Top Tools for CPNI Compliance

Customer Proprietary Network Information (CPNI) compliance is critical for telecom companies to protect sensitive customer data and meet FCC regulations. Noncompliance can result in hefty fines, as seen with AT&T and Sprint in 2024. Here’s a quick breakdown of the key tools and strategies to ensure compliance:
- Consent Management: Tools like Reform simplify customer consent collection with secure forms, audit trails, and CRM integration.
- Data Protection: DLP solutions, encryption software, and monitoring platforms safeguard sensitive information and track access.
- Access Control: Role-Based Access Control (RBAC) systems limit data access based on roles, reducing risks.
- Call Recording Systems: Automated platforms ensure all customer interactions are securely logged and compliant with FCC requirements.
Quick Tip: The annual FCC certification deadline is March 1. Tools that automate reporting and maintain detailed records are essential to avoid compliance risks and reduce audit preparation time.
These tools not only address legal obligations but also help telecom providers build trust by prioritizing data security.
Webinar: Privacy By Design - Building Solutions for CPNI Compliance
Reform for Consent Management and Form Security

Securing and documenting customer consent is a must for complying with CPNI regulations. Michael Kansky, Founder of HelpSquad, explains:
A key part of CPNI compliance is obtaining customer consent. Telecom companies need clear permission - through written, online, or verbal consent - to use or share CPNI.
Reform’s no-code form builder simplifies this process by creating secure forms that generate audit trails and provide the documented proof telecom companies need for their annual FCC certifications, due by March 1.
The platform’s multi-step form feature separates CPNI consent agreements from general terms and conditions, making it easier to capture the "affirmative consent" mandated by the 2007 FCC CPNI Order. Conditional routing further customizes the authorization process, tailoring it to specific consent requirements based on the type of service.
Reform also includes real-time email validation to ensure contact details are accurate from the start. This is crucial because carriers must notify customers at their "address of record" whenever there are changes to their account or password. These measures help establish a strong legal foundation for customer communication, which is increasingly important as regulatory fines and class action settlements for unlawful communication are expected to hit $3.3 billion by 2025.
To further streamline operations, Reform’s CRM integrations automatically sync consent data into central systems. Every form submission is logged with timestamps and customer details, ensuring compliance during regulatory audits. Progressive profiling helps build customer records gradually, avoiding overwhelming new users.
With features like conditional logic, validated data collection, and seamless CRM syncing, Reform makes consent management more efficient. Telecom companies can confidently demonstrate they’ve obtained proper consent while maintaining the detailed records the FCC requires.
Next, we’ll dive into tools for data protection and monitoring to enhance CPNI security even further.
Data Protection and Monitoring Tools
Protecting CPNI (Customer Proprietary Network Information) goes beyond simply obtaining customer consent. Telecom companies need specialized tools to prevent data breaches, safeguard sensitive information, and maintain the detailed audit trails required for FCC compliance. Here’s a closer look at three essential tools - DLP solutions, encryption software, and monitoring platforms - that work together to strengthen CPNI security.
Data Loss Prevention (DLP) Solutions
DLP tools are designed to stop unauthorized sharing of CPNI by monitoring how data moves across networks. Modern DLP systems now incorporate data lineage, which tracks the journey of information - from its origin in a CRM system, for example, to its destination in an external email or AI tool. This method significantly reduces false-positive alerts, cutting them by 90% compared to older systems that relied solely on content analysis.
Effective DLP platforms typically focus on three key areas:
- Blocking unauthorized actions in real time
- Detecting unusual data movements
- Analyzing high-risk behaviors
As companies increasingly use AI tools, the risk of inadvertently exposing CPNI to large language models grows. Advanced monitoring capabilities are now critical to prevent such incidents. While DLP tools help prevent leaks, encryption ensures that sensitive data remains secure, even if accessed.
Encryption Software for CPNI Security
Encryption is a cornerstone of CPNI protection, safeguarding data both when it’s stored and while it’s being transmitted. This aligns with FCC confidentiality requirements under Section 222. Michael Kansky, Founder of HelpSquad, highlights its importance:
"Encryption adds a strong security layer, making it tough for attackers to access or read the data".
To maximize security, encryption tools should integrate with Identity and Access Management (IAM) systems. This ensures that only authorized personnel can decrypt sensitive information, reinforcing the strict access controls required by the FCC. These measures are especially critical in light of recent enforcement actions. For instance, in 2024, TracFone Wireless paid a $16 million settlement, and AT&T faced a $13 million penalty after a breach exposed data for roughly 9 million customers through a vendor’s cloud environment.
Monitoring and Audit Platforms
Security Information and Event Management (SIEM) platforms play a vital role in tracking and analyzing CPNI access. By collecting log data from multiple sources, these tools provide real-time alerts when data is accessed outside of normal patterns. Advanced systems now include User and Entity Behavior Analytics (UEBA), which establish baselines for typical employee behavior, making it easier to detect insider threats or compromised accounts.
These platforms also simplify compliance with FCC regulations. They can automate the annual certification process and generate required reports, such as those documenting consumer complaints about unauthorized data disclosures. Additionally, by storing historical logs, these tools support forensic investigations, enabling companies to reconstruct attack timelines and understand how breaches occurred.
Access Control and Call Recording Systems
Managing access to Customer Proprietary Network Information (CPNI) and keeping thorough records of customer interactions are key to meeting FCC compliance standards. Telecommunications companies need systems that not only block unauthorized access to sensitive data but also maintain detailed logs of customer communications. These measures help meet regulatory requirements while protecting against both external threats and internal misuse.
Role-Based Access Control (RBAC) Systems
RBAC systems limit access to CPNI by assigning permissions based on job roles rather than individual users. For instance, a customer support agent might only have access to the information needed to handle basic inquiries, while a financial director could have broader permissions related to billing. This follows the principle of least privilege, reducing the exposure of sensitive data to unnecessary risks.
FCC regulations also mandate that employees cannot access CPNI until the customer has been properly authenticated. Tyler Reese, VP of Product Management at Netwrix, highlights the importance of this approach:
RBAC minimizes the attack surface since users are restricted to only the privileges required for their specific roles, in accordance with the principle of least privilege.
Modern RBAC systems often include hierarchical models, where higher-level roles inherit permissions from lower-level ones, allowing oversight without requiring complex configurations. Advanced systems may also use constrained RBAC, enforcing separation of duties to prevent fraud. For example, ensuring no single employee can both initiate and approve a SIM card change request is a critical safeguard against SIM swap fraud. Additional security measures like regular access reviews and multi-factor authentication further enhance protection.
When combined with secure consent management, RBAC forms a strong foundation for safeguarding CPNI. These access controls also complement call recording systems, which provide additional layers of security and compliance.
Automated Call Recording Platforms
Automated call recording platforms are crucial for creating the compliance audit trails required by the FCC. These systems log every customer interaction, making them invaluable for reviews and investigations. Many platforms use techniques like data masking (e.g., auto-pause during sensitive moments) to ensure unnecessary Personally Identifiable Information (PII) isn’t stored.
To secure the recordings, platforms incorporate public-key encryption, RBAC for access control, and detailed audit logs. They also support retention management, enabling companies to automatically delete outdated recordings or retain them for over seven years, as regulations may require. Live monitoring features allow supervisors to check whether agents are adhering to CPNI policies and address any potential issues, such as phone misuse. By centralizing all interactions into a single, compliant system, these platforms help streamline FCC certification processes while ensuring data security.
sbb-itb-5f36581
Comparison of Top CPNI Compliance Tools
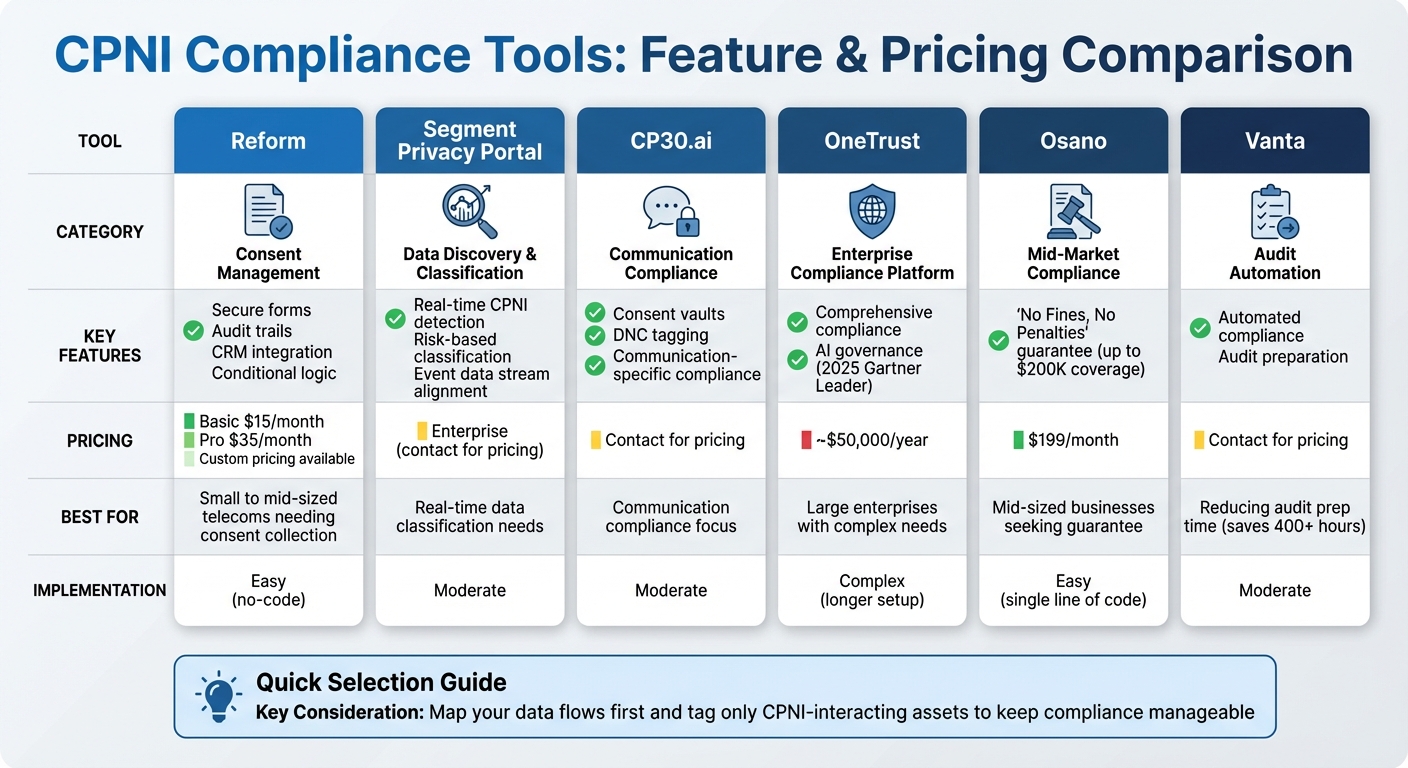
CPNI Compliance Tools Comparison: Features, Pricing, and Best Use Cases
Selecting the right tool for CPNI compliance boils down to understanding your telecom needs, budget, and existing infrastructure. Each platform brings something different to the table, whether it's consent management, data classification, or streamlined reporting.
For managing customer permissions and secure form collection, Reform offers a straightforward solution. It allows telecom providers to capture consent right at the initial point of contact. Pricing starts at $15/month for the Basic plan, while the Pro plan, at $35/month, includes team access and advanced CRM integrations.
When it comes to data discovery and classification, tools like Segment's Privacy Portal stand out. This platform detects and classifies CPNI in real time, assigning risk-based classifications to data points. Rudy Martin, Chief Information Security Officer at Segment, highlights:
Segment's Privacy Portal aligns event data streams with strict privacy standards.
For telecoms focusing on communication-specific compliance, CP30.ai delivers unique features like consent vaults and Do Not Call (DNC) tagging. These capabilities are particularly relevant given the projected $3.3 billion in regulatory fines and settlements for unlawful customer communication by 2025.
At the enterprise level, platforms like OneTrust provide all-encompassing compliance solutions. Recognized as a Leader in the 2025 Gartner Market Report for AI Governance Platforms, OneTrust starts at around $50,000 per year. For mid-sized businesses, Osano offers a more affordable option at $199/month, with a standout "No Fines, No Penalties" guarantee that pledges up to $200,000 in coverage if compliance fails.
Some tools, like Cookiebot and Osano, are easy to implement, requiring just a single line of code. In contrast, enterprise platforms like OneTrust may involve longer setup times but provide more comprehensive solutions. These options reflect the broad range of tools available, from nimble solutions to enterprise-grade platforms.
To ensure effective CPNI security, telecom providers should first map out their data flows. Focus on tagging only those assets that interact with Customer Proprietary Network Information to keep compliance manageable. Tools like Vanta can further simplify the process, with automation features that reportedly save over 400 hours in audit preparation.
Reform Pricing and Implementation for Telecoms
Reform offers three pricing options designed to help telecom providers stay compliant with regulations.
The Basic Plan starts at $15 per month and includes features like unlimited form responses, conditional logic, and integrations with popular tools such as Google Sheets and Zapier. This plan is ideal for smaller telecom providers that need simple opt-in forms to collect customer consent efficiently.
The Pro Plan, priced at $35 per month, goes a step further by offering team access and advanced CRM integrations, including HubSpot. This plan is especially useful for providers that need to synchronize Customer Proprietary Network Information (CPNI) consent across multiple systems and maintain detailed audit trails. Considering the FCC's $16 million settlement with TracFone Wireless in 2024 over CPNI violations, having automated CRM documentation can help mitigate compliance risks significantly.
For larger telecom providers with more complex needs, the Done for You plan provides custom pricing. This option includes forms designed by FunnelEnvy experts, tailored to meet the intricate authentication requirements of carriers. These forms can handle tasks like collecting and verifying customer PINs before granting access to sensitive data like billing or call detail records. Together, these pricing tiers make it easier for telecom providers to integrate compliance tools seamlessly while adhering to regulatory standards.
To implement Reform for CPNI compliance, start by creating secure forms that capture affirmative consent, as outlined in the 2007 FCC CPNI Order. Map these form fields directly to your CRM system to ensure customer consent preferences are automatically updated and an audit trail is established. This is critical for meeting the FCC’s annual certification deadline on March 1. Additionally, configure role-based access controls within your CRM integration to ensure that only authorized personnel can view sensitive data collected through Reform forms.
Another key step is enabling real-time notification triggers to alert customers whenever their CPNI-related information is updated via a Reform submission. This level of transparency not only builds customer trust but also aligns with the FCC’s expectation for providers to exceed minimum compliance requirements. With regulatory fines projected to hit $3.3 billion by 2025 for improper customer communication practices, investing in a reliable consent management system is not just a legal requirement - it’s also a smart financial decision. This approach strengthens your overall CPNI compliance strategy while safeguarding your operations from costly penalties.
Conclusion
Protecting Customer Proprietary Network Information (CPNI) is not just a regulatory requirement under Section 222; it's also a smart business move. Recent FCC fines serve as a stark reminder of the financial risks tied to noncompliance. By leveraging the right tools, businesses can shift from labor-intensive manual processes to automated, reliable systems that safeguard both customer data and their own financial health.
Modern compliance platforms make this transformation possible by automating tasks like continuous monitoring and evidence collection. Features such as PIN verification, automated customer notifications, and role-based access controls ensure the security of sensitive data like call records, billing details, and usage patterns - meeting stringent FCC standards. With 85% of organizations acknowledging that compliance has grown more complex over the past three years, automation has become a necessity rather than a luxury.
"Always-on" security systems also streamline audit preparation, cutting compliance audit times by as much as 82%. This eliminates the last-minute rush before the annual March 1 certification deadline. Additionally, with breach notification rules requiring alerts within 7 business days for incidents impacting 500 or more customers, real-time monitoring is no longer optional - it's essential.
Reform takes compliance to the next level with its consent management features, robust data protection tools, encryption capabilities, and call recording systems. Together, these elements form a comprehensive framework that addresses every aspect of CPNI regulations. By integrating Reform into their compliance strategy, telecom companies can not only avoid costly penalties but also strengthen customer trust through reliable data protection.
FAQs
What tools are essential for ensuring CPNI compliance in telecom companies?
Telecom companies rely on a variety of tools to meet the FCC’s Customer Proprietary Network Information (CPNI) regulations. One essential tool is a consent management system, which securely captures and stores customer authorizations before any use or sharing of their CPNI. Another critical component is identity verification tools - like password-protected portals or multi-factor authentication - that ensure only authorized individuals can access sensitive account information.
Protecting CPNI during storage and transmission requires encryption and data-loss prevention (DLP) solutions, while audit logging provides a record of access events, ensuring accountability. To streamline compliance efforts, policy-management software helps oversee certifications, manage policies, and handle breach reporting. Equally important are employee training programs, which equip staff with the knowledge to handle sensitive data responsibly and follow best practices for safeguarding customer information.
Together, these tools create a robust framework for compliance and protecting customer data within the U.S. telecom industry.
How does Reform help telecom companies collect customer consent for CPNI compliance?
Reform makes it easier for telecom companies to gather customer consent for Customer Proprietary Network Information (CPNI) compliance. It provides customizable, easy-to-use forms that align with CPNI regulations, ensuring clear communication and adherence to legal requirements.
The platform includes features like conditional routing, email validation, and spam prevention to streamline the consent collection process. Plus, its smooth integration with marketing and CRM tools simplifies managing and tracking consent records, helping businesses stay aligned with FCC regulations without added hassle.
Why is encryption important for safeguarding Customer Proprietary Network Information (CPNI)?
Encryption plays a key role in safeguarding sensitive CPNI, including call details, location data, and service usage information, by rendering it unreadable to anyone without proper authorization. This practice aligns with FCC regulations and helps prevent unauthorized access or data exposure.
For telecommunications companies, encrypting data not only protects customer privacy but also minimizes the chances of security breaches. This approach strengthens customer trust while ensuring compliance with legal requirements.
Related Blog Posts
Get new content delivered straight to your inbox

The Response
Updates on the Reform platform, insights on optimizing conversion rates, and tips to craft forms that convert.
Drive real results with form optimizations
Tested across hundreds of experiments, our strategies deliver a 215% lift in qualified leads for B2B and SaaS companies.


.webp)








