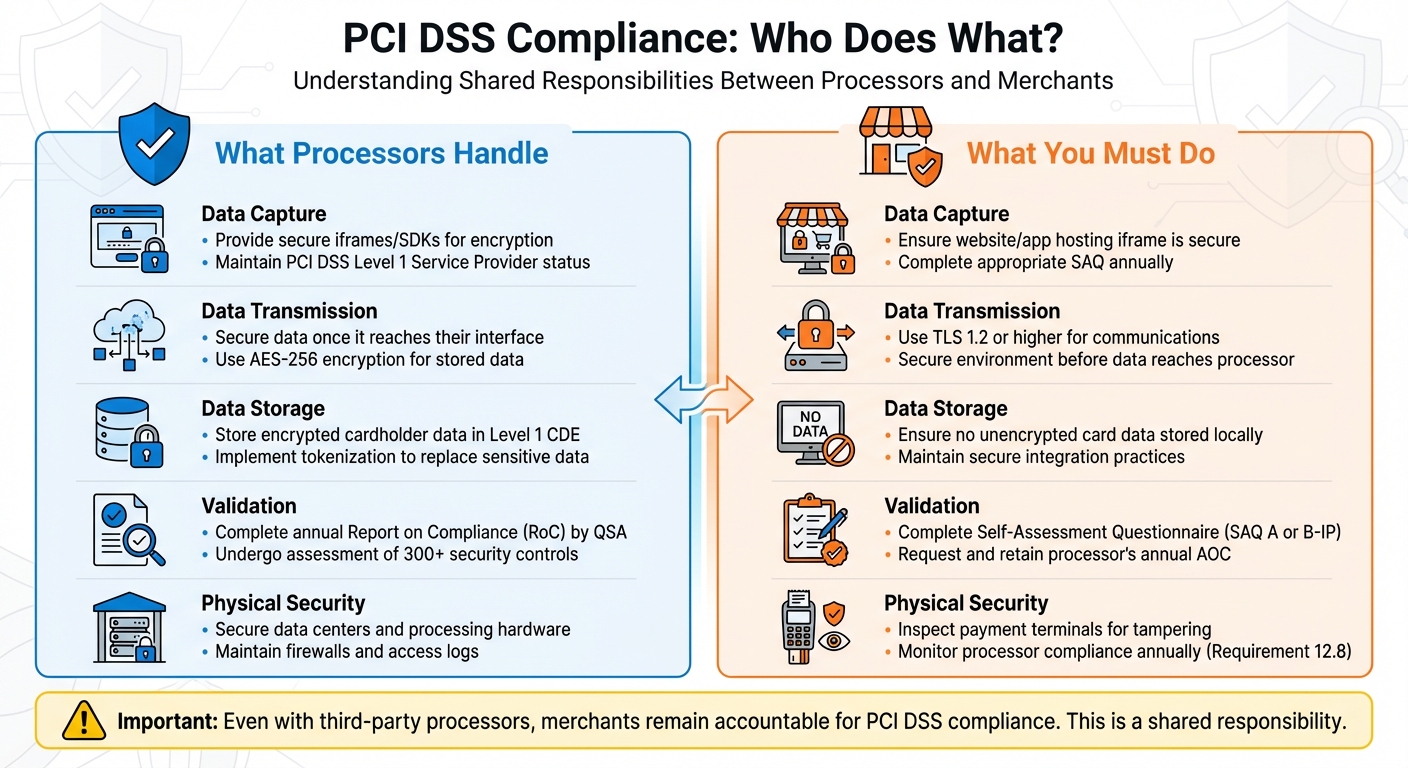
| Responsibility Area | Processor's Job | Your Job |
|---|---|---|
| Data Capture | Providing secure iframes/SDKs for encryption | Ensuring the website or app hosting the iframe is secure |
| Data Transmission | Securing data once it reaches their interface | Using TLS 1.2 or higher for server-to-processor communications |
| Data Storage | Storing encrypted cardholder data in a Level 1 CDE | Ensuring no unencrypted card data is stored locally |
| Validation | Annual Report on Compliance (RoC) by a QSA | Completing the Self-Assessment Questionnaire (e.g., SAQ A or B-IP) |
| Physical Security | Securing data centers and processing hardware | Inspecting physical payment terminals for tampering |
The 12 PCI DSS Requirements and How Processors Meet Them
The 12 Core Requirements Explained
The PCI DSS framework is built around six key goals that safeguard payment data at every stage. These goals are broken down into 12 specific requirements, which apply to anyone handling cardholder information.
- Goal 1 ensures secure networks by requiring firewalls to be installed and maintained (Requirement 1) and eliminating vendor-supplied default passwords (Requirement 2).
- Goal 2 focuses on protecting cardholder data by encrypting stored information (Requirement 3) and using strong cryptography for data transmission over public networks (Requirement 4).
- Goal 3 addresses vulnerability management by requiring anti-virus software (Requirement 5) and timely application of security patches (Requirement 6).
- Goal 4 enforces access controls through need-to-know restrictions (Requirement 7), unique user IDs with multi-factor authentication (Requirement 8), and physical security measures (Requirement 9).
- Goal 5 emphasizes continuous monitoring by logging access and tracking activity (Requirement 10) and conducting regular vulnerability scans and annual penetration tests (Requirement 11).
- Goal 6 calls for formal security policies, ongoing risk assessments, and regular staff training (Requirement 12).
As the PCI Security Standards Council puts it:
"PCI DSS provides a baseline of technical and operational requirements designed to protect payment account data."
Next, let’s look at how processors implement these requirements in real-world settings.
How Processors Implement These Requirements
Processors address these 12 requirements using a layered security strategy that aligns with each of the six goals. For network security, they deploy firewalls to filter unauthorized traffic and isolate the cardholder data environment (CDE) from other systems. They also replace default settings with strict configurations to prevent vulnerabilities.
To protect data, processors rely on encryption and tokenization. They commonly use AES-256 encryption for stored data and TLS 1.2 or higher for secure transmissions. Tokenization is another key tool, replacing sensitive card data with non-exploitable tokens. For example, Stripe employs tokenization across its global systems while maintaining an impressive 99.999% uptime.
Access control measures include multi-factor authentication (MFA), which is mandatory under PCI DSS v4.0 as of March 31, 2025. Processors also assign unique user IDs, enforce role-based access restrictions, and secure data centers with physical safeguards like badge access and video monitoring.
Continuous monitoring is achieved through automated audit trails that log user actions and flag suspicious activity in real time. Processors conduct quarterly vulnerability scans and annual penetration tests to identify and address security gaps. Audit logs are retained for at least one year, with the most recent three months readily accessible for review, as required by PCI DSS.
Lastly, processors uphold formal security policies, conduct annual risk assessments, and maintain incident response plans. These efforts not only ensure compliance with PCI DSS but also minimize potential risks to your business.
sbb-itb-5f36581
How to Choose a PCI-Compliant Payment Processor
Check Their Compliance Documentation
Start by requesting the relevant compliance documents from the payment processor. These include the Attestation of Compliance (AOC), Report on Compliance (ROC) for Level 1 processors, or SAQ-D for Level 2 processors. These documents confirm that the processor has met the requirements of PCI DSS and are essential for verifying compliance. Make sure the scope of these documents specifically covers the services you plan to use.
Visa has strict rules for service providers listed on their Global Registry, requiring validation of PCI DSS compliance:
"PCI DSS compliance validation by a QSA is required before a service provider can be listed on the Visa Global Registry of Service Providers (the Registry)."
Cross-check the processor’s name against the Visa Global Registry of Service Providers to ensure they are in good standing. Additionally, ask for evidence of quarterly vulnerability scans conducted by an Approved Scanning Vendor (ASV), as outlined in PCI DSS Requirement 11.
Once you’ve confirmed the documentation, turn your attention to how securely the processor integrates with your systems.
Assess Security Risks
When evaluating a payment processor, pay close attention to how they handle integration to minimize the risk of exposing sensitive card data. Look for options like hosted payment fields or checkout pages, which ensure that sensitive data doesn’t touch your servers. Also, confirm that the processor uses TLS 1.2 or higher and employs tokenization to secure transactions.
Keep in mind that compliance isn’t a one-and-done process. Request updated compliance documentation annually, as an AOC is only valid for 12 months. Remember, while the processor secures the payment infrastructure, you’re still responsible for maintaining safe integration practices and robust internal security controls.
Here’s a quick breakdown of the key compliance documents you should review:
| Document Type | Purpose | Required For |
|---|---|---|
| Attestation of Compliance (AOC) | Confirms compliance status | All Processors/Service Providers |
| Report on Compliance (ROC) | Detailed audit report by a QSA | Level 1 Processors (>300,000 transactions) |
| SAQ-D for Service Providers | Self-assessment compliance questionnaire | Level 2 Processors (<300,000 transactions) |
| ASV Scan Results | Proof of external vulnerability testing | Entities with external-facing IPs |
Benefits and Risks of Using Third-Party Processors
Why Businesses Use Third-Party Processors
Third-party processors take on much of the responsibility for PCI DSS compliance, which can lighten the load for businesses. When these processors handle the transmission and storage of sensitive cardholder data, your company no longer needs to secure that information within your own systems. In many cases, this allows businesses to demonstrate compliance through a straightforward Self-Assessment Questionnaire (SAQ) instead of navigating a full-scale audit.
These processors often have security systems that go well beyond what most businesses could realistically build on their own. For instance, they use tokenization - a method that replaces sensitive credit card details with non-sensitive tokens. These tokens can be safely stored on your servers without exposing actual card data. By removing cardholder data from your environment, the risk of breaches is significantly reduced.
Additionally, modern processors automate a range of security measures, such as phishing prevention and audit logging. This automation minimizes manual effort, allowing you to focus on your primary business activities while reducing overall risk. For small and medium-sized businesses, outsourcing payment handling to specialists is a practical way to avoid the complexities of maintaining advanced security systems.
What Happens When Processors Aren't Compliant
While third-party processors can reduce your PCI DSS scope, their non-compliance can have serious consequences for your business. Here's the hard truth: outsourcing payment processing doesn’t eliminate your liability. Even if the processor handles all the technical aspects, you remain accountable for protecting cardholder data. If a processor fails to maintain compliance and a breach occurs, your business bears the fallout.
The financial repercussions can be staggering. Monthly fines from acquiring banks can range from $5,000 to $100,000, and card networks may impose penalties of up to $500,000 per incident. In addition, you'll likely face forensic audit expenses to determine the cause of the breach. Other costs include replacing compromised cards, which can run $3 to $5 per card, along with legal fees and compensation for affected customers, such as credit monitoring or identity theft insurance.
Beyond financial penalties, payment brands might limit or even terminate your ability to process card transactions. The statistics are alarming: 60% of small and medium-sized businesses that experience a data breach shut down within six months. Even more concerning, 61% of organizations are unsure whether their third-party partners would notify them of a breach, and 50% don’t actively monitor third parties with access to sensitive information.
Non-compliance can also land your business on the Member Alert to Control High-Risk (MATCH) list, effectively barring you from processing card payments for years. For businesses that rely on card transactions, this could be a death sentence. Ensuring your processor is compliant isn’t just a good practice - it’s critical for staying in business.
Key Takeaways
Here’s what you need to know to manage your PCI DSS compliance effectively:
-
Check your processor’s Attestation of Compliance (AOC): Make sure it’s up-to-date for PCI DSS v4.0 or v4.0.1, as older versions are no longer valid. As Natasja Bolton, Client Engagement Manager at VikingCloud, explains:
"The AOC is essentially your vendor's compliance résumé. And like any résumé, you need to scrutinize compliance details".
- Outsourcing doesn’t mean zero responsibility: Even when you outsource, you’re still liable. Ensure your contracts include a responsibility matrix that clearly outlines which PCI DSS requirements are managed by the processor and which fall on you.
-
Compliance is an ongoing task: AOCs expire every 12 months, so it’s essential to verify their status annually. Consider automating reminders to stay on top of this. Ken Van Allen, Technical Lead at Schellman, highlights this point:
"PCI DSS compliance is a continuous process, not just a point in time exercise".
- Choose processors wisely: Opt for processors that provide full redirection or iFrame-based forms, enabling you to qualify for SAQ A. Confirm that their AOC covers the specific services, locations, and configurations you’re using.
- Evaluate subcontractor management and incident response: Review your processor’s approach to managing subcontractors, breach notification timelines, and how they integrate with your incident response plan. Keep in mind that around 15% of system intrusion incidents involve vulnerabilities exploited through partners.
FAQs
What should businesses know about their responsibilities for PCI DSS compliance when using third-party payment processors?
When working with third-party payment processors, businesses remain accountable for maintaining PCI DSS compliance. Here's what you need to focus on:
- Do your homework: Investigate the processor's security practices and confirm their compliance with PCI DSS standards.
- Check their credentials: Ensure the processor has validated their PCI DSS compliance and meets all required benchmarks.
- Clarify responsibilities: Clearly outline which compliance duties the processor handles and which ones stay with your business.
- Keep records: Maintain documentation of the processor's compliance status as part of your own compliance records.
Even if payment processing is outsourced, businesses must stay actively involved in managing compliance to safeguard customer data and adhere to PCI DSS requirements.
How do I confirm if a payment processor complies with PCI DSS?
To verify that a payment processor complies with PCI DSS standards, request their latest Attestation of Compliance (AOC) or validation report. Then, double-check their status by confirming they’re listed as a validated provider - such as a Level 1 service provider - on the official PCI Security Standards Council directory. This process is a key part of ensuring proper due diligence when engaging with third-party processors.
What risks do businesses face if their third-party payment processor is not PCI DSS compliant?
If your third-party payment processor doesn't uphold PCI DSS compliance, your business could be exposed to serious risks, such as:
- Data breaches that compromise sensitive customer payment details.
- Hefty fines or legal troubles stemming from non-compliance.
- Fraudulent transactions or unauthorized access to financial accounts.
- Erosion of customer trust, which can tarnish your business's reputation.
These issues don’t just create immediate challenges - they can leave lasting scars on your operations and relationships with customers. Ensuring your payment processor complies with PCI DSS standards is a key step in protecting both your business and your customers' sensitive information.
Related Blog Posts
Get new content delivered straight to your inbox

The Response
Updates on the Reform platform, insights on optimizing conversion rates, and tips to craft forms that convert.
Drive real results with form optimizations
Tested across hundreds of experiments, our strategies deliver a 215% lift in qualified leads for B2B and SaaS companies.


.webp)








