GDPR Compliance: Anonymized Data in Forms
If your business collects data through forms, understanding GDPR rules is critical. GDPR applies to any information that can identify an individual, but fully anonymized data is exempt from its regulations. This means if you anonymize form data properly, you can avoid strict compliance requirements while still using the data effectively.
Here’s what you need to know:
- Anonymized data: Cannot be linked to an individual and is not subject to GDPR.
- Pseudonymized data: Uses codes or references but can still identify individuals and remains under GDPR.
- Key risks: Indirect identifiers (like ZIP codes or age) can lead to re-identification when combined with other data.
- Methods to anonymize: Techniques like adding noise, generalization, or synthetic data generation can protect privacy while keeping data useful.
Failing to anonymize data correctly can result in penalties, as seen in cases like Netflix and Taxa 4×35. By using the right techniques and monitoring risks, you can ensure compliance and maintain user trust.
Data protection in research practice I - Key terms of the GDPR
What GDPR Says About Anonymized Data
GDPR Anonymization vs Pseudonymization: Key Differences and Compliance Requirements
How GDPR Defines Anonymized Data
Under GDPR, data protection rules do not apply to information that cannot be linked to an identified or identifiable person. Recital 26 of the regulation states:
"The principles of data protection should therefore not apply to anonymous information, namely information which does not relate to an identified or identifiable natural person or to personal data rendered anonymous in such a manner that the data subject is not or no longer identifiable."
For data to be considered truly anonymized, it should be impossible to identify an individual using any reasonable method. This includes evaluating factors like the cost, time, and technology required to reverse the anonymization. If re-identification is feasible, even with effort, the data remains subject to GDPR rules.
Take the Netflix example from 2006: the company shared a dataset of 500,000 movie ratings, assuming it was anonymized. However, researchers from the University of Texas at Austin managed to re-identify specific users by matching the Netflix data with public IMDb profiles. This case illustrates how linkability can compromise anonymization efforts.
It’s also worth noting that anonymizing data is itself considered a processing activity under GDPR. Organizations must ensure they have a lawful basis to perform this task. Proper anonymization typically involves securely deleting the original identifiable data rather than merely storing it separately.
This distinction between anonymized and reversible data forms the foundation for understanding how GDPR differentiates between anonymization and pseudonymization.
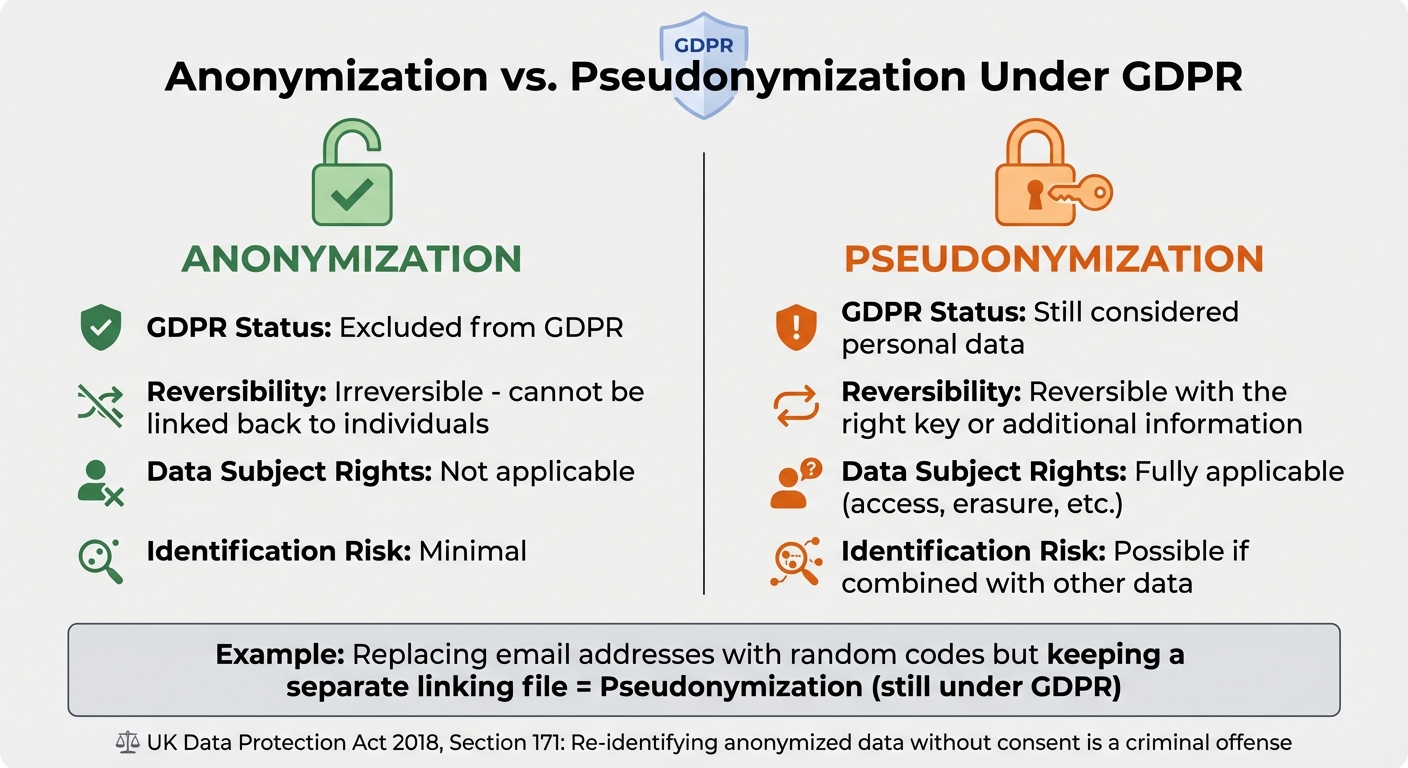
Anonymization vs. Pseudonymization
Anonymization and pseudonymization serve different purposes under GDPR. While anonymization ensures the permanent removal of any link to an individual, pseudonymization only conceals identifiers, keeping the data under GDPR's scope. GDPR makes a clear distinction between these two methods. Pseudonymized data is still considered personal data because it can be reconnected to an individual when combined with other information. The Information Commissioner's Office explains:
"Pseudonymisation refers to techniques that replace, remove or transform information that identifies people, and keep that information separate... It is not a way of transforming personal data to the extent the law no longer applies."
Here’s a quick comparison of the two:
| Feature | Anonymization | Pseudonymization |
|---|---|---|
| GDPR Status | Excluded from GDPR | Still considered personal data |
| Reversibility | Irreversible | Reversible with the right key |
| Data Subject Rights | Not applicable | Fully applicable (access, erasure, etc.) |
| Identification Risk | Minimal | Possible if combined with other data |
For example, if you replace email addresses in a dataset with random codes but maintain a separate file linking those codes to the original emails, the data is pseudonymized, not anonymized. In this case, GDPR obligations, including data subject rights and retention limits, still apply.
Additionally, under Section 171 of the UK Data Protection Act 2018, re-identifying anonymized data without the controller’s consent is a criminal offense. This reinforces the importance of ensuring anonymization is genuinely irreversible to avoid legal and ethical risks.
Common Problems with Form Data Collection
Indirect Identifiers and Re-Identification Risks
Forms often collect data points that, while seemingly harmless on their own, can reveal identities when pieced together. These indirect identifiers - like IP addresses, location details, age, or ZIP codes - can combine through what's known as the mosaic effect to identify individuals uniquely. For example, a form might skip asking for a name but still collect a user's city, age range, and a specific medical condition. Together, these details could narrow down the individual to a single person within a group. The key issue lies in how easily someone can be singled out from a larger population.
One common blind spot for businesses is the "motivated intruder" test - a scenario where someone with access to public records and a strong intent to identify individuals could succeed. Research highlights just how fragile anonymized data can be: 99.98% of anonymized datasets risk re-identification when cross-referenced with other information sources. For instance, a publicly available house purchase price of $500,000 might suggest the homeowner earns around $100,000 annually, transforming what seems like an innocuous record into personal data.
Recognizing these risks is crucial before applying anonymization strategies to your forms.
Examples of Compliance Failures
Real-world examples reveal how quickly form data collection can go awry. Take Taxa 4×35, a Danish taxi company. After an audit, it was fined for retaining GPS coordinates and pickup/drop-off data for five years, even though customer names had been removed. This oversight made it possible to re-identify individuals, violating GDPR rules.
The risks aren't limited to traditional forms. In June 2025, a breach at Central Maine Healthcare exposed sensitive data for 145,381 individuals, including names, birth dates, and Social Security numbers. These incidents prove that simply removing direct identifiers - like names - doesn't ensure compliance or data safety.
Such examples emphasize the importance of integrating strong anonymization techniques into your data collection processes to avoid similar pitfalls.
Methods for Anonymizing Form Data
These techniques address the risks of re-identification by breaking or weakening the connections between data and individuals, ensuring privacy without compromising the dataset's utility.
Randomization Methods
A couple of practical randomization techniques include:
- Noise addition: This involves introducing small, random variations to numerical data. For example, slightly altering salary figures can mask exact values while preserving the dataset's overall statistical patterns. This allows trends to be analyzed without exposing individual details.
- Data swapping: Also known as permutation, this method exchanges attribute values between records. For instance, swapping ZIP codes between two form submissions can obscure specific locations while maintaining a useful geographic distribution for analysis.
These approaches help obscure personal details while retaining the dataset's analytical value.
Generalization Methods
Generalization reduces the precision of data to make re-identification more difficult. For example, instead of storing a full birthdate like "March 15, 1985", you could retain only the year "1985" or categorize it into an age range, such as "35-40".
A popular framework in this category is K-anonymity, which ensures that each record is indistinguishable from at least k other records. For instance, if k is set to 5, every unique combination of attributes will appear for at least five individuals.
Other advanced generalization methods include:
- L-diversity: Enhances K-anonymity by requiring that sensitive attributes within each group have a minimum number of distinct values, reducing the risk of inference attacks.
- T-closeness: Ensures that the distribution of sensitive attributes within a group closely mirrors the overall dataset, further safeguarding privacy.
Advanced Methods
For more robust anonymization, advanced techniques like the following are often employed:
- Differential privacy: Widely regarded as a gold standard, this method adds carefully calibrated noise - often using Laplacian or Gaussian distributions - to query results. It ensures that the inclusion or exclusion of an individual's data has minimal impact on the output. The level of privacy is controlled by a "privacy budget" (ε), where a lower ε provides stronger protection.
- Synthetic data generation: Machine learning is used to create entirely artificial datasets that mimic the statistical properties of the original data. These synthetic datasets are highly resistant to re-identification but can be complex to generate and may slightly reduce the utility of the data.
Here's a quick comparison of these methods:
| Technique | Re-identification Resistance | Data Utility | Complexity |
|---|---|---|---|
| Noise Addition | High | High | Medium |
| Data Swapping | High | Medium | Medium |
| Generalization | High | Medium | Medium |
| Differential Privacy | Very High | Medium-High | High |
| Synthetic Data | Very High | Medium | High |
These tools provide a solid foundation for anonymizing form data, ensuring privacy while maintaining the dataset's usefulness for analysis.
sbb-itb-5f36581
How to Add Anonymization to Your Form Workflows
Incorporating anonymization into your form workflows is essential for meeting GDPR requirements while still addressing your business objectives. Start by mapping out your data flow to ensure anonymization is applied effectively. If you're using a no-code, conversion-focused form builder like Reform, these best practices can be seamlessly integrated without compromising user experience. Then, conduct a thorough data audit to pinpoint exactly where anonymization is required.
Conducting a Data Audit
The first step is identifying direct identifiers (like names and emails) and indirect identifiers (such as job titles or locations) in your forms. This distinction is crucial because even if direct identifiers are removed, combining indirect identifiers can still lead to re-identification.
Evaluate the risk of re-identification using the motivated intruder test. The UK GDPR Recital 26 provides guidance:
"To determine whether a natural person is identifiable, account should be taken of all the means reasonably likely to be used, such as singling out, either by the controller or by another person to identify the natural person directly or indirectly."
This highlights the linkability risk, where information from different sources can be combined to identify someone.
Use a Data Protection Impact Assessment (DPIA) to structure your audit. A DPIA helps you identify risks to individuals’ rights, document mitigation measures, and create a defensible record for regulators. Assign a Senior Information Risk Owner (SIRO) to oversee the process and work closely with your Data Protection Officer (DPO).
Applying Anonymization Methods
Once risks are identified, choose anonymization techniques based on the type of data you're handling and how it will be used. Your approach will also depend on the release model - whether the data will be shared publicly (open release) or with a limited audience (restricted access).
For open releases, consider robust methods like differential privacy or synthetic data generation. For restricted access, you can use more detailed data but must implement safeguards such as confidentiality agreements, access controls, and staff training.
It's important to note that anonymization itself is considered a form of data processing under GDPR. The Information Commissioner’s Office (ICO) explains:
"If you can still identify people using additional information you hold separately, the data is not anonymised. It is pseudonymised and is still personal data."
This means you need a lawful basis for the anonymization process, not just for the original data collection. Choose techniques that ensure compliance while maintaining the data's usefulness for decision-making. Clearly document your purpose and ensure the method minimizes the risk of re-identification. Keep in mind that data might appear anonymous for internal use but could still be considered personal data if additional information is accessible - a concept known as the "spectrum of identifiability".
Documentation and Monitoring
After implementing anonymization techniques, thorough documentation and ongoing monitoring are critical for compliance. Proper documentation can protect your organization if regulators investigate your practices. According to the ICO:
"Organizations are less likely to face enforcement action if they can demonstrate a serious effort to comply and a genuine belief that the data was effectively anonymized."
Ensure all anonymization methods and testing outcomes are recorded in your Record of Processing Activities (ROPA) as required under GDPR Article 30. Update your privacy notices to explain - clearly and in plain language - why data is anonymized, the techniques used, and the safeguards in place.
Train your team on anonymization standards and schedule regular reviews to ensure your methods remain effective. The ICO advises:
"You should review your risk assessments and decision-making processes regularly."
As technology advances, new identification threats or increased computational power can undermine older anonymization methods. Stay updated on the latest developments and have a response plan ready in case of heightened risks due to security incidents or external data availability.
| Governance Area | Key Actions |
|---|---|
| Planning | Appoint a senior lead (SIRO) and define the purpose of anonymization |
| Risk Mitigation | Conduct a DPIA and document results of motivated intruder testing |
| Effectiveness | Monitor technological advancements and track new identification risks |
| Transparency | Update privacy notices and gather feedback from data subjects |
| Operations | Maintain ROPA and log staff training efforts |
Balancing Compliance and Data Usefulness
Striking the right balance between compliance and maintaining data's value is no small feat. You want to protect privacy without stripping away the insights that drive smarter business decisions. The challenge is ensuring your data remains actionable for analyzing trends, optimizing campaigns, and enriching leads - all while staying compliant with privacy regulations.
Keeping Data Useful After Anonymization
Even after anonymization, data can still play a valuable role in your marketing and sales strategies. Instead of zeroing in on individual-level tracking, focus on broader trends and aggregated insights. This approach allows you to fine-tune campaigns and understand customer behavior without the legal risks tied to personally identifiable information (PII).
Raveena Rani, International IP Counsel, highlights this balance perfectly:
"Anonymized data is a great approach to strike a balance between customer privacy and lead acquisition, which enables companies to analyze and develop insights without jeopardizing people's privacy."
Using anonymized data effectively can unlock insights like industry-wide form completion rates while ensuring compliance remains intact. It's important to remember that identifiability exists on a spectrum. Data is considered anonymous when the risk of re-identification is "sufficiently remote" based on the tools and methods likely to be used. This doesn’t mean eliminating every possible scenario of re-identification but reducing the risk to an acceptable level, depending on whether the data is for internal use or public sharing.
Trade-Offs in Anonymization Methods
Once you've safeguarded data utility, understanding the trade-offs between different anonymization techniques becomes crucial. Each method offers a unique balance between privacy, usefulness, and complexity. For example, pseudonymization methods like hashing or tokenization retain strong analytical value but still fall under GDPR's scope, requiring strict security measures. Meanwhile, aggregation provides stronger privacy protections but often sacrifices detailed insights.
| Technique | Re-identification Resistance | Data Utility | Complexity |
|---|---|---|---|
| Data Masking | Medium | High | Low |
| Generalization | High | Medium | Medium |
| Pseudonymization | Medium | High | Medium |
| Synthetic Data | Very High | Medium | High |
| Perturbation (Noise) | High | High | Medium |
| Aggregation | Very High | Low | Low |
A smart approach is to layer techniques. For instance, combining generalization (like turning exact birthdates into age ranges) with perturbation (adding random noise to numerical data) can enhance privacy without completely sacrificing analytical value. The key is to prioritize: focus on protecting data that poses the highest privacy risks while preserving the information that delivers the most business value. Regularly test your safeguards to ensure they remain effective.
Tools like Reform can help you apply these techniques strategically. By using features like conditional routing and selective lead enrichment, you can build anonymization into your processes right from the start, ensuring compliance without compromising on insights.
Conclusion
Anonymized data offers more than just regulatory compliance - it's a smart way to avoid GDPR penalties while still retaining valuable insights. When done properly, anonymization takes data completely out of GDPR's scope, easing the regulatory load. The key is to reduce the risk of re-identification to a "sufficiently remote" level.
The Information Commissioner's Office emphasizes this approach:
"If you don't need to use personal data to achieve your objectives, then you should assess whether you can use anonymous information instead."
This approach not only ensures long-term data usability beyond retention deadlines but also supports a proactive, privacy-focused design philosophy. It shows a commitment to protecting user trust and minimizing reputational risks.
However, as technology advances, anonymized data could potentially become identifiable in the future. That’s why it’s essential to regularly review your anonymization techniques. Be diligent about documenting your decisions and clearly differentiate between anonymization, which removes data from GDPR's scope, and pseudonymization, which does not.
To make this process easier, tools like Reform can incorporate these privacy measures directly into your workflows. By using features such as conditional routing and selective data collection, you can gather meaningful insights while safeguarding privacy. It’s a balanced approach - protecting user trust while reducing legal risks and driving growth.
FAQs
What steps can I take to ensure my data is fully anonymized under GDPR?
To ensure your data meets the GDPR requirements for anonymization, you need to implement strong technical and organizational practices that make re-identification nearly impossible. Key steps include:
- Removing direct identifiers such as names, phone numbers, or email addresses.
- Masking or encrypting sensitive details to protect individual information.
- Introducing noise or aggregating data to blur specific personal details.
You should also assess how likely it is for someone to identify individuals using the remaining data, available tools, and access permissions. When data is truly anonymized, it can no longer be tied to an individual, which places it outside the scope of GDPR regulations.
What’s the difference between anonymization and pseudonymization under GDPR?
Anonymization means permanently removing or changing personal identifiers so that the data can no longer be traced back to an individual. Once data is anonymized, it’s no longer classified as personal and is exempt from GDPR regulations.
Pseudonymization, however, works differently. It replaces personal identifiers with a key or alias, offering a layer of privacy. But since the data can still be re-identified if the key is available, it continues to fall under GDPR rules.
This distinction is vital for businesses striving to manage personal data responsibly while staying compliant with regulations.
How can I effectively anonymize form data to ensure GDPR compliance?
To anonymize form data in line with GDPR requirements, you can apply techniques such as masking or redacting identifiers, hashing or tokenization, and generalizing or aggregating data values. Other effective methods include adding random noise (like differential privacy) and removing direct personal identifiers.
These methods ensure sensitive data can't be linked back to individuals, helping to safeguard user privacy while minimizing compliance risks. The key lies in implementing these techniques correctly to maintain data security and avoid potential penalties.
Related Blog Posts
Get new content delivered straight to your inbox

The Response
Updates on the Reform platform, insights on optimizing conversion rates, and tips to craft forms that convert.
Drive real results with form optimizations
Tested across hundreds of experiments, our strategies deliver a 215% lift in qualified leads for B2B and SaaS companies.


.webp)