Vendor Contract Checklist for Compliance

When managing vendor contracts, compliance is non-negotiable. It helps protect your organization from data breaches, regulatory penalties, and operational risks. A structured checklist ensures vendors meet legal, security, and performance standards. Here's what you need to know:
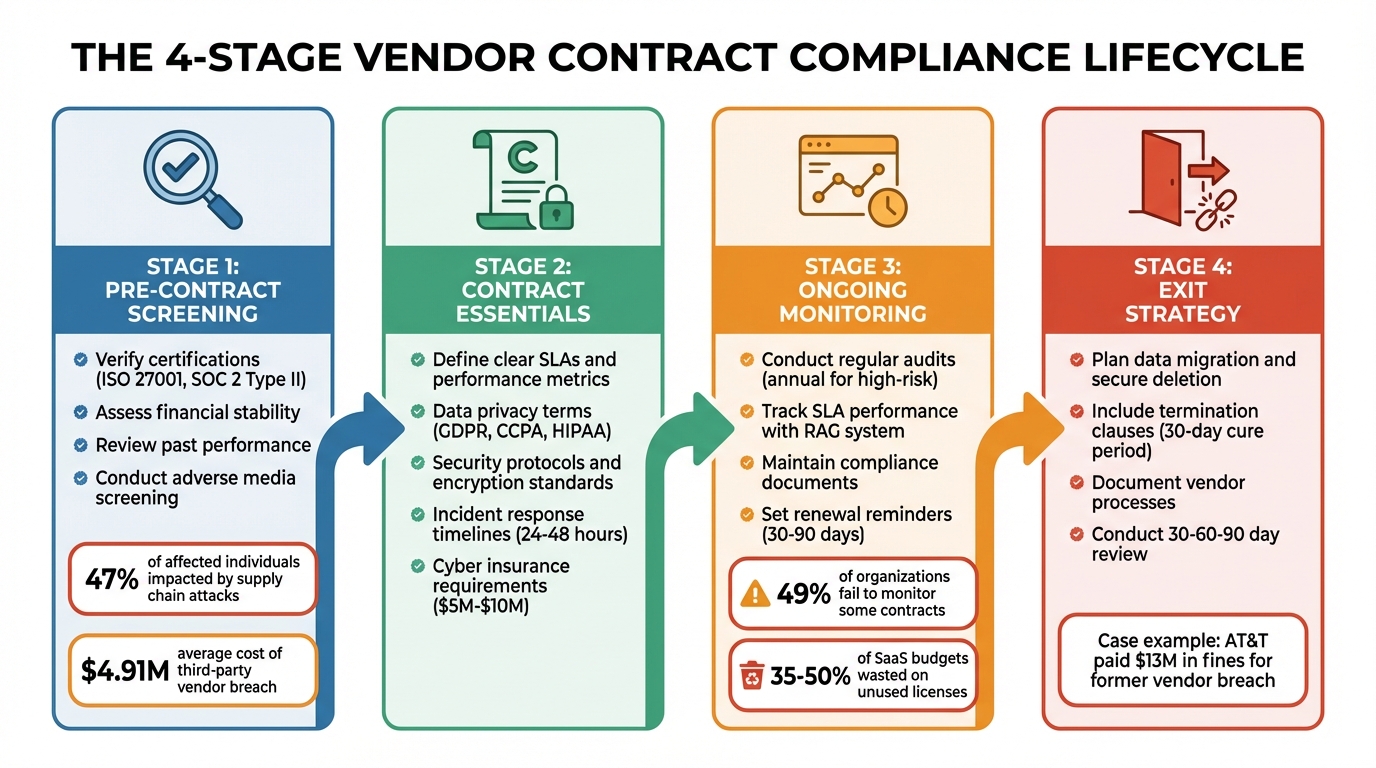
- Pre-Contract Screening: Verify certifications (e.g., SOC 2 Type II, ISO 27001), assess financial stability, and review past performance.
- Contract Essentials: Define clear SLAs, data privacy terms, security protocols, and incident response timelines. Include indemnification clauses and cyber insurance requirements.
- Ongoing Monitoring: Conduct regular audits, track SLA performance, and maintain up-to-date compliance documents. Use tools to centralize vendor data.
- Exit Strategies: Plan for data migration, ensure secure deletion, and outline clear termination clauses to minimize disruptions.
A well-managed vendor contract process reduces risks and ensures accountability throughout the vendor lifecycle.
4-Stage Vendor Contract Compliance Checklist Process
Contract Lifecycle Management Software Checklist
Pre-Contract Vendor Screening Checklist
Before signing any vendor contract, it’s crucial to ensure the vendor can deliver on its promises and meet compliance standards. This requires more than just reviewing their marketing materials - you’ll need to perform independent verification using public databases, registries, and external monitoring tools. The goal here is to classify vendors by risk level - Critical, High, Medium, or Low - so you can determine the depth of due diligence required. A solid starting point is confirming their adherence to industry standards and certifications.
Verify Credentials and Certifications
Begin by requesting industry-standard certifications such as ISO 27001, which focuses on information security management, and SOC 2 reports for system and organization controls. Keep in mind, not all SOC 2 reports are created equal. A Type 1 report provides a snapshot of controls at a specific moment, while a Type 2 report evaluates those controls over a period of 3 to 12 months. Since SOC 2 reports tend to lose relevance after about 12 months, ensure any report you review is current.
If the vendor handles sensitive data, confirm their compliance with relevant regulations like GDPR, CCPA/CPRA, or HIPAA/HITECH, depending on your industry and location. For vendors working with government-related or cloud services, check for adherence to standards like NIST SP 800-53 or ISO/IEC 19086-1. Additionally, ask for their Written Information Security Program (WISP), which should outline their physical, administrative, and technical safeguards.
Assess Reputation and Past Performance
Credentials are important, but they’re only part of the picture. Dig deeper into the vendor’s reputation and track record. Go beyond testimonials by conducting an adverse media screening to uncover any controversies, legal issues, or prior security incidents. Reach out to industry peers who have firsthand experience with the vendor to gather honest feedback about their performance. You can also use external security rating platforms to evaluate their IP reputation, patch management, and network security, which are often scored on an A-F scale.
The statistics highlight the risks: supply chain attacks impacted 47% of all affected individuals in the first half of 2025, and the average cost of a third-party vendor breach is $4.91 million. This reality has shifted the industry’s mindset from "trust but verify" to a more cautious "verify then maybe trust" approach. Validate SOC 2 Type II results for a 6- to 12-month snapshot of their control performance, and ensure they have the legal right to use any data they handle by verifying their data lineage.
Evaluate Financial and Operational Stability
Compliance is essential, but so is ensuring the vendor’s financial and operational health. Review their balance sheets, income statements, and cash flow reports to confirm they can meet long-term commitments. For startups or smaller vendors, check their credit scores and funding status to assess any risk of insolvency. High-risk vendors should undergo financial reviews annually, while lower-risk vendors might only require reviews every two to three years.
Operational stability is equally important. Examine their infrastructure and verify they have documented Business Continuity and Disaster Recovery plans with proven RPO (Recovery Point Objective) and RTO (Recovery Time Objective) metrics. Look at historical uptime data and SLA performance, aiming for uptime commitments of 99.5% to 99.9%. It’s also worth noting that 43% of workers admit to making mistakes that compromise security, so review the vendor’s internal processes for change management and release protocols to minimize human error risks.
Core Contractual Obligations Checklist
After vetting your vendor, the next step is to ensure your contract includes clear, measurable compliance requirements. This is where many organizations falter - relying on vague assurances instead of setting precise expectations. As Reena Bajowala, Data Security and Privacy Partner at Ice Miller, explains:
"Contract provisions should attempt to transfer whatever risk the company is not able to mitigate on its own".
Your contract is your key tool for managing vendor risks, so every clause should be actionable and specific. These guidelines align with earlier vendor screening steps, helping ensure ongoing compliance and reducing risks.
Define Scope, SLAs, and Performance Metrics
Using insights from your vendor screening, outline the services, deliverables, and timelines in detail. Specify who is responsible for delivering these services - whether it’s the vendor, their affiliates, or subcontractors.
Set performance expectations as measurable service levels or KPIs instead of vague terms. For example, rather than saying "timely support", state that critical issues must receive a response within 2 hours and standard issues within 8 hours. Also, clarify what your organization must provide - like access to facilities, staff availability, or necessary data - to help the vendor fulfill their obligations.
Include provisions for audits and performance monitoring, allowing for regular assessments. Require that any identified shortcomings be addressed within a defined timeframe. Additionally, ensure that all security and compliance requirements apply not only to the vendor but also to any subcontractors they engage.
Outline Data Privacy and Sharing Policies
Start by defining terms such as "Personal Information" and "Sensitive Personal Information", referencing regulations like GDPR, CCPA, or CPRA.
For GDPR compliance, your contract should specify the subject matter, duration, nature, and purpose of data processing, as well as the types of personal data and categories of data subjects involved. Vendors must act only on documented instructions unless legally required otherwise. If you’re subject to CCPA, include clauses that prohibit vendors from selling or sharing personal information.
Sub-processor management is another critical element. Require vendors to get written approval before hiring sub-processors and ensure those sub-processors follow the same data protection rules. Contracts should also obligate vendors to support data subject rights requests - like access, deletion, or portability - through defined technical and organizational measures.
For international data transfers, prohibit moving data outside the EEA or UK without your prior consent and proper safeguards, such as Standard Contractual Clauses. At the end of the contract, specify whether data should be returned or deleted, and reserve the right to review and approve any breach notifications the vendor sends to affected parties.
Include Security and Incident Management Protocols
Security measures should be explicitly stated. Require vendors to maintain a Written Information Security Program (WISP) that outlines their physical, administrative, and technical safeguards. Specify encryption standards for data both at rest and in transit, and include requirements for timely vulnerability patching and multi-factor authentication.
Define what qualifies as a "security incident", covering both suspected and confirmed breaches. Vendors should notify you of major incidents within 24 hours and confirmed breaches within 48 hours. Include details about how incidents should be reported, who to contact, and how often updates should be provided during an active investigation.
Clearly allocate financial and legal responsibilities. Determine who bears the costs for forensics, legal counsel, credit monitoring, and remediation. Common industry practices include requiring vendors to carry cyber liability insurance of $5 million, with some contracts setting breach indemnification amounts as high as $10 million. Lastly, mandate thorough investigations, root cause analyses, and cooperation with internal teams, regulators, law enforcement, and insurers.
sbb-itb-5f36581
Compliance and SLA Monitoring
Once you've established solid contractual terms, the next critical step is systematic monitoring to ensure vendors stick to their promises. A strong contract only holds value if backed by consistent oversight. As Reena Bajowala, Data Security and Privacy Partner at Ice Miller, aptly states:
"A perfectly written contract is only useful for ensuring data security if the company continues to check on its vendors to ensure ongoing compliance."
This is where many organizations stumble. Nearly half (49%) of organizations fail to monitor some of their contracts, leading to missed compliance checks and unexpected renewals. Without proper monitoring, you're essentially relying on vendors to self-report issues - a risky gamble that can leave your business exposed. Ongoing monitoring bridges the gap between what’s written in the contract and what’s actually being delivered.
Conduct Regular Audits and Reviews
Start by scheduling audits based on vendor risk levels. Vendors managing sensitive data or critical systems should undergo annual reviews, while medium-risk vendors might only need assessments every two years. However, don’t stop at scheduled reviews - trigger immediate reassessments after major events like security breaches, product changes, acquisitions, or the addition of new sub-processors.
When reviewing documents like SOC 2 Type II reports, don’t just accept them as-is. Look for exceptions or findings, map them to your specific use case, and confirm that remediation steps have been taken with tangible evidence.
Centralize all vendor-related documents - contracts, amendments, SOC reports, ISO certifications, insurance certificates, and more - in a single, searchable repository. This ensures that all stakeholders have a clear and comprehensive view of vendor compliance.
Track SLA Performance Metrics
To ensure vendors meet their obligations, compare their reports against internal data like ticketing logs and uptime dashboards. Use a Red/Amber/Green (RAG) system to visualize compliance:
- Green: Full compliance (e.g., all certificates are current, SLA targets are met).
- Amber: Warning signs (e.g., upcoming certificate expirations, minor performance dips).
- Red: Major issues (e.g., expired documents, consistent SLA failures).
For example, if a certificate is nearing expiration (Amber status), automated workflows can notify the responsible team to request updated documentation.
| Monitoring Category | Green (Compliant) | Amber (Cautionary) | Red (Non-Compliant) |
|---|---|---|---|
| Compliance | All certificates/SOC reports current | Key documents nearing expiry | Documents expired; regulatory failure |
| SLA Performance | All targets met; uptime achieved | Minor performance dips; occasional delays | Consistent SLA failures; major outages |
| Data Privacy | DPA current; sub-processors verified | Data incomplete; needs review | Data missing/outdated; breach of terms |
Set automated renewal reminders - 30, 60, or 90 days in advance - and begin renegotiations 90 to 120 days before contracts expire.
Document and Address Compliance Gaps
For any compliance gaps, assign internal owners and deadlines to resolve them. Vendors should provide concrete proof of corrections, such as updated policies, penetration test results, or evidence of vulnerability management. Contracts should clearly define how deficiencies must be addressed and how corrective actions are communicated. For instance, if a vendor delays breach notification (e.g., notifying you 72 hours after detection instead of the agreed 48 hours), document the delay, its impact, and the corrective steps required.
Pay attention to the total cost of the relationship (TCR), not just the contract’s sticker price. Hidden expenses - like implementation hours, usage-based fees, or the internal time spent managing the vendor - can significantly inflate costs. Companies often waste 35% to 50% of their SaaS budgets on unused or underutilized licenses. Effective compliance monitoring can help uncover and address these inefficiencies.
Lastly, ensure Data Processing Addendums (DPAs) are up to date. If a DPA predates regulatory updates like CCPA or GDPR, initiate amendments to align with current laws. Vendors should also notify you when they add new sub-processors, allowing you to verify whether these third parties meet your security standards.
Exit Strategy for Non-Compliant Vendors
A thorough exit strategy is critical when vendors fail to meet compliance standards, despite rigorous contract monitoring.
Even with strong contracts and diligent oversight, non-compliance can still occur. When a vendor repeatedly fails to meet SLA commitments or regulatory requirements, having a clear plan to terminate the relationship is essential to safeguard your business. Without a well-defined exit strategy, you risk operational disruptions, data breaches, and legal liabilities. As Maria Yiannitsarakos, Esq., Strategic Legal Counsel, emphasizes:
"Negotiating termination clauses upfront provides flexibility and a clear process for exiting the contract helping prevent potential disputes and complications."
Consider the case of AT&T. In January 2023, the company faced a data breach involving a former cloud vendor that impacted 8.9 million wireless customers - years after the vendor contract had ended. This breach resulted in AT&T paying $13 million in FCC fines and implementing stricter data handling protocols for both current and former vendors. Similarly, in 2020, Morgan Stanley incurred a $60 million fine for failing to oversee a third-party vendor responsible for decommissioning hardware, which led to the exposure of sensitive customer data.
Include Termination Clauses in Contracts
Termination clauses should be carefully crafted to address both major failures and repeated minor breaches, such as missed SLA targets, delayed incident reporting, or non-compliance with critical regulations. These clauses should also establish a cure period (commonly 30 days) and outline notice requirements (e.g., 30, 60, or 90 days via certified mail or email).
Contracts should mandate vendors to return all data in a "commonly readable program" format, settle any financial obligations, and provide transitional support to onboard a replacement vendor. Additionally, they should grant the right to conduct third-party audits and ensure that subcontractors adhere to the same security and compliance standards.
Plan for Data Migration and Continuity
When initiating termination, safeguarding your data is a top priority. Follow these steps to ensure a smooth transition:
- Retrieve all essential datasets, processed reports, and analytics before revoking the vendor’s access. Cooperation often diminishes once access is cut, making data recovery more challenging.
- Obtain a written certificate confirming the secure deletion of all data, including backups and copies stored on employee devices.
- Document vendor-managed processes, custom scripts, and workarounds. Ensure all service accounts, credentials, and technical access (e.g., VPNs, API keys, cloud links) are handed over and deactivated.
- Extend survival clauses to maintain data protection, confidentiality, and audit rights beyond the termination date.
For example, in 2021, Lexington Medical Center faced a data breach involving archived patient records, including Social Security numbers, stored by their former vendor, Healthgrades Operating Company. Although the hospital had transitioned to a new provider, the failure to ensure secure deletion of the old vendor’s backup files resulted in significant costs and liabilities.
Once data is secured and continuity measures are in place, focus on transitioning to a compliant replacement vendor.
Establish a Vendor Replacement Process
To find a suitable replacement, evaluate potential vendors using a risk rubric based on the sensitivity of the data they’ll handle (e.g., PII, PHI, financial information) and the criticality of their services to your business. Collaborate with legal, IT, and business teams to create a master timeline that ensures a seamless transition without service interruptions. Be vigilant about identifying shadow IT, unauthorized integrations, and orphaned credentials to avoid disruptions.
After the transition, conduct a 30-60-90 day review to monitor for issues like failed logins or broken integrations. Verify final invoices against your records to catch any unexpected exit fees or data export charges. Poor vendor offboarding can lead to hidden costs, sometimes inflating the total expense of the vendor relationship by 30% to 70%.
Conclusion
Managing vendor contract compliance is an ongoing process that requires careful planning, well-structured contracts, and consistent oversight. Every phase of the vendor lifecycle, from initial screening to exit strategies, plays a critical role in protecting your business from risks like data breaches, regulatory penalties, and operational setbacks.
A well-organized checklist can simplify this process by streamlining tasks and ensuring no detail is overlooked. These checklists not only improve efficiency and accuracy but also help allocate liability appropriately. They also enhance supply chain transparency by ensuring compliance terms are extended to subcontractors, effectively addressing potential weak points in your vendor network.
Experts emphasize the importance of regular contract reviews to keep up with changing regulations and business priorities. High-risk vendors should be reassessed annually, while medium-risk relationships should undergo reviews every two years.
FAQs
What certifications should you check when screening vendors before signing a contract?
When you're assessing vendors before committing to a contract, it's crucial to ensure they meet important industry standards or legal requirements. Depending on your industry and the type of data involved, certifications like HIPAA, FERPA, FISMA, or PCI DSS should be on your radar.
These certifications indicate that the vendor prioritizes security, privacy, and compliance. Confirming these credentials helps ensure the vendor meets your organization's expectations and reduces potential risks tied to non-compliance.
What are the best practices for monitoring vendor compliance after signing a contract?
To keep vendors compliant after a contract is signed, it's crucial to set up ongoing monitoring processes. This means regularly checking how well the vendor is meeting their contractual commitments, such as adhering to data privacy standards, following security protocols, and fulfilling service level agreements (SLAs). Periodic evaluations, like audits, security reviews, and assessments of certifications (e.g., SOC reports), are key to verifying compliance.
Contracts should also clearly spell out monitoring expectations, reporting responsibilities, and the consequences of falling short. Open and consistent communication with vendors is essential. If there are any changes in their practices or security measures, addressing them quickly can reduce risks and ensure they remain accountable.
What should be included in an exit strategy for vendors who fail to meet compliance standards?
An effective plan for handling non-compliant vendors should prioritize minimizing risks and ensuring a secure transition. The first step? Revoke all access the vendor has to your systems, data, and infrastructure. This means deactivating API keys, disabling login credentials, and shutting down any other access points. Doing this promptly helps prevent unauthorized use or potential security breaches.
The next critical step is to review and address any contractual obligations tied to data security and privacy. Double-check that the vendor has adhered to relevant legal and regulatory requirements, such as GDPR or CCPA. Clearly document any remaining responsibilities, like breach notifications or remediation actions, to avoid misunderstandings and ensure accountability.
Lastly, keep detailed records of the offboarding process. Thorough documentation not only proves compliance but also helps protect your organization from future legal or security issues. By following these steps, you can secure your operations and ensure a smooth exit process with minimal risk.
Related Blog Posts
Get new content delivered straight to your inbox

The Response
Updates on the Reform platform, insights on optimizing conversion rates, and tips to craft forms that convert.
Drive real results with form optimizations
Tested across hundreds of experiments, our strategies deliver a 215% lift in qualified leads for B2B and SaaS companies.


.webp)



