Checklist for Monitoring Vendor Privacy Risks

Vendors can be a major privacy risk if not monitored properly. They often handle sensitive data like PII or PHI, and a single weak link can lead to breaches, fines, or reputational damage. This checklist provides actionable steps to assess and monitor vendor privacy risks throughout the relationship - from onboarding to reassessment.
Key Points:
- Categorize Vendors by Risk: Assign vendors to Low, Medium, High, or Critical tiers based on the sensitivity of data they handle.
- Verify Security Controls: Request evidence like SOC 2 Type II reports, penetration test summaries, and incident response plans.
- Monitor Sub-Processor Changes: Require vendors to notify you before adding or changing sub-processors.
- Set Reassessment Schedules: High-risk vendors need annual reviews, while medium-risk vendors can be reviewed every two years.
- Document Everything: Maintain a centralized audit trail for compliance and oversight.
Why this matters: Regulations like GDPR and CCPA demand strict vendor oversight. With 35.5% of breaches in 2024 involving third-party compromises, continuous monitoring is essential to protect your organization.
This guide walks you through every step, from initial assessments to ongoing reviews, ensuring you stay ahead of risks and maintain compliance.
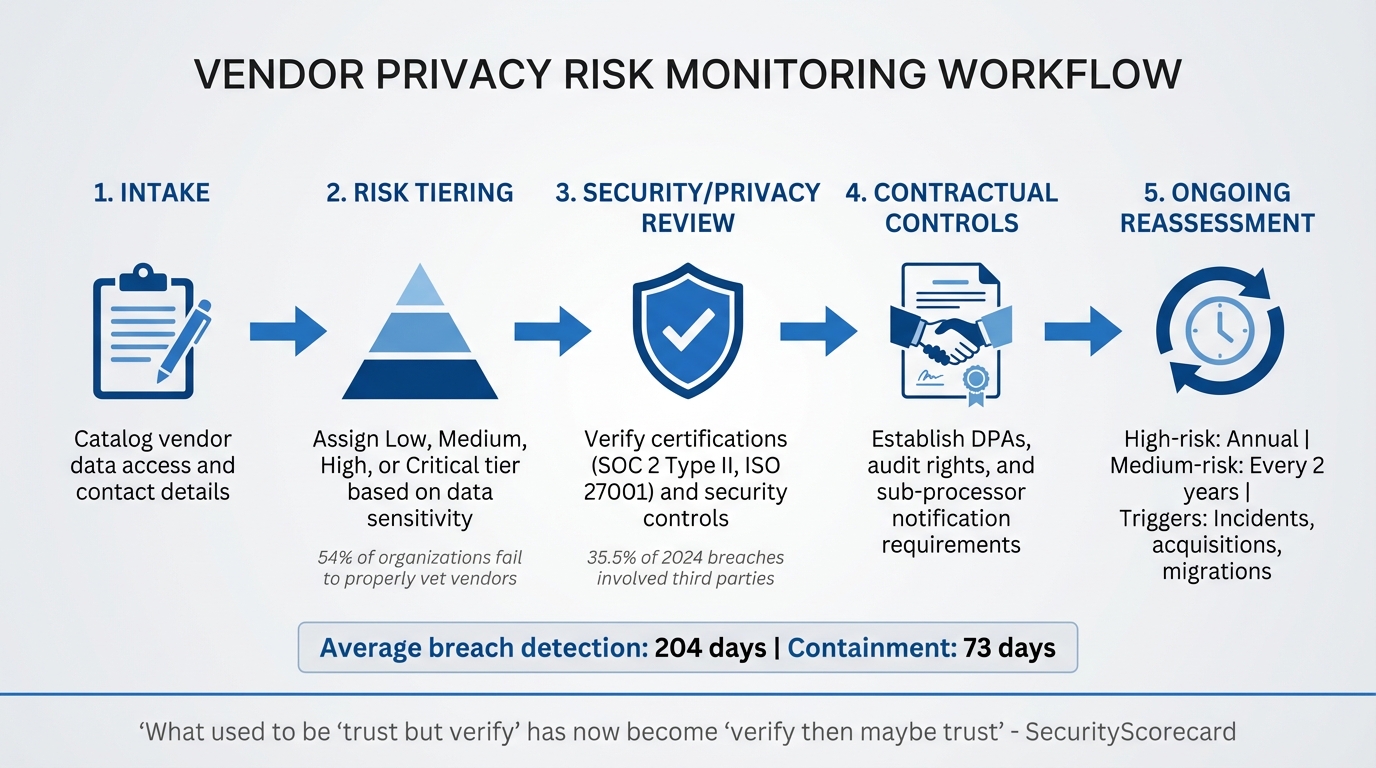
5-Step Vendor Privacy Risk Monitoring Workflow
Initial Vendor Assessment
Data Inventory and Risk Tiering
Before entering an agreement, it's crucial to map out the vendor's data landscape. This includes documenting their contact details, risk owners, services, systems, and most importantly, the types of data they handle - like PII (Personally Identifiable Information), PHI (Protected Health Information), or intellectual property. Also, note where this data is stored and how long it’s retained.
This inventory lays the groundwork for risk tiering. Not all vendors carry the same level of risk. For instance, a marketing tool that doesn’t access customer names is far less concerning than a payment processor managing credit card information. The numbers paint a stark picture: in 2024, 35.5% of data breaches stemmed from third-party compromises, while 41% of ransomware attacks exploited third-party access points. Alarmingly, 54% of organizations still fail to properly vet their vendors.
Vendors should be categorized into Low, Medium, High, or Critical tiers based on the sensitivity of the data they handle and their impact on operations. For example:
- Low-risk vendors deal with non-sensitive data and require minimal vetting, like a basic security questionnaire.
- High-risk vendors, which process sensitive data like PII, demand a deeper dive, including SOC 2 Type II reports, penetration test results, and incident response plans.
Here’s how evidence requirements scale with risk:
| Risk Tier | Data/Impact Criteria | Minimum Evidence Required |
|---|---|---|
| Low | No sensitive data; low operational impact | Basic privacy policy, security questionnaire |
| Medium | Business data; internal integrations | SOC 2 Type I or II, DPA, penetration test summary |
| High/Critical | PII, regulated data, mission-critical services | SOC 2 Type II, penetration test results, incident response plan |
By standardizing this intake process and capturing the vendor’s data footprint before signing a contract, you eliminate surprises down the road. This approach ensures you can tailor the depth of your review to the vendor's risk tier.
Review Privacy Certifications and Policies
Once vendors are tiered, it’s time to verify their security claims with solid evidence. For medium and high-risk vendors, start with a SOC 2 Type II report. Unlike Type I, which provides a point-in-time snapshot, Type II covers a longer period - typically six to twelve months. Ensure the report’s scope includes the services and systems you’re purchasing. If the report is outdated, request a bridging letter to cover the gap.
For international vendors, check for ISO/IEC 27001 certification, which demonstrates adherence to information security management standards. If the vendor processes PII in public cloud environments, look for ISO 27018. Industry-specific certifications are equally crucial: HIPAA/HITRUST for healthcare, PCI DSS for payment processing, or FedRAMP for government-related services.
Beyond certifications, review the vendor’s Data Processing Addendum (DPA). This document outlines critical details like processing instructions, data categories, sub-processor management, and breach notification timelines. Under GDPR and similar regulations, a DPA is mandatory. For international data transfers, ensure Standard Contractual Clauses (SCCs) are in place. If the vendor handles PHI, a Business Associate Agreement (BAA) under HIPAA is also required.
Ask for additional operational policies, such as:
- Incident Response Plan: Includes breach notification timelines.
- Business Continuity and Disaster Recovery Plans: Demonstrates their ability to maintain operations during disruptions.
- Vulnerability Management Policy: Details scanning schedules and patch timelines for critical issues.
These documents are vital. In 2024, breaches took an average of 204 days to detect and 73 days to contain. You need vendors who can act quickly and effectively.
"A single vendor's weakness can compromise an entire ecosystem." - SaltyCloud Research Team
Lastly, request a comprehensive list of the vendor’s sub-processors and ensure they have a notification process for any changes. Your risk isn’t limited to the vendor - it extends to their entire supply chain.
sbb-itb-5f36581
Security and Privacy Monitoring
Monitor Security Controls
Once you've onboarded a vendor, it's important to keep a close eye on their security measures. Regular monitoring is your best defense against potential data threats.
Start with Identity and Access Management (IAM). Ensure vendors enforce Multi-Factor Authentication (MFA) for privileged accounts and offer Single Sign-On (SSO) for administrative users. Their Role-Based Access Control (RBAC) should stick to the principle of least privilege - users should only access what’s necessary for their role. Ask for access logs or IAM policy excerpts to confirm these protections.
Next, focus on data protection. Vendors should encrypt data both in transit and at rest using AES-256 encryption. Dive into their key management practices, checking for regular key rotation and secure storage. Request architecture diagrams to better understand their data protection measures.
Also, verify that vendors conduct routine vulnerability scans and adhere to strict timelines for patching critical issues. Ask for penetration test summaries and patch management logs to evaluate their security monitoring.
A strong incident response plan is essential. Vendors should notify you of breaches within 24–72 hours and maintain centralized logging with defined retention periods. They should also have 24/7 alerts for critical events. To assess their readiness, request incident logs and root cause analysis reports.
Finally, ensure that vendors consistently meet regulatory standards and maintain their security controls over time.
Verify Regulatory Compliance
Regulatory compliance is non-negotiable. Vendors must adhere to laws like GDPR, CCPA, or HIPAA, depending on the data they handle.
For vendors managing sensitive data, conduct annual reassessments for high-risk vendors and review medium-risk vendors every two years. When evaluating SOC 2 Type II reports, make sure the coverage period matches your risk timeline. If there’s a gap between the report’s end date and the current date, ask for a bridging letter to confirm their controls stayed effective.
Your Data Processing Agreement (DPA) should include clear audit rights or alternatives, such as access to SOC reports or certifications. It should also outline breach notification timelines, data retention policies, and vendor responsibilities for responding to regulatory inquiries or data subject requests.
Be proactive. If security incidents, acquisitions, system migrations, or new sub-processors arise, treat these as triggers for immediate reassessments. Regularly review the vendor’s updated privacy policies, certifications, or trust marks to confirm they remain compliant.
Track Sub-Processor Changes
Your vendor’s ecosystem matters just as much as their own operations. Sub-processors - third parties your vendor relies on - can introduce risks if not properly managed.
Make sure your DPA requires vendors to notify you before adding new sub-processors. A 30-day notice period is common, and you should retain the right to object if the sub-processor doesn’t meet your security or privacy standards.
"Determine whether subprocessors are contractually bound to equivalent obligations." - DataGrail
Ensure that sub-processors are contractually required to follow the same privacy and security standards as your vendor. The vendor should remain fully accountable for their sub-processors’ compliance, leaving no room for ambiguity.
Treat new sub-processor additions as material changes. Don’t wait for an annual review - verify their certifications and agreements immediately. If the sub-processor operates in another jurisdiction, confirm that appropriate data transfer mechanisms, like Standard Contractual Clauses, are in place.
Documentation and Assurance Reviews
Review Compliance Reports
When reviewing a SOC 2 report, make sure it's a Type II report and that its coverage period aligns with your risk timeline. Confirm that the services you rely on are explicitly included in the audit scope. This step ensures the report is relevant to your operations.
Pay close attention to any exceptions noted in the report. These exceptions could signal potential risks. Create a list of these exceptions and evaluate their significance to your business. Are they minor issues, or could they introduce unacceptable risks to your operations?
"SOC 2 reports are useful only if you confirm scope, period, exceptions, and what controls you must operate." - NMS Consulting
Another critical element to review is the Complementary User Entity Controls (CUECs). These are the security measures you are responsible for implementing to ensure the vendor's protections function effectively. Without these controls in place, the vendor's assurances might not hold up. For each CUEC, document it clearly and assign someone on your team to oversee its implementation.
Additionally, review other security documentation like penetration test summaries, vulnerability assessments, and training logs. For example, ask for evidence of regular security awareness training for the vendor’s employees. This is vital, as 43% of employees admit to making security-related mistakes at work. Depending on the type of data your vendor handles, collect proof of compliance with regulations like GDPR, HIPAA, or PCI DSS.
All these findings should be documented thoroughly to build a record that supports ongoing oversight and creates a seamless transition to maintaining a comprehensive audit trail.
Maintain an Audit Trail
Once you've reviewed the reports, every action and decision should be meticulously recorded in a centralized audit trail. This documentation is critical for regulatory compliance and ensures you have a clear record of your evaluative processes. It also demonstrates Board oversight, which auditors often require.
"When auditors review risk assessments, they need documentation proving the evaluative process as well as Board oversight." - SecurityScorecard
Your audit trail should capture everything: vendor risk tier assignments, compliance reports you've reviewed, exceptions you've validated, and responsibilities for operating Complementary User Entity Controls. Include records of sub-processor lists and any objections raised about new additions. This approach ties in with your earlier monitoring steps and ensures alignment.
Treat your audit trail as a dynamic document - it should grow and adapt with each vendor interaction. To streamline this process, use standardized templates for questionnaires, approvals, and sign-offs. This consistency not only simplifies future assessments but also helps maintain a clear, organized view of your vendor portfolio. A well-maintained audit trail can also uncover hidden risks, especially during events like mergers or acquisitions.
Set Up a Reassessment Schedule
Determine Reassessment Frequency
The frequency of vendor reassessments should align with their risk tier. For high-risk vendors - those managing sensitive data like personally identifiable information (PII), regulated data, or critical systems - an annual review is essential. Medium-risk vendors, which handle business data or integrate with internal systems, can be reassessed every two years. Meanwhile, low-risk vendors with limited access to sensitive information may only need reassessment at contract renewal or when significant changes occur.
The extent of a vendor's integration with your systems also plays a role. Even if a vendor falls into a lower risk tier, their deep integration into your infrastructure might justify more frequent evaluations. Similarly, vendors onboarded quickly or heavily embedded in your operations may require closer monitoring.
| Risk Tier | Reassessment Frequency | Trigger for Immediate Review |
|---|---|---|
| High Risk (PII, mission-critical systems) | Annual | Security incident, acquisition, new sub-processor, system migration |
| Medium Risk (Business data) | Every 2 years | Major product change, new data type being processed |
| Low Risk (No sensitive data) | On renewal or material change | Significant policy update or reported breach |
In addition to scheduled reassessments, you should be prepared to conduct immediate reviews when major changes or incidents occur.
Respond to Material Changes
Beyond routine assessments, certain events demand immediate action. These include security breaches, corporate acquisitions, the introduction of new sub-processors, significant product updates, or system migrations. Such "material changes" require prompt reassessment to ensure continued compliance and security.
To address these scenarios, include protective measures in your vendor contracts. For instance, add "right-to-audit" clauses and require vendors to notify you of material changes, such as updates to sub-processor lists or data handling policies. Clearly outline these triggers in your agreements to avoid misunderstandings. For critical vendors, establish joint incident response plans and escalation procedures to handle security events efficiently.
To stay ahead, consider using automated tools that monitor security ratings and send real-time alerts if a vendor's performance declines or their certifications lapse. These tools can help you act quickly and maintain oversight without relying solely on scheduled reviews.
The Basics of Vendor Risk Assessments Webinar
Final Checklist
Summarize your ongoing vendor privacy oversight with the checklist below.
Key Takeaways
Keeping vendor privacy risks in check requires continuous effort, backed by a well-organized process, thorough documentation, and constant vigilance. The best way to approach this is through a structured workflow: Intake, Risk Tiering, Security/Privacy Review, Contractual Controls, and Ongoing Reassessment. This ensures that each vendor gets the right level of scrutiny based on the sensitivity of data they manage and their involvement with your systems.
Risk-based tiering plays a crucial role, shaping how often vendors are reviewed, as discussed earlier. It's equally important to evaluate both technical and operational safeguards, including workforce training and access management practices.
As SecurityScorecard aptly put it, "What used to be considered 'trust but verify' has now become 'verify then maybe trust.'" This highlights the need to go beyond basic trust and require solid proof - like SOC 2 Type II reports, penetration test summaries, or vulnerability management logs. Point-in-time assessments should also be paired with real-time monitoring tools that can detect security lapses before they turn into incidents. Automation can be a game-changer here, helping you identify declines in vendor security quickly and efficiently.
Below is a streamlined checklist to reinforce these monitoring steps.
Complete Monitoring Checklist
This checklist outlines the critical actions needed to manage vendor privacy risks effectively - from the initial evaluation to ongoing oversight.
Initial Assessment
- Catalog vendor data access and assign a risk tier (High, Medium, or Low).
- Confirm privacy certifications (e.g., SOC 2 Type II, ISO 27001) and review their privacy policies.
- Ensure robust encryption is in place (e.g., AES for data at rest and in transit) and multi-factor authentication is enforced.
Ongoing Monitoring
- Track sub-processor changes and enforce objection rights as needed.
- Regularly review updated compliance reports and verify remediation of noted exceptions.
- Monitor security incidents via online searches and vendor notifications.
- Verify that patching schedules meet agreed service levels, especially for critical vulnerabilities like zero-day threats.
Documentation & Contracts
- Establish Data Processing Agreements (DPAs) with clearly defined breach notification timelines.
- Document audit rights and termination procedures, including data export and deletion processes.
- Maintain a centralized system to track vendor status, risk tiers, and reassessment schedules.
Reassessment Schedule
- High-risk vendors: Conduct reviews annually.
- Medium-risk vendors: Conduct reviews every two years.
- Initiate immediate reassessments for material changes, such as security breaches, acquisitions, new sub-processors, or system migrations.
AI-Specific Considerations (if applicable)
- Confirm whether customer data is used for model training and ensure opt-out options are available.
- Verify retention periods for prompts and outputs.
- Assess controls designed to mitigate prompt injection vulnerabilities.
FAQs
What’s the best way to categorize vendors based on risk?
To sort vendors by risk effectively, start with a clear and organized risk assessment process. This means evaluating each vendor’s security protocols, privacy practices, and compliance with regulations that apply to your industry. Pay close attention to critical areas like how they handle data, their breach notification policies, and any relevant certifications they’ve earned. It’s also important to revisit these assessments regularly, especially after significant changes like system updates or acquisitions.
Once assessments are complete, group vendors into risk categories such as high, medium, or low. The level of risk often depends on their access to sensitive data or critical systems. For instance, vendors managing highly confidential data may need tighter controls, such as frequent audits or stronger contract terms, like requiring cyber liability insurance. Taking a methodical approach ensures you can focus your resources where they’re needed most, reducing third-party risks in a practical way.
What evidence should I ask for to confirm a vendor’s security measures?
To evaluate a vendor's security measures, ask for essential documentation like their security policies, SOC reports, and any privacy certifications or trust seals they possess. It's also important to request details about their incident response plans - specifically how they handle data breaches and recovery processes. Reviewing this information ensures the vendor aligns with your compliance and security requirements before finalizing any agreements.
How often should I review high-risk vendors for privacy risks?
Regularly reviewing high-risk vendors is essential to ensure they continue to meet your privacy and security standards. Setting a consistent review schedule - whether quarterly, annually, or based on the vendor's risk level - can help you stay on top of potential issues.
Beyond routine checks, it's important to reassess vendors after major changes. These could include mergers, acquisitions, system upgrades, or incidents that might affect how they handle data. Taking a proactive approach not only safeguards your business but also helps you stay aligned with privacy regulations.
Related Blog Posts
Get new content delivered straight to your inbox

The Response
Updates on the Reform platform, insights on optimizing conversion rates, and tips to craft forms that convert.
Drive real results with form optimizations
Tested across hundreds of experiments, our strategies deliver a 215% lift in qualified leads for B2B and SaaS companies.


.webp)



