How Consent Management Systems Handle Third-Party Data Sharing
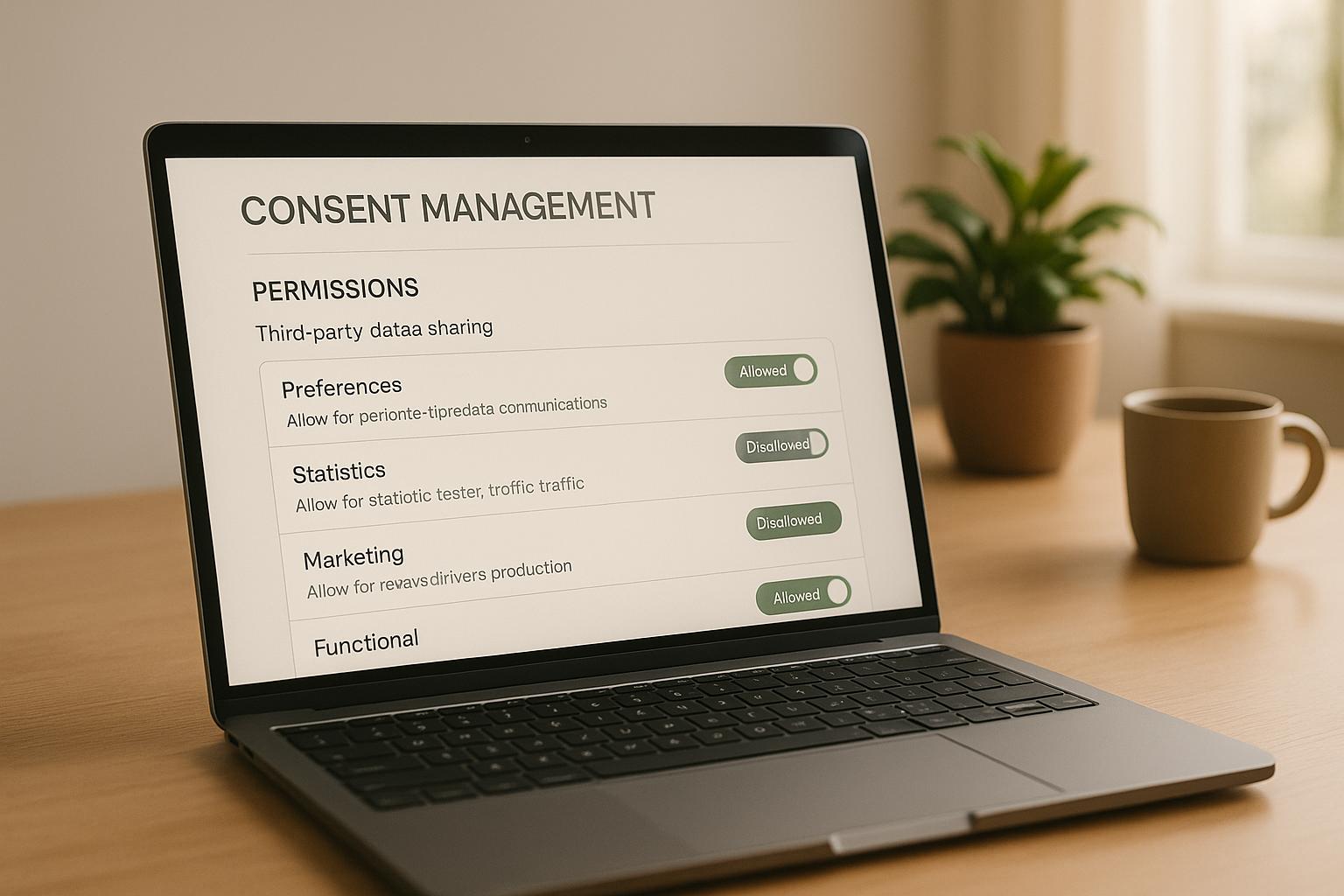
Consent management systems (CMS) are tools businesses use to manage user permissions for collecting and sharing personal data. They ensure compliance with privacy laws like GDPR and CCPA while giving users control over their data. These systems automate consent collection, storage, and updates, ensuring third-party tools respect user preferences.
Key takeaways:
- Why it matters: 51% of companies report third-party data breaches, and 75% of consumers avoid businesses they don't trust with data.
- Regulations: GDPR requires opt-in consent, while CCPA focuses on opt-out models. Non-compliance can result in hefty fines.
- How CMS works: They collect consent via banners, store it securely, and sync preferences with third-party tools like Google Analytics.
- Challenges: Managing third-party risks, excessive vendor access, and compliance complexity.
- Best practices: Use least-privilege access, AI tools, and regular vendor audits to improve security.
CMS platforms like Reform simplify compliance by integrating consent processes into user-friendly forms, helping businesses build trust while meeting legal requirements.
What is consent management?
Core Functions of Automated Consent Management Systems
Automated consent management systems play a crucial role in safeguarding user privacy and ensuring compliance with data regulations. They handle user permissions seamlessly across various touchpoints, providing transparency and control. Below, we explore how these systems collect, store, and manage consent while integrating with third-party tools.
How Systems Collect and Store User Consent
Consent management platforms are designed to capture user permissions in a clear and informed way. When users visit a website for the first time, banners or pop-ups appear to present options for data collection and sharing with third parties. These systems also allow for granular consent, enabling users to pick and choose specific types of data they are comfortable sharing.
For deeper control, many platforms include preference centers - dedicated spaces where users can adjust privacy settings. Here, visitors can see exactly what kind of data might be shared and with whom. This level of transparency helps users make decisions about categories like analytics tracking, marketing personalization, or social media integration.
To ensure these decisions are securely stored, systems rely on centralized repositories. Using first-party cookies and detailed audit logs, they record timestamps, user identifiers, and granted permissions. This means, for instance, if a user opts out of marketing cookies, that choice is immediately applied across all connected tools.
Research highlights that over 60% of users reject cookies when a clear "Reject All" button is available.
This secure and centralized storage is the backbone of effective consent lifecycle management.
Managing Consent Throughout Its Lifecycle
Once consent is collected, these systems ensure that user preferences are consistently respected. Real-time updates play a key role here. If a user changes their privacy settings - perhaps opting out of email marketing - the system immediately reflects these changes across all linked platforms, avoiding issues like unwanted emails continuing to arrive.
To make managing consent easy, many systems provide direct links to privacy dashboards. These links are often found in website footers or email signatures, offering users a straightforward way to review and adjust their settings.
The business benefits are clear: 89% of consumers are more loyal to brands that emphasize transparency in how they handle data.
Connecting with Third-Party Tools
Consent management systems don’t just handle internal processes - they also communicate user preferences to external tools. For example, if a user opts out of analytics tracking, platforms like Google Analytics will immediately stop collecting data. This seamless integration ensures that user decisions are respected across the board.
One of the most common scenarios involves marketing and analytics tools. These systems often sync with platforms such as Google Tag Manager, Meta Pixel, and CRMs to align consent signals automatically. They also feature dynamic blocking, which prevents unauthorized tracking by halting cookies and scripts until proper consent is granted.
For example, the New England Journal of Medicine achieved compliance and strengthened user trust by implementing a smooth integration process.
Some advanced consent systems even leverage AI to monitor compliance across all connected tools. This allows them to adjust data collection practices as privacy laws change, ensuring ongoing adherence to regulations. Acting as the central hub for privacy management, these systems ensure that every connected tool respects user choices, fostering trust among users and meeting regulatory requirements effectively.
Features That Ensure Compliance and Build User Trust
Beyond basic consent management, advanced features play a pivotal role in ensuring legal compliance and earning user trust. These tools work hand-in-hand to create transparent, user-centric experiences that meet regulatory standards while fostering stronger relationships with customers.
Detailed Consent Controls
Advanced consent systems go beyond the basic "accept all" or "reject all" options by offering users more control over their data. These granular settings allow individuals to decide exactly what they want to share. For example, a user might permit analytics tracking but block marketing cookies or agree to receive email communications while opting out of specific integrations. These controls typically cover areas like cookie management, analytics, and personalized advertising.
The key here is respecting user autonomy while still providing businesses with actionable insights. However, for these controls to be effective, they must be paired with interfaces that are clear, intuitive, and easy to navigate. This combination ensures transparency and empowers users to make informed decisions about their data.
Clear and Accessible User Interfaces
Designing user-friendly interfaces is crucial for earning trust and securing valid consent. Poorly designed interfaces - especially those using manipulative tactics like dark patterns - can not only erode trust but also lead to regulatory penalties. For instance, privacy regulators have invalidated consents obtained through confusing or misleading interfaces.
Effective consent interfaces prioritize balance and simplicity. They use clearly labeled opt-in and opt-out buttons, avoid technical jargon, and ensure users can easily revisit and modify their choices at any time. This approach not only builds trust but also strengthens compliance.
Research highlights that while 79% of consumers are concerned about their online privacy, only 32% take the time to read privacy terms before consenting. Additionally, 89% of consumers remain loyal to brands that prioritize transparency around data usage.
An intuitive interface is just one piece of the puzzle. Real-time compliance monitoring is another critical component.
Real-Time Compliance Monitoring and Reporting
Automated compliance monitoring helps businesses stay ahead of regulatory changes and adapt to user preference updates immediately. These systems continuously track consent statuses across all connected platforms, ensuring that user preferences are respected. For instance, if a user opts out of marketing emails, real-time monitoring ensures that no further emails are sent.
AI-driven tools enhance this process by analyzing compliance trends and predicting potential issues. Comprehensive audit logs document every interaction, including timestamps, user identifiers, and consent choices. This level of detail is invaluable during regulatory investigations. A notable example: in 2021, France's data protection authority issued fines of €150 million to Google and €60 million to Facebook for cookie consent violations.
Automated reporting takes this a step further, simplifying compliance management by generating audit-ready documents and dashboards. These tools provide stakeholders with a clear overview of consent activities and help businesses stay prepared for regulatory scrutiny. With projections estimating the global consent management platform market will hit $2.5 billion by 2032, and 73% of consumers expressing growing concerns about their data privacy, investing in advanced consent management features is a smart move for businesses aiming to thrive in a privacy-conscious world.
Challenges and Best Practices in Managing Third-Party Data Sharing
Managing third-party data sharing is more than a technical necessity - it’s a survival skill in today’s business landscape. With 98% of organizations experiencing breaches and nearly half attributing those breaches to third-party access, the stakes couldn’t be higher.
Common Challenges in Third-Party Data Sharing
The manufacturing sector is a prime example of how vulnerable industries can be. Last year, 42% of manufacturing organizations reported breaches tied to third-party access. These incidents often arise from weak vendor management practices, creating vulnerabilities that ripple through the entire data ecosystem.
One major issue? Excessive vendor privileges. A startling 35% of security incidents are linked to third parties being granted more access than they actually need. Adding to the problem, over half of organizations (54%) don’t evaluate the security and privacy practices of their third-party vendors before granting them access. This lack of due diligence leaves businesses exposed to risks they may not even be aware of.
Managing vendor relationships is another uphill battle. Security teams dedicate an average of 47 hours each week to analyzing third-party risks. As Dr. Larry Ponemon, Chairman of the Ponemon Institute, points out:
"This time investment reflects the complexity of vendor relationship management. Manufacturers lacking clear security strategies are more vulnerable."
Regulatory requirements further complicate the picture. Sixty-one percent of organizations identify regulatory complexity as their biggest challenge. Non-compliance isn’t just a theoretical risk - it’s costing businesses an average of $14.82 million in fines and penalties. Alarmingly, 43% of organizations don’t even maintain a complete inventory of third parties with network access, making it nearly impossible to manage risks effectively.
Best Practices for Effective Consent Management
Tackling these challenges requires a proactive and structured approach. Start by creating detailed vendor inventories and conducting thorough risk assessments before granting anyone access to your data.
Implement least privilege access principles and adopt a zero trust architecture. This means limiting third-party access to only what’s absolutely necessary and incorporating measures like continuous authentication, encryption, and activity monitoring.
AI-powered security tools can also play a significant role. These tools not only enhance threat detection but can also save organizations an average of $2.22 million per breach. Vendor contracts should include enforceable provisions for audits, incident response, and data recovery, while adhering to industry standards like ISO27001 or NIST800-53.
Ongoing oversight is critical. This includes real-time monitoring of vendor activities, regular evaluations of their data privacy and security controls, and the ability to revoke access immediately when needed. You can further reduce risk by employing data minimization strategies - sharing only the information vendors need for their tasks - and using tiered vendor management to prioritize oversight based on risk levels.
Don’t overlook the human element. Training staff on data security best practices ensures employees are equipped to handle third-party systems responsibly.
Feature Trade-Offs to Consider
Designing a robust third-party data sharing system often involves weighing different security models. For instance, Attribute-Based Access Control (ABAC) can achieve similar levels of security as Role-Based Access Control (RBAC) but with fewer data policies, making it a more efficient option. Similarly, integrated platforms offer streamlined security but may lack the granular control provided by standalone solutions. The right choice depends on your organization’s risk tolerance, regulatory requirements, and operational needs.
As Dr. Larry Ponemon aptly puts it:
"A comprehensive strategy forms the foundation of effective risk management."
sbb-itb-5f36581
Reform: Simplifying Consent Management for High-Conversion Lead Generation
With increasing challenges around third-party data sharing, Reform turns compliance into a competitive edge. This no-code form builder helps businesses meet consent management requirements while boosting lead generation, making data collection more efficient and conversion-friendly.
How Reform Handles Third-Party Data Sharing Compliance
Reform's multi-step forms and conditional routing are game-changers for consent management. Multi-step forms break the process into smaller, easy-to-follow steps, ensuring users clearly understand what they’re agreeing to while improving form completion rates.
Conditional routing tailors the consent process by displaying GDPR-specific options for users in the EU and CCPA options for Californians. This targeted approach keeps things relevant, avoiding unnecessary legal jargon for users outside these regions.
To further support compliance, Reform includes email validation and spam prevention. These features ensure the data collected is accurate and legitimate, reducing the risk of compliance issues later and simplifying tasks like honoring data deletion or modification requests. By combining these tools, Reform not only safeguards compliance but also fosters user trust and drives better conversions.
Building User Trust and Boosting Conversions with Reform
Trust is key when managing consent, and Reform’s design reflects that. As one industry expert puts it:
"Reform is what Typeform should have been: clean, native-feeling forms that are quick and easy to spin up. Reform does the job without a bunch of ceremony."
Reform’s professional, customizable interface helps build confidence, especially when collecting sensitive data. With no-code customization, you can align the forms perfectly with your brand’s style, creating a seamless experience that feels integrated rather than outsourced.
Key features like the "finish later" option and abandoned submission tracking are especially helpful for consent-heavy forms. Users can pause and return later if they need more time to review terms or policies, reducing form abandonment while respecting their decision-making process.
"I've been using Reform for a landing page contact form for the past couple of months - really loving it so far! Super clean product and great support."
Simplifying Compliance with Reform’s Audit Tools
Reform makes compliance audits hassle-free with real-time analytics and reporting. The platform tracks everything from form completion rates to user interactions, creating a detailed, audit-ready trail that regulators often require.
Its A/B testing feature lets you refine consent flows without compromising compliance. You can experiment with different ways of presenting privacy information or consent options, using data to strike the right balance between legal obligations and user experience.
Reform also integrates seamlessly with CRM and marketing tools, ensuring consent data stays consistent across systems. This eliminates the risks of compliance gaps caused by siloed or manually transferred data.
"When we're trying to build a new product the last thing we want to waste time on tedious work like a sign-up form. Reform was a super clean, easy to use solution at a very reasonable price."
For businesses with complex compliance needs, Reform’s headless forms and API capabilities offer additional flexibility. These tools allow technical teams to embed Reform’s features into custom applications while maintaining full control over data and user experiences.
Reform’s templates are designed to optimize conversions, featuring options like demo request forms, early access lists, and customer intake forms. These templates balance compliance with marketing goals, so businesses don’t have to choose between meeting legal standards and driving results.
Conclusion: Balancing Compliance and User Trust in Third-Party Data Sharing
Navigating third-party data sharing today demands a careful blend of strict compliance and genuine user trust - two cornerstones of modern business success. As regulations continue to evolve, companies must embrace consent management not just as a legal obligation but also as a way to stand out in the marketplace. Striking this balance between regulatory adherence and empowering users is shaping the future of consent management.
The idea that compliance and trust are at odds is outdated. In fact, they complement each other. Consider this: 78% of customers are more likely to share their data with companies they trust. Transparency, when done right, becomes a competitive edge rather than a chore. Leading businesses exemplify this by embedding Privacy by Design into their systems and conducting regular security checks.
This shift highlights the need for a forward-looking, tech-driven approach to data protection.
"Protecting data just enough to meet regulations is simply no longer safe enough, as evidenced by recent cyber-attacks on Snowflake, Ascension, Change Healthcare, and the users of MOVEit, to name a few. However, protecting data to the point in which its utility is diminished is not sufficient either. This is why the critical need to adopt PETs isn't just an option – it's a necessity that can truly transform industries."
– Regina Gray, COO of Karlsgate
With 84% of IT leaders acknowledging the need to overhaul data practices to meet new privacy laws, the outdated reactive approach to compliance no longer works.
Automated systems are stepping up to the challenge, combining compliance with user-friendly experiences to build trust. Tools like Reform turn consent management into a seamless process, making it feel natural rather than intrusive. For instance, over 60% of users reject cookies when they see a clear "Reject All" option. Reform addresses this by designing consent flows that respect user decisions while maintaining clarity and ease of use.
The stakes are high. Access control breaches account for 34% of all data breaches, underscoring why 72% of Americans support stricter regulations on data practices. People want their information protected - and they want more control over it.
Industry leaders continue to stress the importance of a unified strategy.
"In today's rapidly evolving regulatory landscape, a fragmented approach to data privacy and compliance is no longer sufficient. Data level tooling combined with manual consulting services creates a loss in data utility and privacy. Organizations that adopt a holistic strategy that seamlessly integrates technology end to end will reap the benefits: privacy by design principles, robust governance, and configurable compliance solutions and gain an early competitive advantage. At Integral, we've observed that companies implementing a comprehensive approach not only achieve better compliance outcomes but also greater value from their data-sharing initiatives. The key is to view compliance as an enabler of trusted, innovative data collaborations."
– Shubh Sinha, CEO of Integral
The future belongs to businesses that treat consent management as the foundation of sustainable data relationships. Platforms like Reform demonstrate how automated systems can go beyond reducing regulatory risks - they can foster trust, encouraging customers to share data that fuels personalization and growth. With 94% of consumers preferring brands that are upfront about their practices and 87% more likely to engage with transparent companies, user-controlled consent processes are no longer optional. In a world where 66% worry about how brands handle their personal data, transparency and trust are the keys to long-term success.
FAQs
How do consent management systems comply with GDPR and CCPA regulations?
How Do Consent Management Systems Support GDPR and CCPA Compliance?
Consent management systems play a key role in helping businesses meet the requirements of GDPR and CCPA, tailoring their features to each regulation's specific demands.
Under GDPR, companies are required to obtain consent that is explicit, informed, and freely given before collecting any personal data. Consent management systems make this easier by tracking, storing, and managing user consents. This ensures businesses can provide proof of compliance if questioned.
For CCPA, while explicit consent isn't always mandatory, companies must give users clear options to opt out of data sales and honor their choices. These systems streamline compliance by keeping detailed records, enabling opt-out functions, and ensuring transparency in how user data is used.
With tools like real-time consent tracking, audit logs, and user preference management, these platforms not only help businesses comply with regulations but also foster trust by showing a commitment to user privacy.
What challenges do businesses face with third-party data sharing, and how can they address them?
Managing third-party data sharing isn't without its hurdles. Companies often face issues like weak security measures from vendors, compliance challenges, and the looming threat of data breaches. Any of these can result in financial setbacks, legal troubles, and a tarnished reputation.
To tackle these risks, businesses need a clear plan. This includes performing regular checks on vendors, streamlining compliance efforts through automation, and leveraging AI-driven tools for real-time oversight. These strategies not only reduce risks but also help ensure compliance and strengthen trust with both users and partners.
How do consent management systems help businesses build trust and improve data sharing practices?
Consent management systems play a crucial role in helping businesses establish trust with their customers. They ensure open and honest communication about how personal data is collected, used, and shared. By securing explicit consent and adhering to privacy laws, these systems show respect for individuals' privacy rights, which builds both confidence and accountability.
Beyond compliance, these systems give users control over their personal information. They allow individuals to adjust or revoke consent whenever they choose. This level of control not only deepens trust but also encourages responsible data practices, minimizes the risk of violating regulations, and boosts overall user satisfaction.
Related posts
Get new content delivered straight to your inbox

The Response
Updates on the Reform platform, insights on optimizing conversion rates, and tips to craft forms that convert.
Drive real results with form optimizations
Tested across hundreds of experiments, our strategies deliver a 215% lift in qualified leads for B2B and SaaS companies.


.webp)








