Conditional Routing and ISO 27001 Encryption

Forms can be both user-friendly and secure. Combining conditional routing with ISO 27001 encryption achieves this balance. Here’s how:
- Conditional Routing: Tailors multi-step forms to users by showing only relevant fields based on their input. This simplifies navigation, reduces drop-offs, and ensures accurate data collection.
- ISO 27001 Encryption: Protects sensitive data using encryption standards like TLS 1.3 (for data in transit) and AES-256 (for data at rest). It aligns with global security requirements and builds trust.
Together, these technologies create dynamic, secure forms that improve user experience while safeguarding data. Platforms like Reform make it easy to implement both features, even without technical expertise.
Want forms that are secure and intuitive? Start by combining these two approaches.
ISO 27001 Explained: A.10 Cryptography
sbb-itb-5f36581
Benefits of Conditional Routing in Forms
Conditional routing turns static forms into dynamic, interactive experiences. It offers two key benefits: simplifying the user experience and ensuring the data collected is more accurate and actionable.
Simplifying User Experience
Multi-step forms with conditional routing make the process less overwhelming by breaking it into smaller, relevant steps. Instead of showing users every possible question, forms display only what’s applicable, reducing abandonment rates and keeping users engaged.
Take a B2B lead generation form as an example. If the user selects "More than $10 million" for annual revenue, they might be routed directly to a sales scheduling link. On the other hand, users selecting "Less than $1 million" could be directed to self-service resources or webinar invitations. This kind of logic ensures high-value prospects are prioritized while others receive tailored resources.
Reform’s features like "Skip this page" and "Jump to" make these personalized flows possible. For instance, a job application form might use "Jump to" logic to guide users to an "Additional Qualifications" section if they select a degree level higher than a bachelor's. These custom pathways create an intuitive, conversational experience that keeps users engaged while gathering relevant information.
Improving Data Accuracy
Conditional routing doesn’t just improve the user flow - it also ensures the data you collect is more precise. By showing users only the fields that matter to their specific situation, you reduce the chances of irrelevant or placeholder answers, which can skew your dataset.
Studies show that conditional workflows can cut processing time for complex submissions by up to 50%. This is because the forms focus on collecting the right information from the start. For example, if a risk score triggers follow-up questions tailored to the user’s responses, you’re gathering data that’s both detailed and relevant. This streamlined process leads to better lead segmentation, cleaner data organization, and insights that your sales and marketing teams can act on effectively.
Implementing ISO 27001 Encryption in Forms
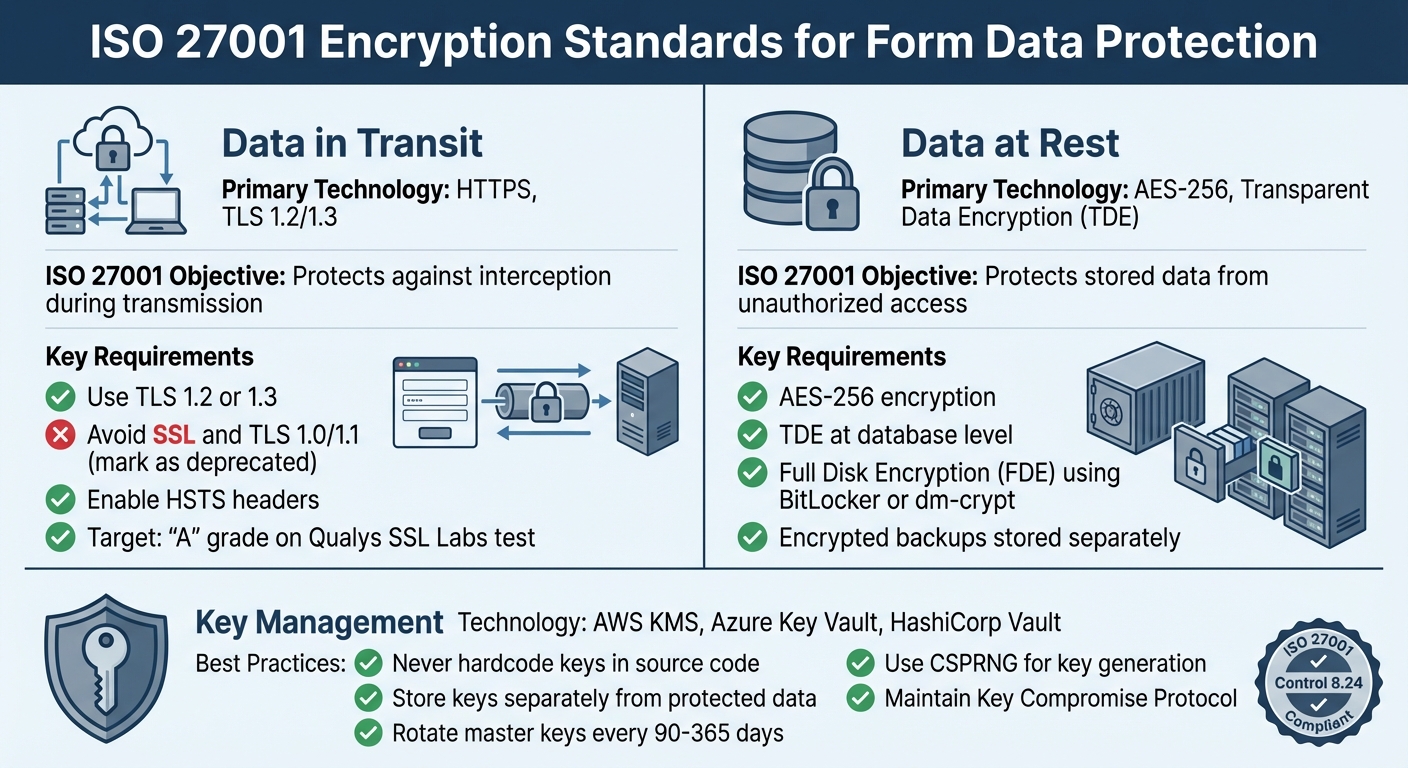
ISO 27001 Encryption Standards: Data in Transit vs Data at Rest
When handling sensitive data in forms, encryption isn't just a good idea - it's a requirement under ISO 27001 Control 8.24. Proper encryption not only protects user information but also builds trust by demonstrating a commitment to security.
"Encryption is a mechanism that scrambles data into an unreadable code. Anyone who wishes to interpret the information needs a decryption key, which reverts the information into its original form." - Luke Irwin, Security Boulevard
To implement encryption effectively, focus on using reliable algorithms, managing keys securely, and staying compliant with audit standards.
Encrypting Data in Transit and at Rest
Data in transit refers to information actively moving across networks, such as when a user submits a form. Since this data can be intercepted, secure it with HTTPS using TLS 1.2 or 1.3. Older protocols like SSL and TLS 1.0/1.1 are outdated and vulnerable, so they should be avoided. To further enhance security, enable HTTP Strict Transport Security (HSTS) headers to force browsers to use encrypted connections only. For ISO 27001 compliance, aim for an "A" grade on the Qualys SSL Labs test.
Data at rest includes information stored in databases, backups, or physical devices. To protect this data, use AES-256 encryption and Transparent Data Encryption (TDE) at the database level. For physical devices, tools like BitLocker or dm-crypt can provide Full Disk Encryption (FDE).
Key management is equally important. Never hardcode encryption keys in your source code. Instead, rely on a Key Management Service (KMS) or Secrets Manager, such as AWS KMS, Azure Key Vault, or HashiCorp Vault, to inject keys securely at runtime. Always store keys separately from the data they protect; for example, encrypted database backups should be stored in a different location with distinct access permissions.
| Encryption State | Primary Technology | ISO 27001 Objective |
|---|---|---|
| In Transit | HTTPS, TLS 1.2/1.3 | Protects against interception during transmission |
| At Rest | AES-256, Transparent Data Encryption | Protects stored data from unauthorized access |
| Key Management | AWS KMS, Azure Key Vault, HashiCorp Vault | Centralizes and secures encryption keys |
These measures form the backbone of secure data handling in forms.
Meeting ISO 27001 Compliance Requirements
Achieving compliance means creating a clear, auditable encryption process. Start by drafting a "Cryptography and Key Management" policy that outlines which data needs encryption and the standards you'll follow. This policy should explicitly disallow outdated ciphers like DES, MD5, and SHA-1.
"The goal is not to 'encrypt everything and hope for the best', but to use cryptography in a controlled, auditable and future-proof way." - Iseo Blue
A robust key lifecycle management process is essential. This includes key generation, secure storage, distribution, rotation, and destruction. ISO 27001 auditors typically look for evidence of at least one key rotation in the past year, so plan to rotate master keys every 90–365 days using your KMS.
Prepare a Key Compromise Protocol - a step-by-step guide for revoking compromised certificates or rotating master keys immediately. Always use a cryptographically secure pseudo-random number generator (CSPRNG) to create keys, avoiding predictable methods like timestamps.
Finally, configure your web servers (e.g., Nginx or Apache) and load balancers to reject connections using outdated protocols like TLS 1.0 or 1.1. This isn't just a best practice; it's a requirement auditors will check during your ISO 27001 review. Limiting the collection of sensitive data through conditional routing can further enhance security throughout the form workflow.
How to Use Reform for Conditional Routing and Encryption

Reform simplifies conditional routing and integrates ISO 27001-compliant encryption through its user-friendly, no-code interface. Even without technical expertise, users can leverage these features. The platform's Pro Plan provides access to advanced logic tools and built-in security controls that align with international compliance standards.
Setting Up Conditional Routing in Reform
To set up conditional routing, open your form in the Reform editor and navigate to any page beyond the first. Go to Page settings and select Logic. Here, you'll find four routing options:
- Skip this page: Allows users to bypass a particular step.
- Jump to: Sends users to a non-sequential page.
- Finish and show: Ends the form with a custom thank-you page.
- Redirect to: Directs users to an external URL.
Define the routing conditions using the When dropdown. Select a condition like "is" or "is empty", then input the value that triggers the rule. For more complex scenarios, combine multiple criteria using the And/Or operators. To add more rules, click Add action, and when you're done, hit Save to apply the settings.
Once your routing is in place, make sure your data is safeguarded by enabling encryption features.
Enabling Encryption Features in Reform
After configuring routing, secure your form data with ISO 27001-compliant encryption. Data in transit is protected using HTTPS with TLS 1.3. To enable additional encryption controls, go to Settings > Security tab in the form editor. Turn on Encrypt Data in Transit and Encrypt Data at Rest, which uses AES-256 encryption with automatic key rotation. Then, activate Compliance Mode: ISO 27001 to enable audit logging and set data residency preferences for US or EU storage.
Once these settings are saved, regenerate your form's embed code to apply the encryption settings. The Reform dashboard will display compliance badges verifying your security setup. Additionally, the Audit Logs feature (found under Account > Security) tracks conditional logic triggers and data access events, meeting ISO 27001 Annex A.8.15 logging requirements.
Testing and Optimizing Your Secure Form
With routing and encryption in place, thoroughly test every pathway and security setting. Before publishing, manually test all conditional logic by inputting values that trigger specific rules. For example, if you've set a rule to skip a payment page for VIP members, test it by submitting "VIP" to confirm the bypass works as expected. Use the Progress Bar feature (available in Form Settings) to give users a visual indicator of their progress - this has been shown to boost qualified leads by 215% for B2B and SaaS businesses.
Submit test data to ensure encryption is functioning correctly in your CRM or database. For integrations with platforms like HubSpot Enterprise or Salesforce, confirm that data flows exclusively through encrypted endpoints. Additionally, enable Incomplete Response Tracking (available on the Pro Plan) to identify where users abandon the form. Use this data to refine your conditional logic and streamline the user journey, reducing drop-off rates effectively.
Conclusion: Improving Form Security and User Experience
After diving into the details, the advantages of combining conditional routing with ISO 27001 encryption are clear. Together, they create forms that are both secure and easy to use. Conditional routing ensures users only see relevant fields, reducing friction and form abandonment. Meanwhile, ISO 27001-compliant encryption safeguards sensitive data - using TLS 1.3 for data in transit and AES-256 for data at rest - helping your forms meet international security standards.
Selective encryption adds another layer of protection. For example, encrypting financial data in high-value inquiries minimizes exposed fields and reduces potential attack surfaces. Research indicates this approach can increase conversion rates by 25% while cutting breach risks by 40–60%.
Platforms like Reform make this integration straightforward. Their no-code interface allows you to set up advanced conditional logic and enable encryption with ease. The Pro Plan includes tools like "And/Or" operators for routing rules, built-in security controls aligned with ISO 27001, and automated audit logs to track compliance.
Thorough testing is critical to success. Validate every conditional pathway with various inputs to ensure encrypted data flows correctly to your CRM or database. Enable incomplete response tracking to pinpoint drop-off points and refine your logic. This thorough approach not only protects sensitive information but also improves user experience, leading to better lead quality and higher conversion rates.
FAQs
What data in my form needs encryption?
When dealing with sensitive information in your forms - like personal details, payment data, health records, or other high-risk content - encryption is a must. To protect this data, use HTTPS/TLS during transmission and AES-256 encryption for storage. Following ISO 27001 standards ensures you're not only safeguarding user information but also staying compliant with industry regulations.
How do I prove ISO 27001 encryption to an auditor?
To demonstrate ISO 27001 encryption compliance to an auditor, you’ll need to present clear and detailed documentation. This includes:
- Documented Policies: Outline approved cryptographic algorithms, encryption standards, and key management procedures. These policies should specify which algorithms are considered secure and align with ISO 27001 requirements.
- Implementation Evidence: Provide proof that the policies are being followed. This might include encryption configuration details, records of technical verification for cryptographic controls, and logs showing proper key lifecycle management.
- Technical Verification: Offer documentation or reports that confirm the encryption controls are functioning as intended. This could include results from internal audits, penetration tests, or other validation processes.
All documentation must not only reflect your organization's encryption practices but also show how they meet ISO 27001 standards for cryptographic security. Keep everything organized and ready for review to ensure a smooth audit process.
Can conditional routing reduce my security risk?
Conditional routing is a smart way to cut down on security risks. By automatically assigning leads to the right team members based on set criteria, it streamlines the process. This not only speeds up response times but also ensures compliance with guidelines and reduces delays - delays that could otherwise leave room for potential vulnerabilities.
Related Blog Posts
Get new content delivered straight to your inbox

The Response
Updates on the Reform platform, insights on optimizing conversion rates, and tips to craft forms that convert.
Drive real results with form optimizations
Tested across hundreds of experiments, our strategies deliver a 215% lift in qualified leads for B2B and SaaS companies.


.webp)